
Phishing Analysis
Detailed analysis of captured phishing page
95
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: VirtualPA SERVICES
- • Threat: Phishing for personal information using a fake job application form.
- • Target: Job seekers interested in VirtualPA SERVICES.
- • Method: Tricking users into signing in or submitting sensitive information on a Google Docs form with a vague and suspiciously attractive job offer.
- • Exfil: Data likely sent to the attacker's email or another system for data harvesting; formResponse.
- • Indicators: Unofficial Google Docs form, vague job description, unusually high pay for little work, request for donation, and requests for a login to continue with the application process.
- • Risk: HIGH - Potential for credential theft and identity theft.
⚠ Risk Factors
- Brand impersonation of VirtualPA SERVICES on non-official domain
- Contains 1 credential harvesting form(s)
- JavaScript obfuscation detected (7 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
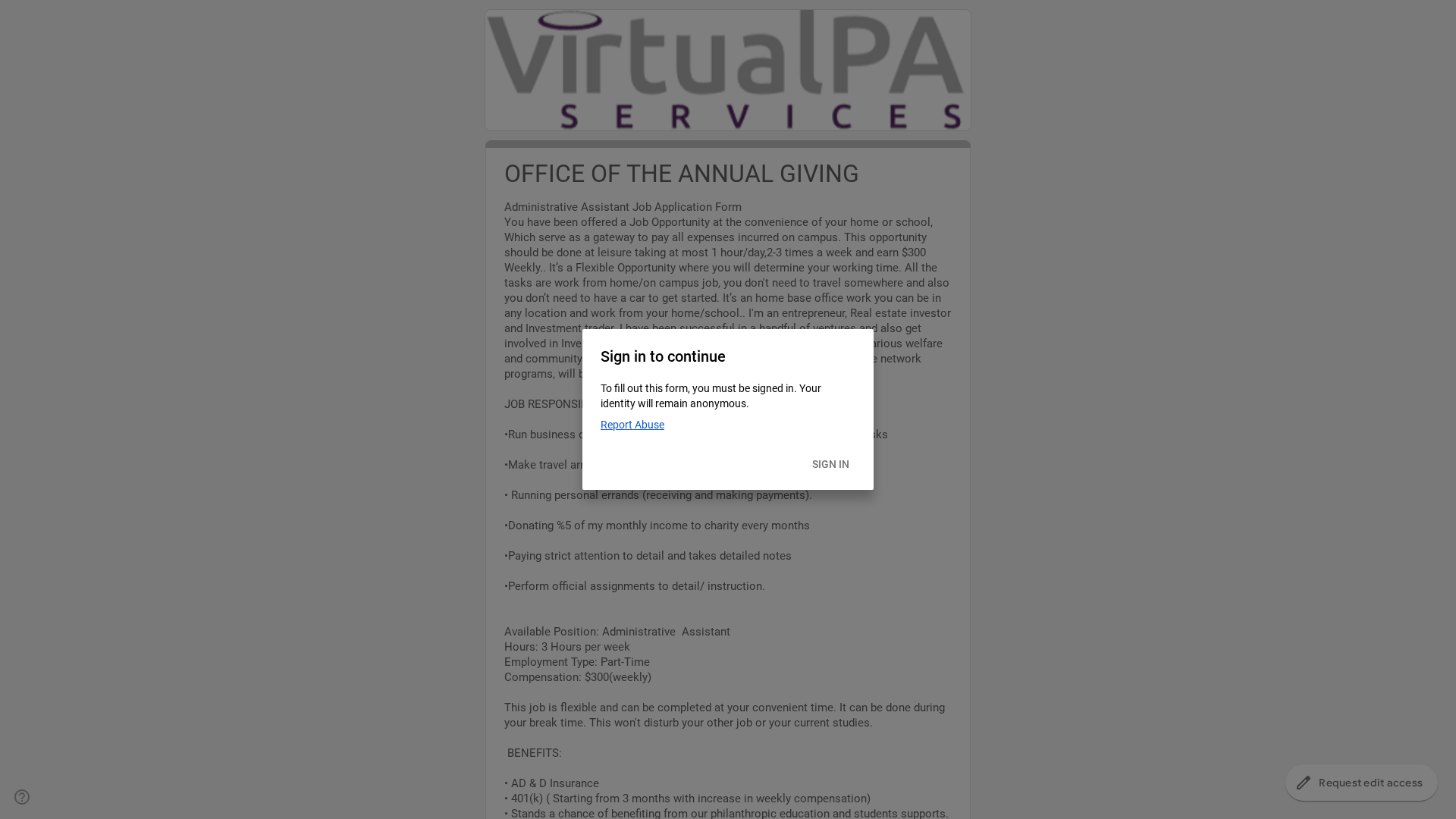
Detection Info
https://docs.google.com/forms/d/1ZrJdSKe4SJ2QUAPcfx-m1ZhXfNnuoI-6GU7EKFxWT1Q/viewform?edit_requested=true
Detected Brand
VirtualPA SERVICES
Country
International
Confidence
100%
HTTP Status
200
Report ID
06065a61-4cc…
Analyzed
2026-01-09 22:22
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T144F2E8377111BC3706174AC0B9AA6B4F32A7D31ED91B20A006FC27E41BFAD95F927619 |
|
CONTENT
ssdeep
|
384:s1F+G+6jm9ZUGLpO9m9ZUGLu6SOBfREWYIraGlsQwHJQQN8tQ/Na/1TGv2zwYuYZ:1hSm+mJSOBfROqsYPhac/56CtKfrCyrA |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
996666cc993966cc |
|
VISUAL
aHash
|
0000001818000800 |
|
VISUAL
dHash
|
040c0cb2b2081818 |
|
VISUAL
wHash
|
c0c0c4dcfceccc4d |
|
VISUAL
colorHash
|
07000c00040 |
|
VISUAL
cropResistant
|
a2d8b6aea8a280a2,040c0cb2b2081818 |
Code Analysis
Risk Score
95/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Banking
🎣 Personal Info
🔬 Threat Analysis Report
• Threat: Phishing for personal information using a fake job application form.
• Target: Job seekers interested in VirtualPA SERVICES.
• Method: Tricking users into signing in or submitting sensitive information on a Google Docs form with a vague and suspiciously attractive job offer.
• Exfil: Data likely sent to the attacker's email or another system for data harvesting; formResponse.
• Indicators: Unofficial Google Docs form, vague job description, unusually high pay for little work, request for donation, and requests for a login to continue with the application process.
• Risk: HIGH - Potential for credential theft and identity theft.
🔐 Credential Harvesting Forms
🔒 Obfuscation Detected
- atob
- eval
- fromCharCode
- unescape
- hex_escape
- unicode_escape
- base64_strings
Scan History for docs.google.com
Found 10 other scans for this domain
-
https://docs.google.com/presentation/d/e/2PACX-1vS...
https://docs.google.com/presentation/d/e/2PACX-1vT...
https://docs.google.com/document/d/e/2PACX-1vTh3iy...
https://docs.google.com/presentation/d/e/2PACX-1vS...
https://docs.google.com/forms/d/e/1FAIpQLSdMQ4frGs...
https://docs.google.com/presentation/d/e/2PACX-1vQ...
https://docs.google.com/forms/d/1qUV0ZKLYHGW_4y4Pf...
https://docs.google.com/forms/d/e/1FAIpQLSdrYyw_8J...
https://docs.google.com/forms/d/e/1FAIpQLSdbKfmfqZ...
https://docs.google.com/presentation/d/e/2PACX-1vS...