
Phishing Analysis
Detailed analysis of captured phishing page
95
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: ActiveCampaign
⚠ Risk Factors
- Brand impersonation of ActiveCampaign on non-official domain
- Contains 5 form(s) with JavaScript submission
- JavaScript obfuscation detected (7 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
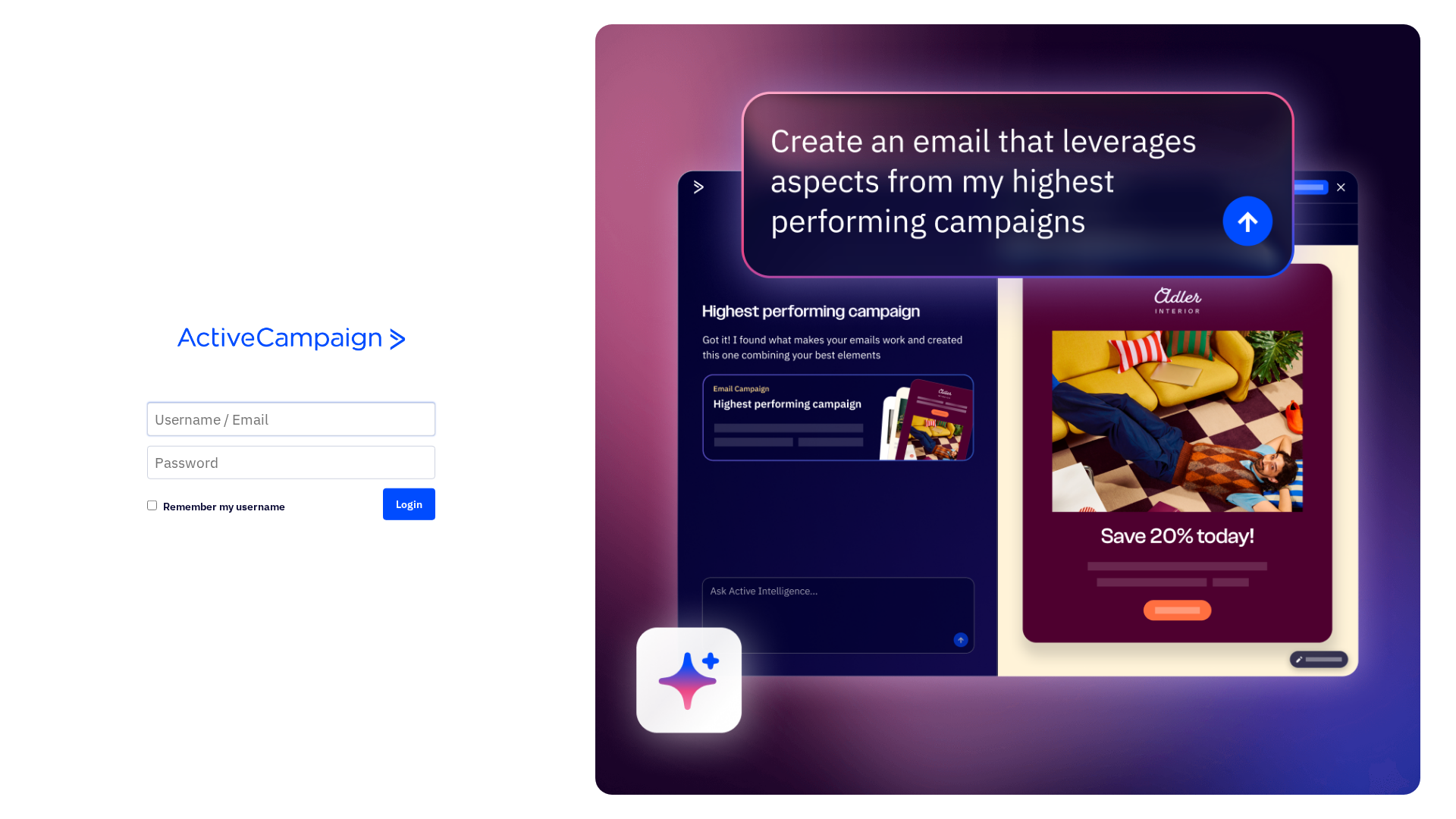
Detection Info
https://davisroberto480.activehosted.com/admin/archived_user.php
Detected Brand
ActiveCampaign
Country
USA
Confidence
100%
HTTP Status
200
Report ID
0c5afb4f-b11…
Analyzed
2026-01-09 00:15
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T121816320C4374D7A317DB1E4EAA53B1994C7C707CB812BE492B4432ECAECEC9AC67495 |
|
CONTENT
ssdeep
|
96:nEaoB/Bp9VS9NiJsUW23Jxj3qwElFmlfjRIbVlmd7tZMTgYFb3:ToB/Bp989NiJsnOjWmnYp |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
e65b992c998caa9c |
|
VISUAL
aHash
|
f0e0e0e0e0e0f0e0 |
|
VISUAL
dHash
|
41414d4f0d0d454d |
|
VISUAL
wHash
|
f0f0f0f0e0e0f1f1 |
|
VISUAL
colorHash
|
0e000680000 |
|
VISUAL
cropResistant
|
41414d4f0d0d454d,3749711d55697331,c7a7b3bc1eceecf1,c486d68e8edab0f8,0002527c76533ca0 |
Code Analysis
Risk Score
95/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Banking
🎣 Personal Info
🔐 Credential Harvesting Forms
🔒 Obfuscation Detected
- atob
- eval
- fromCharCode
- unescape
- hex_escape
- unicode_escape
- base64_strings
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
ActiveCampaign
https://rayjanikowski7157914.activehosted.com/admin/archived...
Jan 09, 2026
ActiveCampaign
https://rayjanikowski7199997.activehosted.com/admin/archived...
Jan 09, 2026
ActiveCampaign
https://bobmcllane61709.activehosted.com/admin/archived_user...
Jan 09, 2026
ActiveCampaign
https://joescamp24160.activehosted.com/admin/archived_user.p...
Jan 08, 2026
ActiveCampaign
https://dk11863350763.activehosted.com/admin/archived_user.p...
Jan 08, 2026