
Phishing Analysis
Detailed analysis of captured phishing page
78
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: Microsoft
- • Threat: Credential harvesting phishing kit
- • Target: Microsoft users in Israel
- • Method: Fake login form stealing email and password
- • Exfil: Potential data exfiltration via obfuscated JavaScript
- • Indicators: Domain mismatch, obfuscation, non-official domain
- • Risk: HIGH - Immediate credential theft
⚠ Risk Factors
- Brand impersonation of Microsoft on non-official domain
- Contains 1 credential harvesting form(s)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
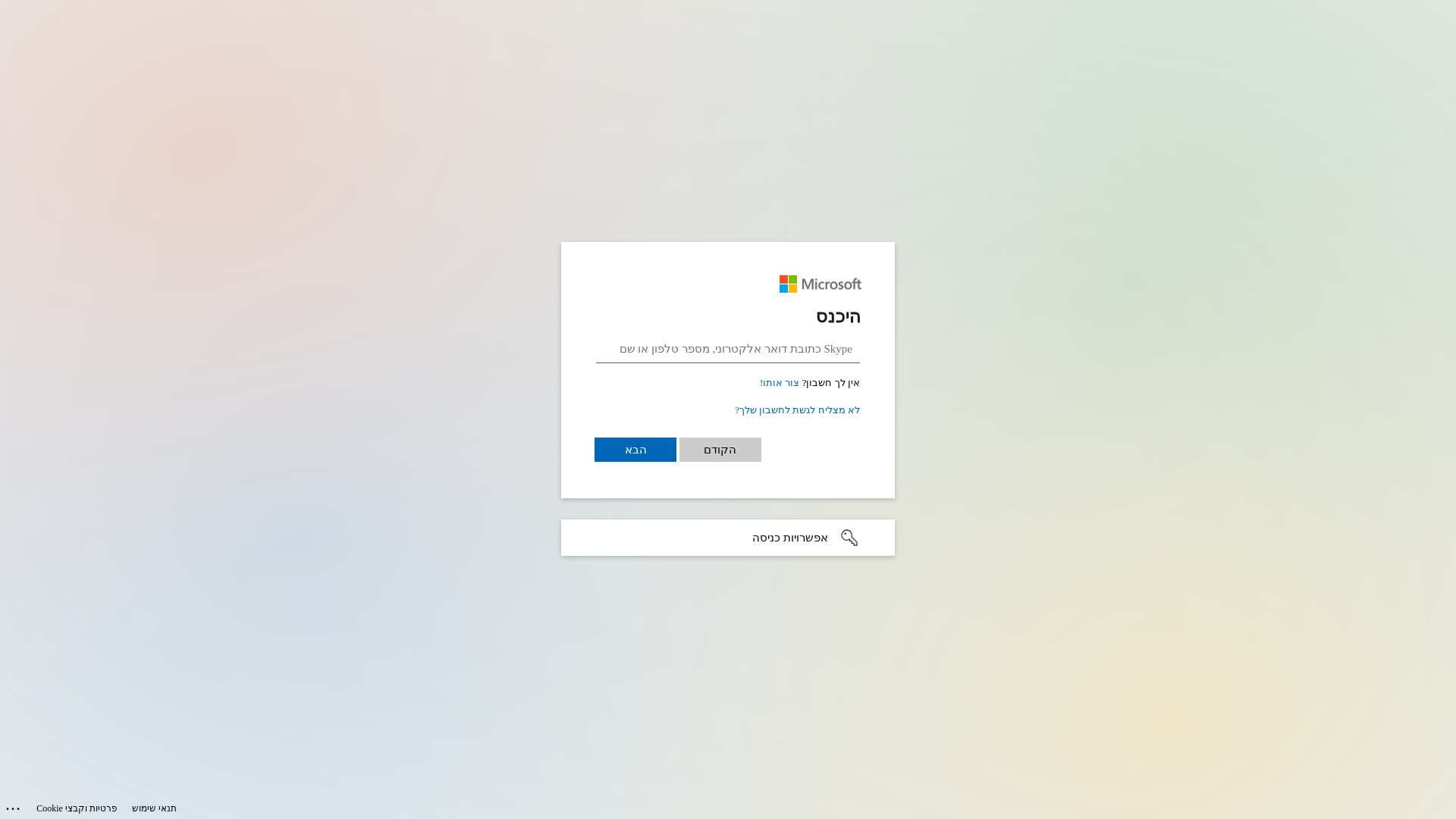
Visual Capture
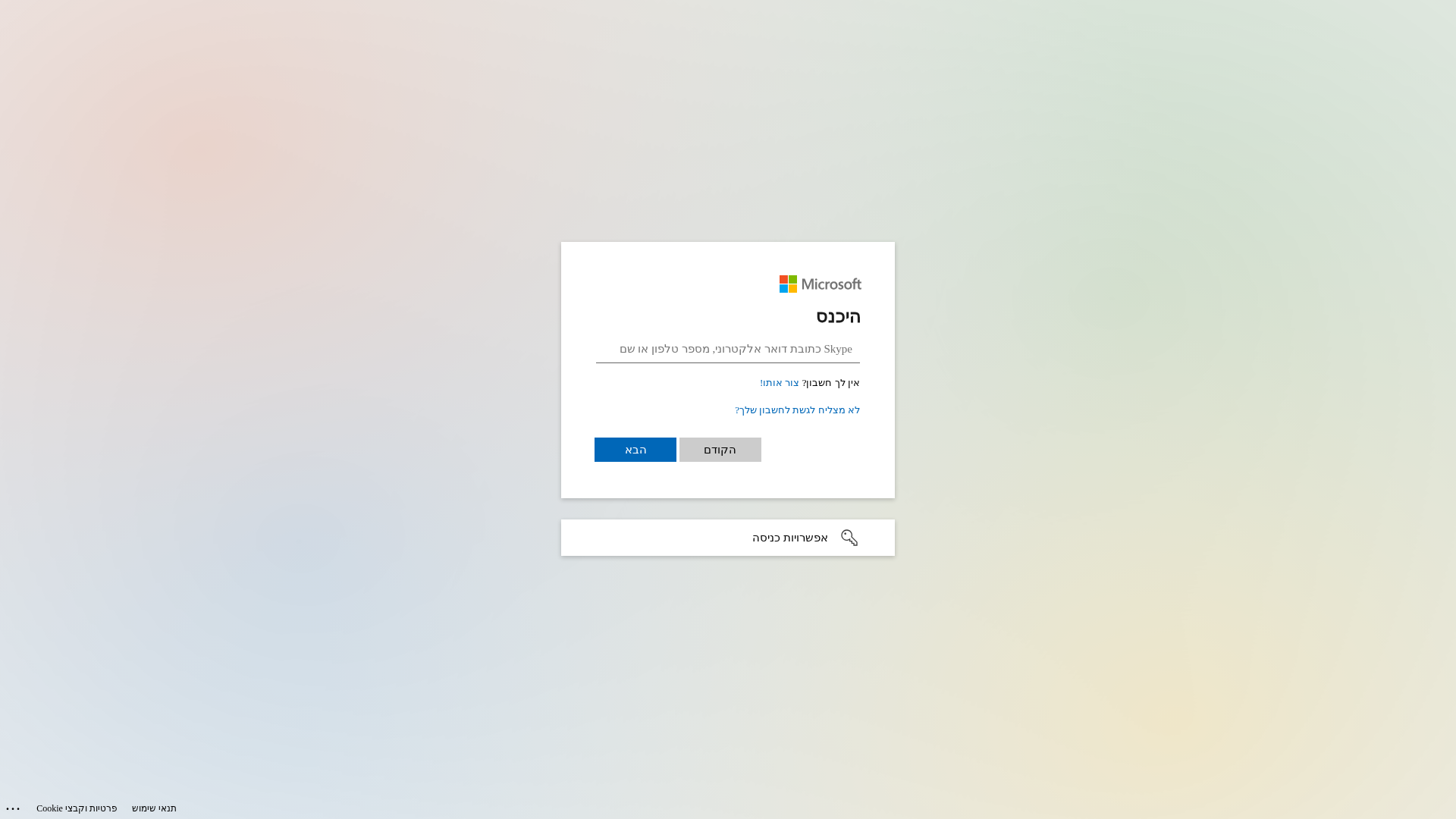
Detection Info
https://notifyhubss.net/k949b93007b44a44ec1934c2bbax6adb6612.html
Detected Brand
Microsoft
Country
Israel
Confidence
100%
HTTP Status
200
Report ID
0f8ec8a0-bfb…
Analyzed
2026-01-11 13:09
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T1ACD1317060C09D3712D3D6D8B7B5A70B3785C301DE8766AA97E4C38D4EEBDA1CC19291 |
|
CONTENT
ssdeep
|
96:6W9GQbeu0nPK/AmvUAK5KndPsb+vNR1j7fEAE9Nlt8dSsTioS4Dz5Q2GAMFJf:zBbMb8Rh7S9NAVDz5NEnf |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
9d486633d9cccc33 |
|
VISUAL
aHash
|
180018181d1f0f1f |
|
VISUAL
dHash
|
716131337b327d79 |
|
VISUAL
wHash
|
191818181f1f1fff |
|
VISUAL
colorHash
|
07000000180 |
|
VISUAL
cropResistant
|
716131337b327d79 |
Code Analysis
Risk Score
78/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🔬 Threat Analysis Report
• Threat: Credential harvesting phishing kit
• Target: Microsoft users in Israel
• Method: Fake login form stealing email and password
• Exfil: Potential data exfiltration via obfuscated JavaScript
• Indicators: Domain mismatch, obfuscation, non-official domain
• Risk: HIGH - Immediate credential theft
🔒 Obfuscation Detected
- atob
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
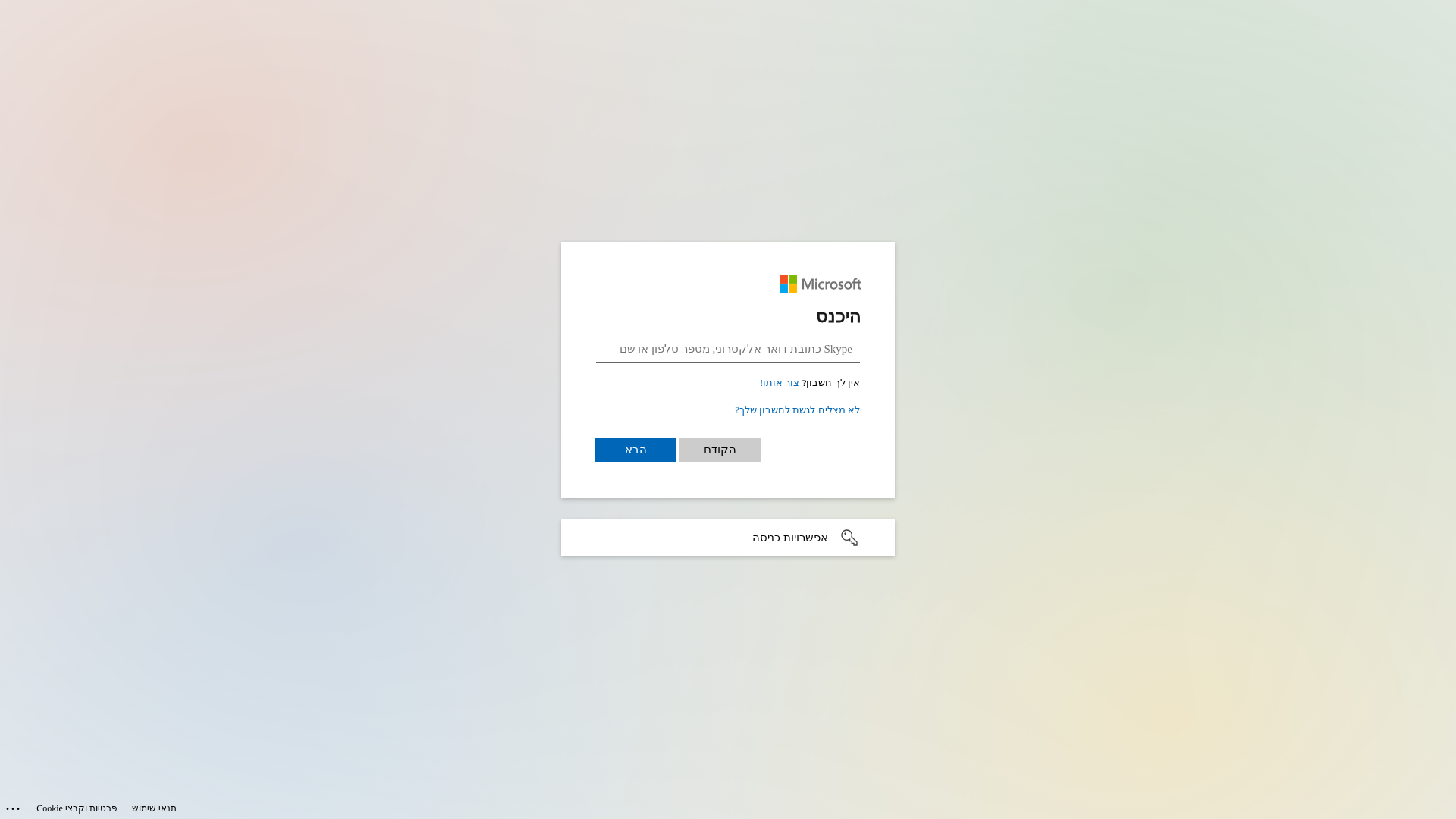
Microsoft
https://notifyhubss.net/13a6a40855506d481cgb8da4fca0007cae1b...
Jan 11, 2026
No screenshot
Microsoft
https://netfimarketing.com/t17b96992t0e77403fab4c69635se7606...
Jan 11, 2026
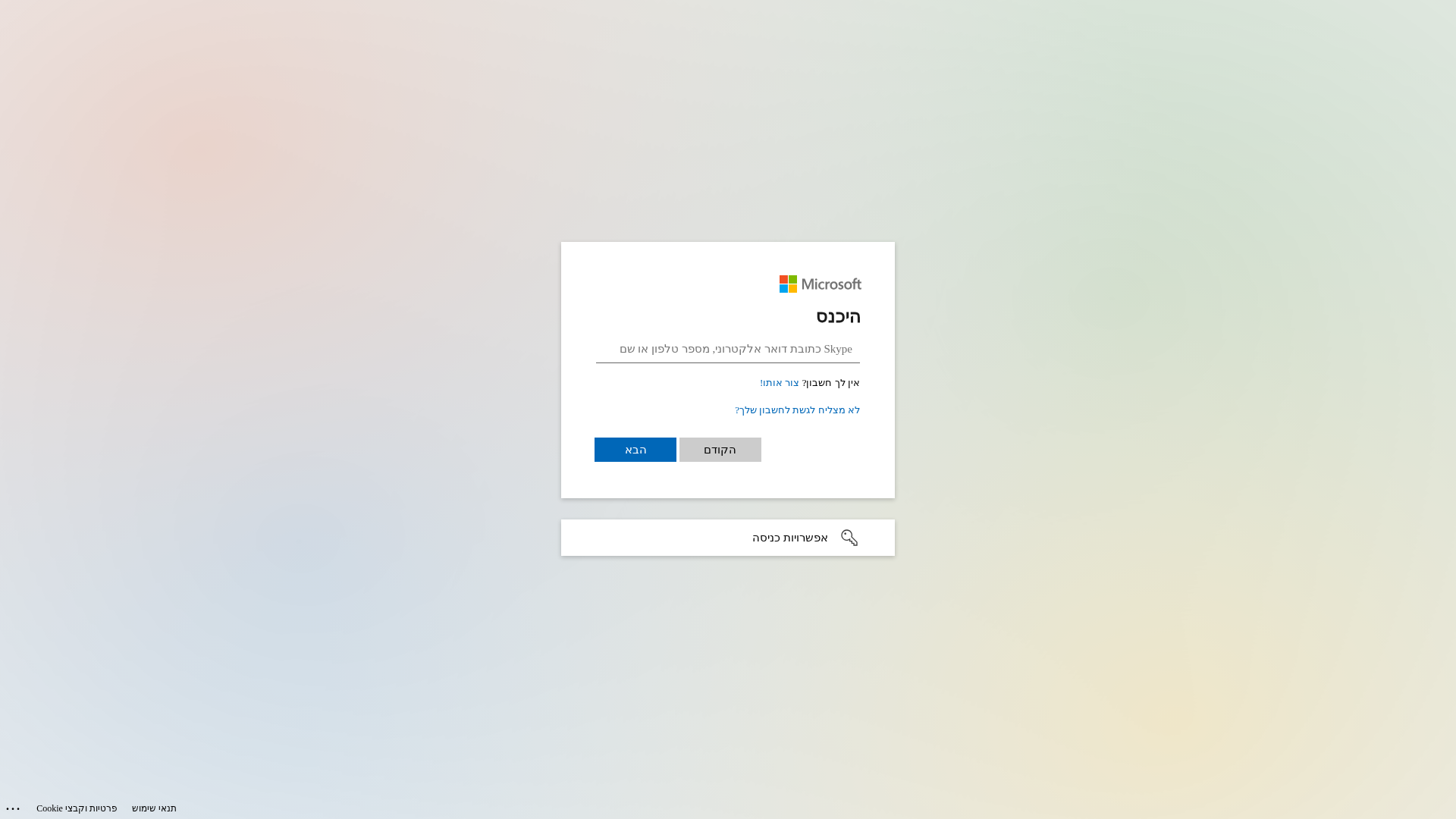
Microsoft
https://notifyhubss.net/164393ca05179d4e85g99238f18084a1d1cf...
Jan 11, 2026
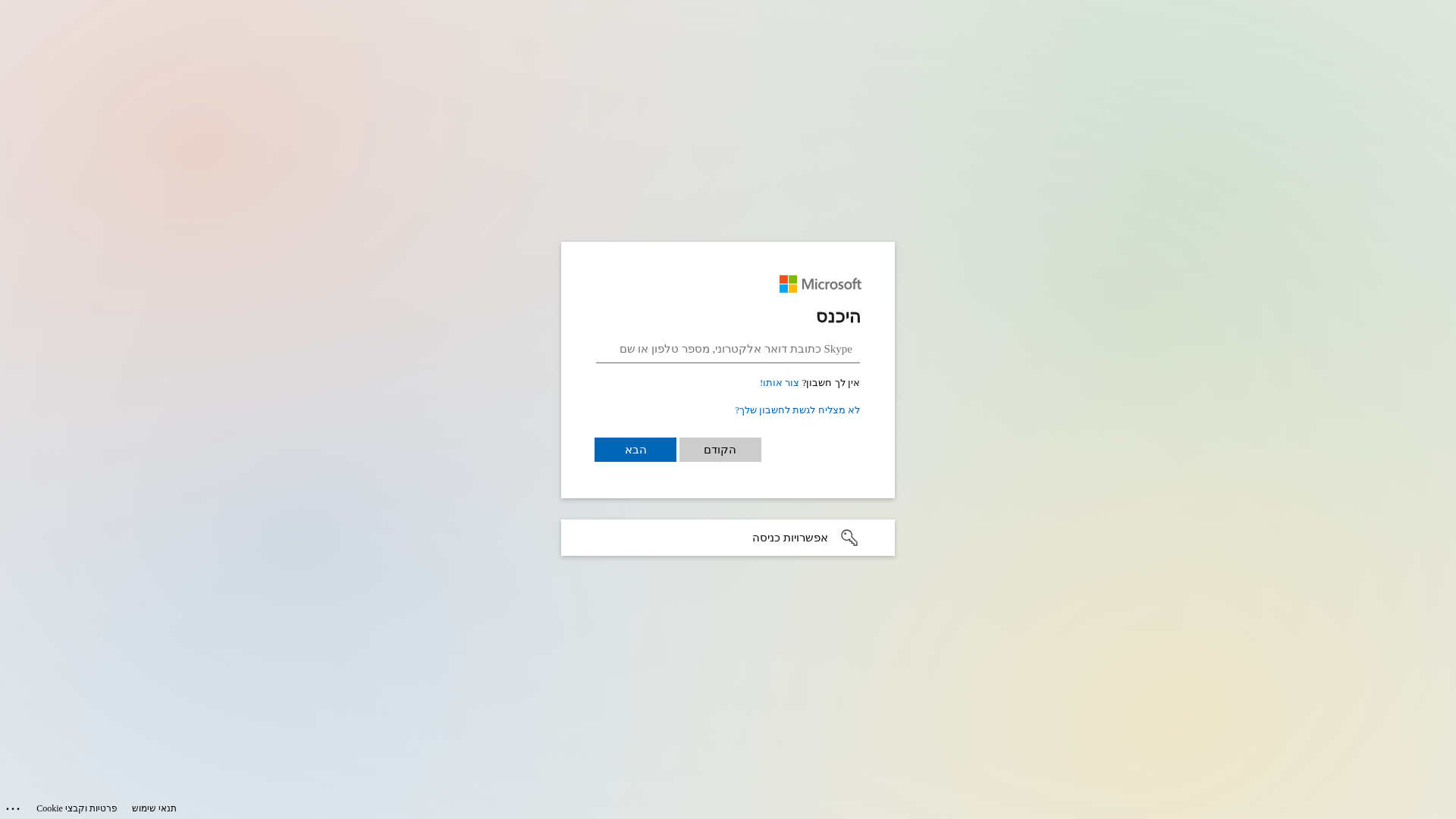
Microsoft
https://datagivers.com/57bb55786e18614f266bf44132fq0f5eb969....
Jan 10, 2026
Microsoft
https://datagivers.com/f89269ef6kb0f94aefz89226951sc5989905....
Jan 10, 2026
Scan History for notifyhubss.net
Found 10 other scans for this domain
-
https://notifyhubss.net/13a6a40855506d481cgb8da4fc...
https://notifyhubss.net/164393ca05179d4e85g99238f1...
https://notifyhubss.net/k70bd5a53738d94bcc194a13f9...
https://notifyhubss.net/k269d5d807202f4f3c1871811f...
https://notifyhubss.net/z6970aeb1r6d3846b908b29592...
https://notifyhubss.net/k418e7afb7b9b64a5e1a206268...
https://notifyhubss.net/k46fc05327515c4988192f157b...
https://notifyhubss.net/k750ec9a97a85d4ded1ab493a0...
http://notifyhubss.net/za4e6325dr863b470d0b6570bc0...
https://notifyhubss.net/z33388c39r46f4410f0ad3df30...