
Phishing Analysis
Detailed analysis of captured phishing page
Visual Capture
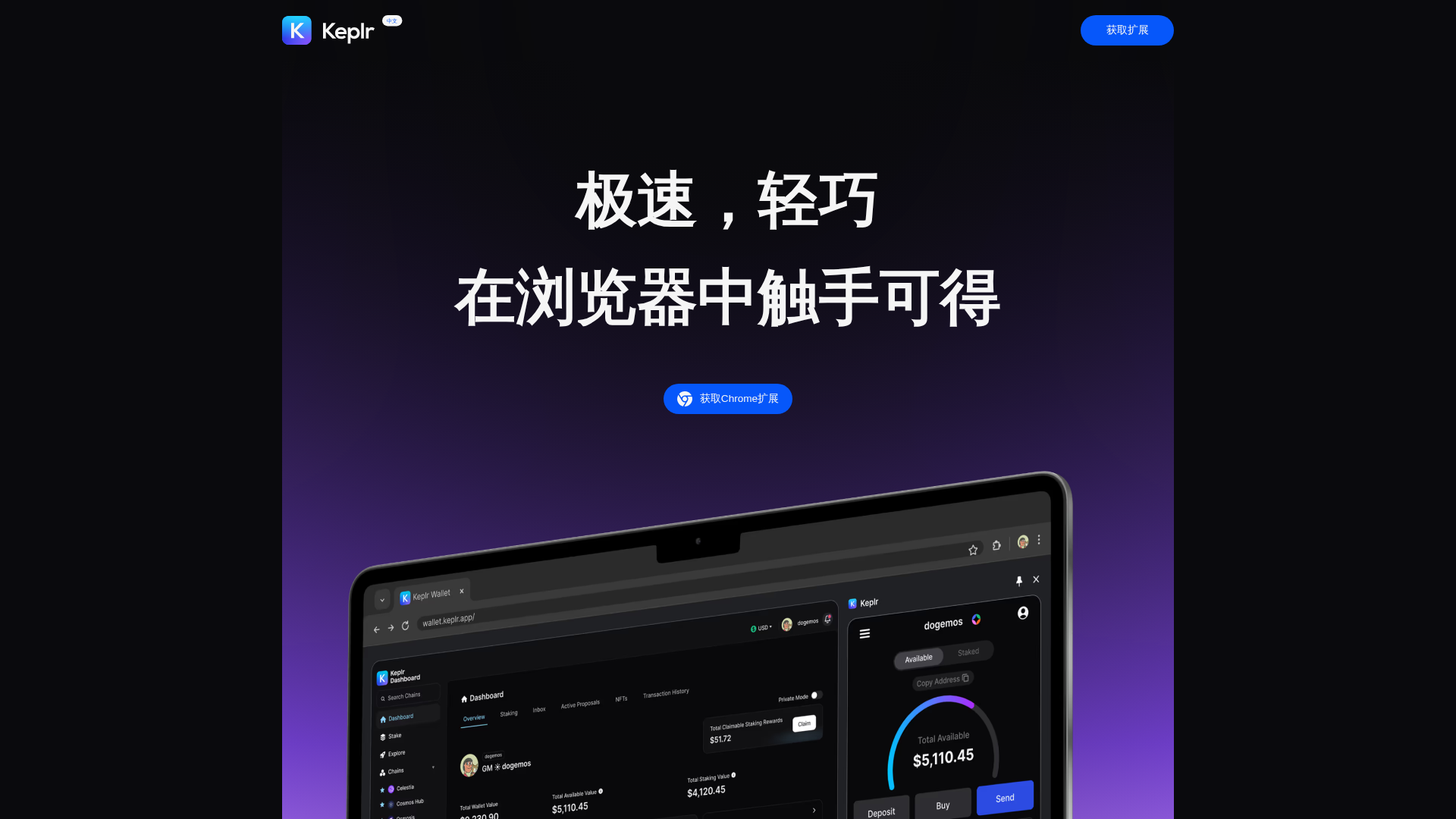
Detection Info
https://keplr.cn
Detected Brand
Keplr
Country
China
Confidence
90%
HTTP Status
200
Report ID
1b57878d-62d…
Analyzed
2026-01-11 08:31
Final URL (after redirects)
https://keplr.cn/
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T102C1DAE7D3C4A59A4607D3E4EE52701CB39B24F9FE61820C82E8559867A4AFECC539C1 |
|
CONTENT
ssdeep
|
96:nS7VBVPreC6RbI2j/wNUEb0gJuA9DUV+cgGpfjWeHTFz6:OVPrylcnb0+NPcjpfjZ16 |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
944c316333c796ed |
|
VISUAL
aHash
|
00183c3c7e7e6666 |
|
VISUAL
dHash
|
ccb2f0f0d4ccd4dc |
|
VISUAL
wHash
|
02183c3c7e7e666e |
|
VISUAL
colorHash
|
30000c00008 |
|
VISUAL
cropResistant
|
ccb2f0f0d4ccd4dc |
Code Analysis
Threat Level
ALTO
⚠️ Phishing Confirmed
🔬 Threat Analysis Report
• Threat: Credential harvesting phishing kit
• Target: Keplr users in China
• Method: Fake login form stealing wallet credentials
• Exfil: Data sent to unknown server
• Indicators: Domain mismatch, new domain, mimicked branding
• Risk: HIGH - Immediate credential theft