Phishing Analysis
Detailed analysis of captured phishing page
70
Risk Score
High Risk
Threat Level: ALTO
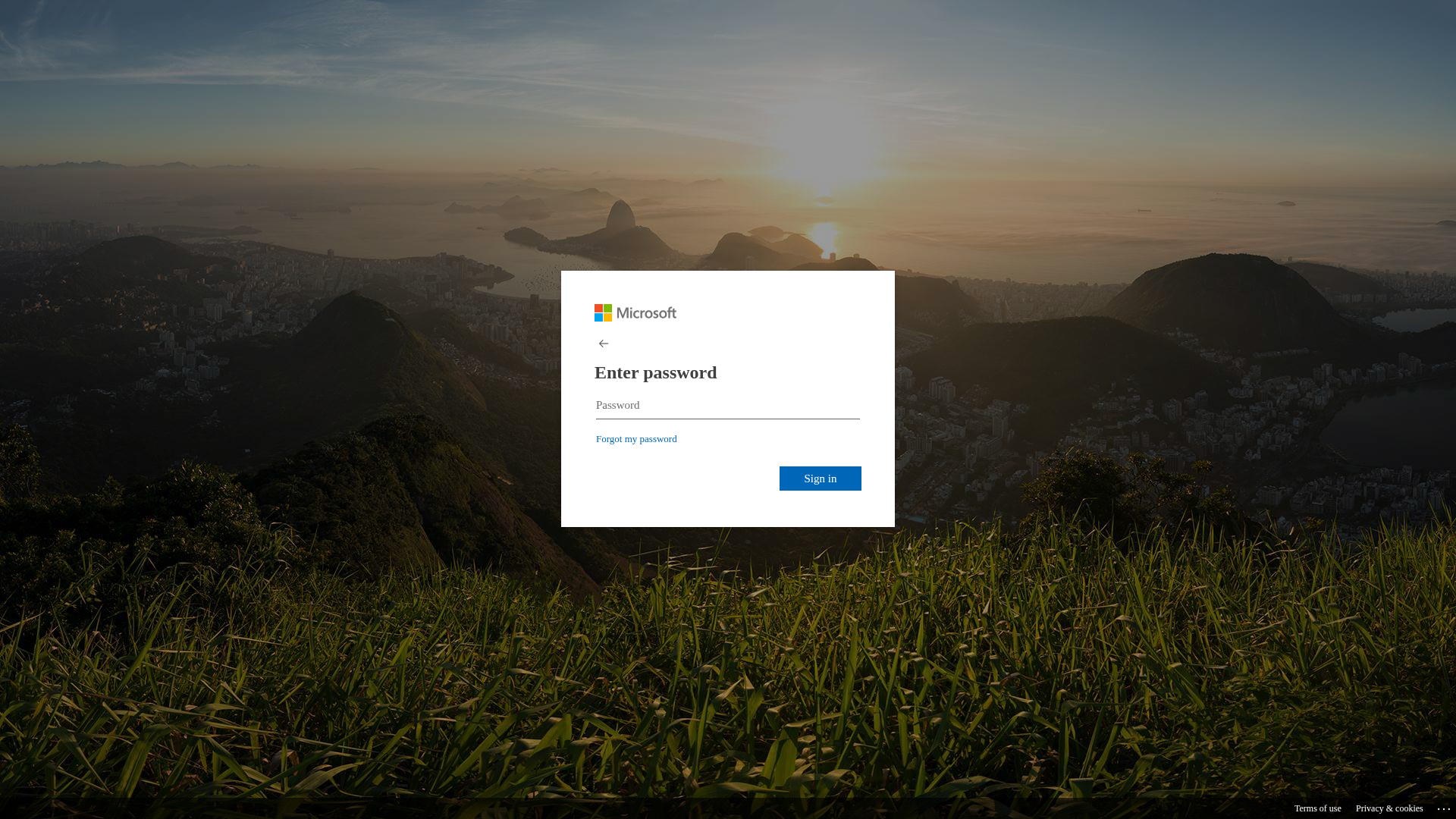
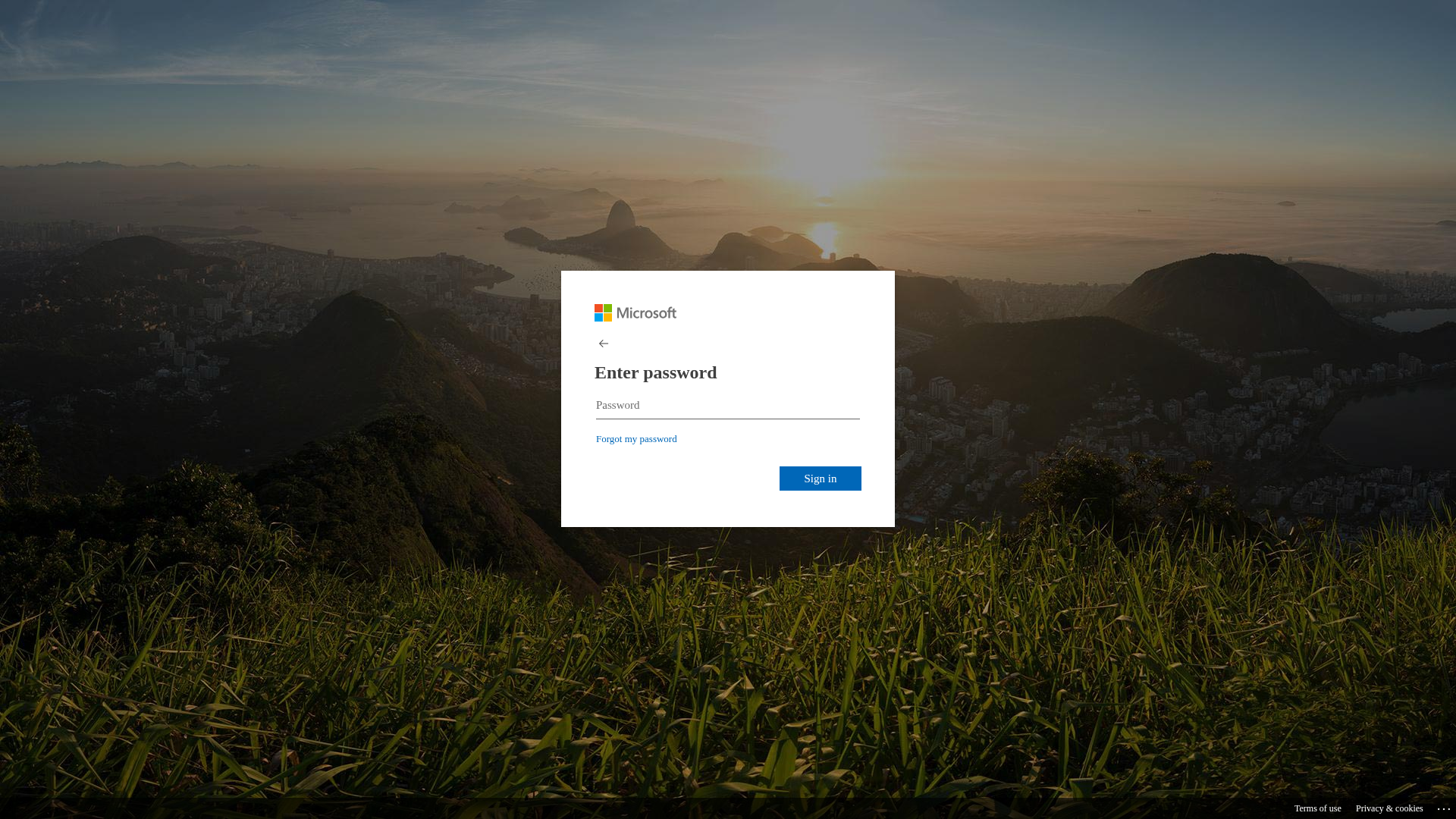
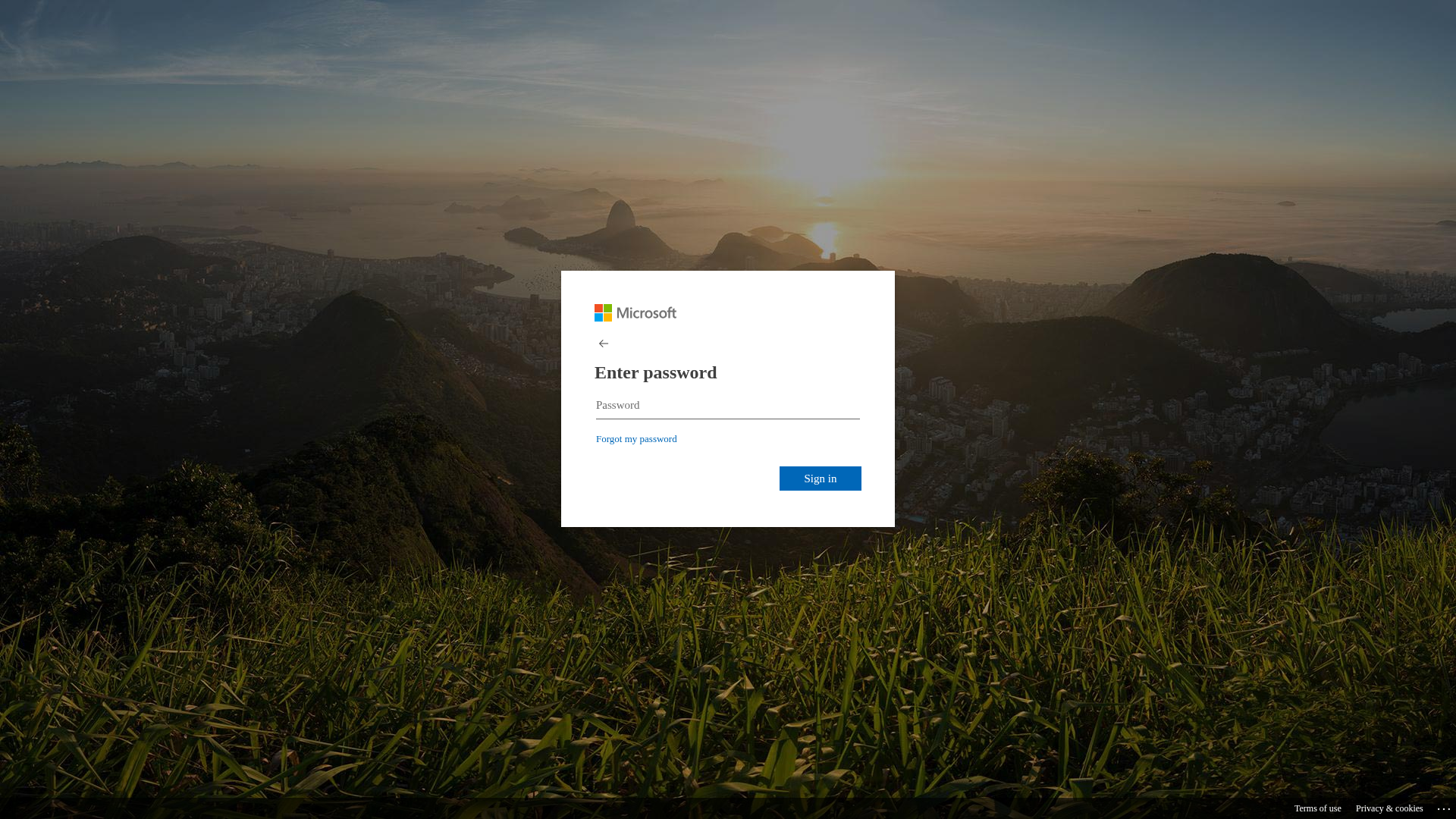
• Impersonating: Microsoft
- • Threat: Microsoft login page phishing
- • Target: Microsoft account users
- • Method: Steals passwords via a fake login form.
- • Exfil: Unknown data exfiltration point.
- • Indicators: Domain mismatch, impersonates Microsoft.
- • Risk: HIGH - Password theft risk
⚠ Risk Factors
- Brand impersonation of Microsoft on non-official domain
- Contains 2 credential harvesting form(s)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
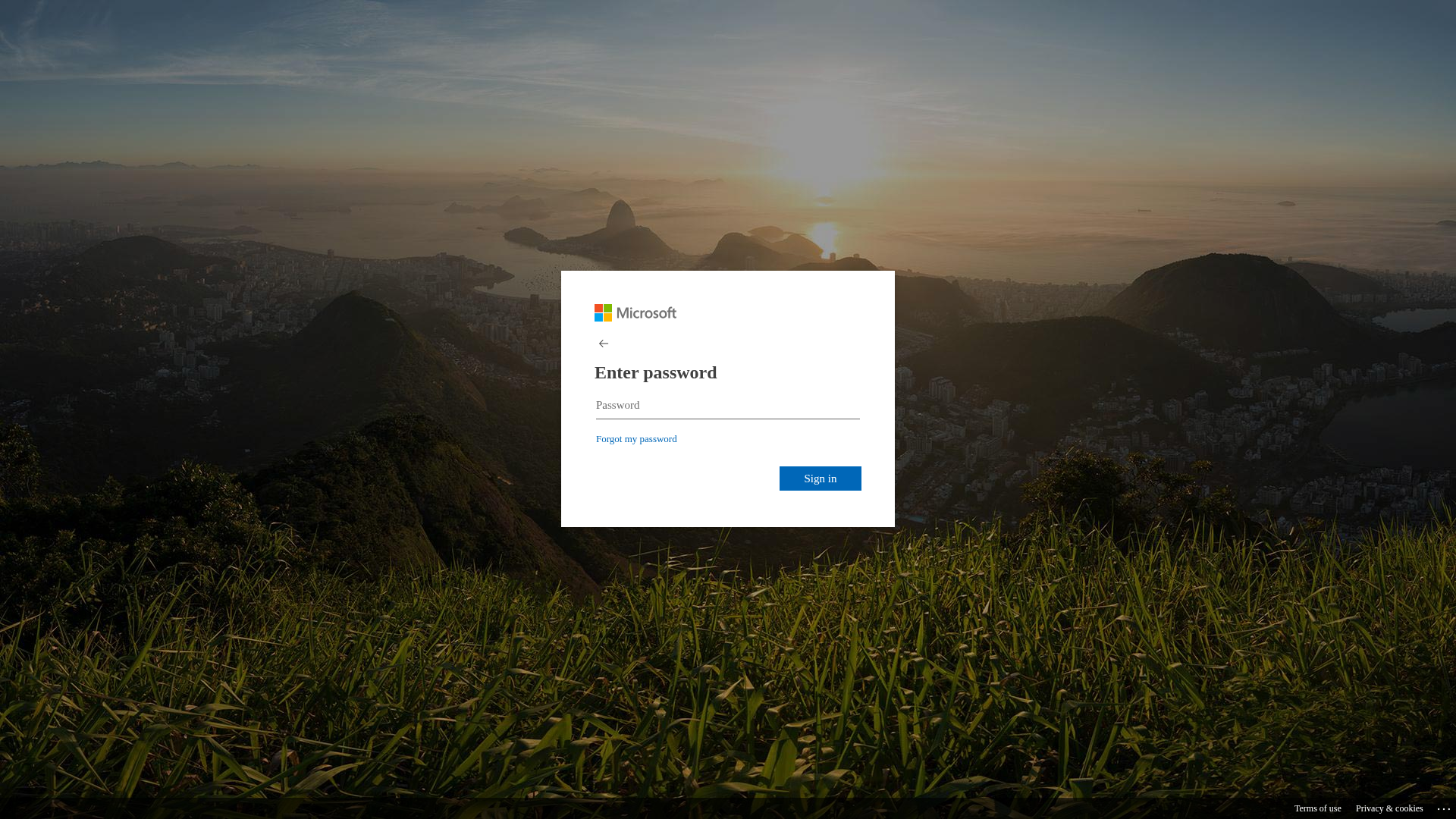
Detection Info
http://busanopen.org/office/msgvoice/source/Login.php
Detected Brand
Microsoft
Country
International
Confidence
100%
HTTP Status
200
Report ID
21cf16d5-e4e…
Analyzed
2025-12-30 23:47
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T113436CEABF121D77874696A1F436AD01B37A9D07898CCE84F19CD8842FFAE1D8127513 |
|
CONTENT
ssdeep
|
1536:qXF8awnep4mclCJ3WSykhtaALerxfya6j:qXqnefmjkhtaGutyao |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
989b7366cc5b321c |
|
VISUAL
aHash
|
ffff3e1818080000 |
|
VISUAL
dHash
|
f0f8f0b2b2f1dab2 |
|
VISUAL
wHash
|
ffffff1c18180800 |
|
VISUAL
colorHash
|
1bc00010000 |
|
VISUAL
cropResistant
|
e0e0f0f0f0f0f070,a8e0b8b8e4b083a2,f0f8f0b2b2f1dab2 |
Code Analysis
Risk Score
70/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Banking
🔬 Threat Analysis Report
• Threat: Microsoft login page phishing
• Target: Microsoft account users
• Method: Steals passwords via a fake login form.
• Exfil: Unknown data exfiltration point.
• Indicators: Domain mismatch, impersonates Microsoft.
• Risk: HIGH - Password theft risk
🔐 Credential Harvesting Forms
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
Scan History for busanopen.org
Found 9 other scans for this domain
-
http://www.busanopen.org/office/msgvoice/source/wr...
http://www.busanopen.org/office/msgvoice/source/Lo...
http://www.busanopen.org/office/msgvoice/source/wr...
http://busanopen.org/office/msgvoice/source/Login....
http://busanopen.org/office/msgvoice/cmd-login=a2a...
http://busanopen.org/office/msgvoice/source/wrongp...
http://busanopen.org/office/msgvoice/source/Login....
http://busanopen.org/office/msgvoice/source/wrongp...
http://busanopen.org/office/msgvoice/cmd-login=a2a...