
Phishing Analysis
Detailed analysis of captured phishing page
100
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: mail.com
⚠ Risk Factors
- Brand impersonation of mail.com on non-official domain
- Contains 5 form(s) with JavaScript submission
- JavaScript obfuscation detected (7 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
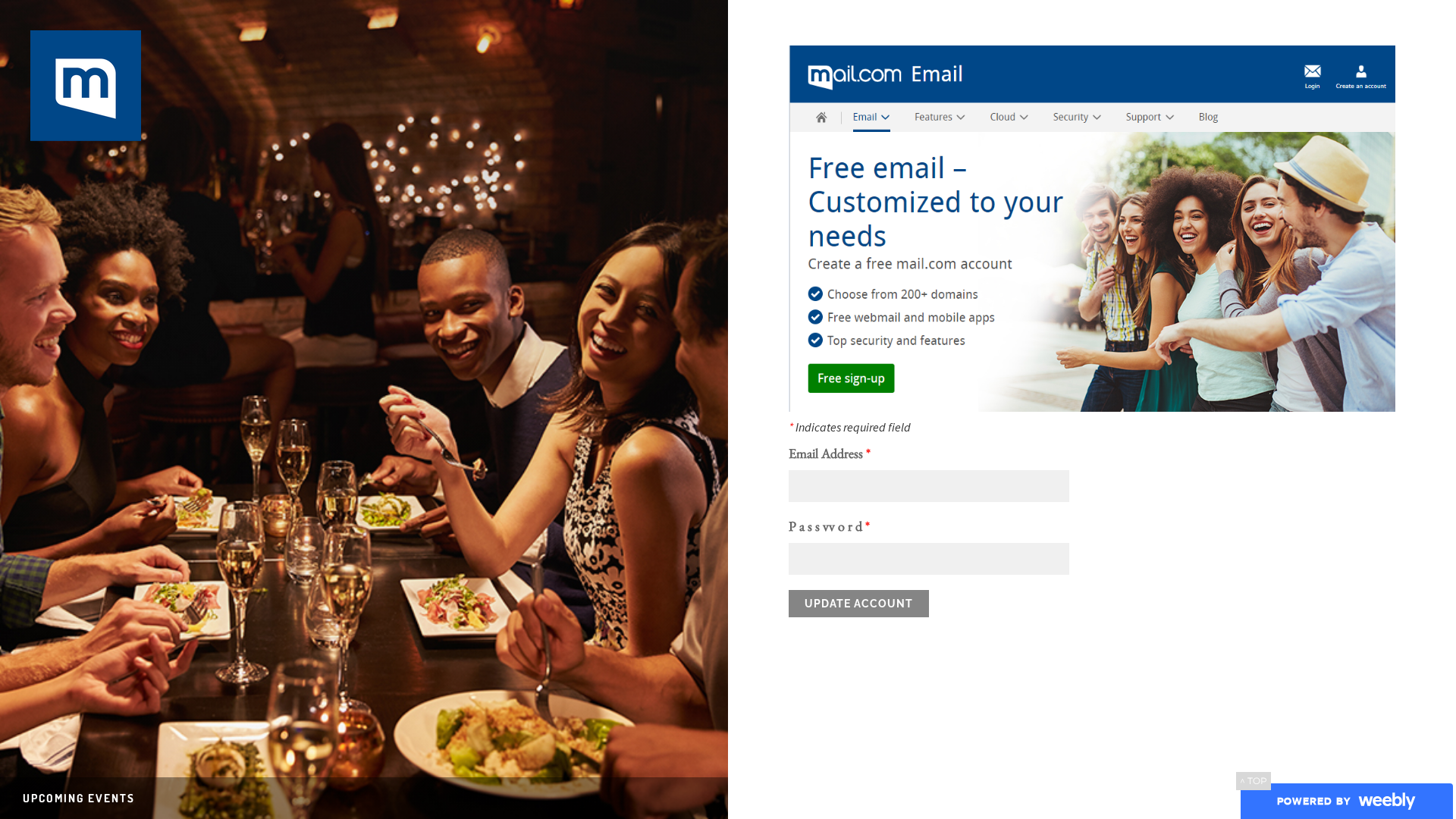
Detection Info
https://mailverificationteamoath.weebly.com/
Detected Brand
mail.com
Country
International
Confidence
100%
HTTP Status
200
Report ID
2df8651e-d8e…
Analyzed
2026-01-07 08:49
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T1B10260E2D054DD360B1682C5B7B6776FB6B2C305CB020D8453F813AE97CBDA0C722599 |
|
CONTENT
ssdeep
|
96:nk2hzy8zHwLIST3wKUEwt7aCLwvFiQedX3HF7eNXztX/10STu13GAx43a:k2hzy8zHwLBDVUEwIC5dkPXtN61ZeK |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
9b4a75a5056fd08b |
|
VISUAL
aHash
|
0f0f0d0d0f0f0f0f |
|
VISUAL
dHash
|
5b595979f99e5e98 |
|
VISUAL
wHash
|
0f0f0f0f0f0f0f0f |
|
VISUAL
colorHash
|
0b400030040 |
|
VISUAL
cropResistant
|
0923e765c770e489,cbe9383c69d3ab66,f1d19934262698d8,a8390a2c5edc0848,0081421213136380,3d2c6c2f37b766f0 |
Code Analysis
Risk Score
100/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Card Stealer
🎣 Banking
🎣 Personal Info
🔐 Credential Harvesting Forms
🔒 Obfuscation Detected
- atob
- eval
- fromCharCode
- unescape
- hex_escape
- unicode_escape
- base64_strings