
Phishing Analysis
Detailed analysis of captured phishing page
85
Risk Score
High Risk
Threat Level: ALTO
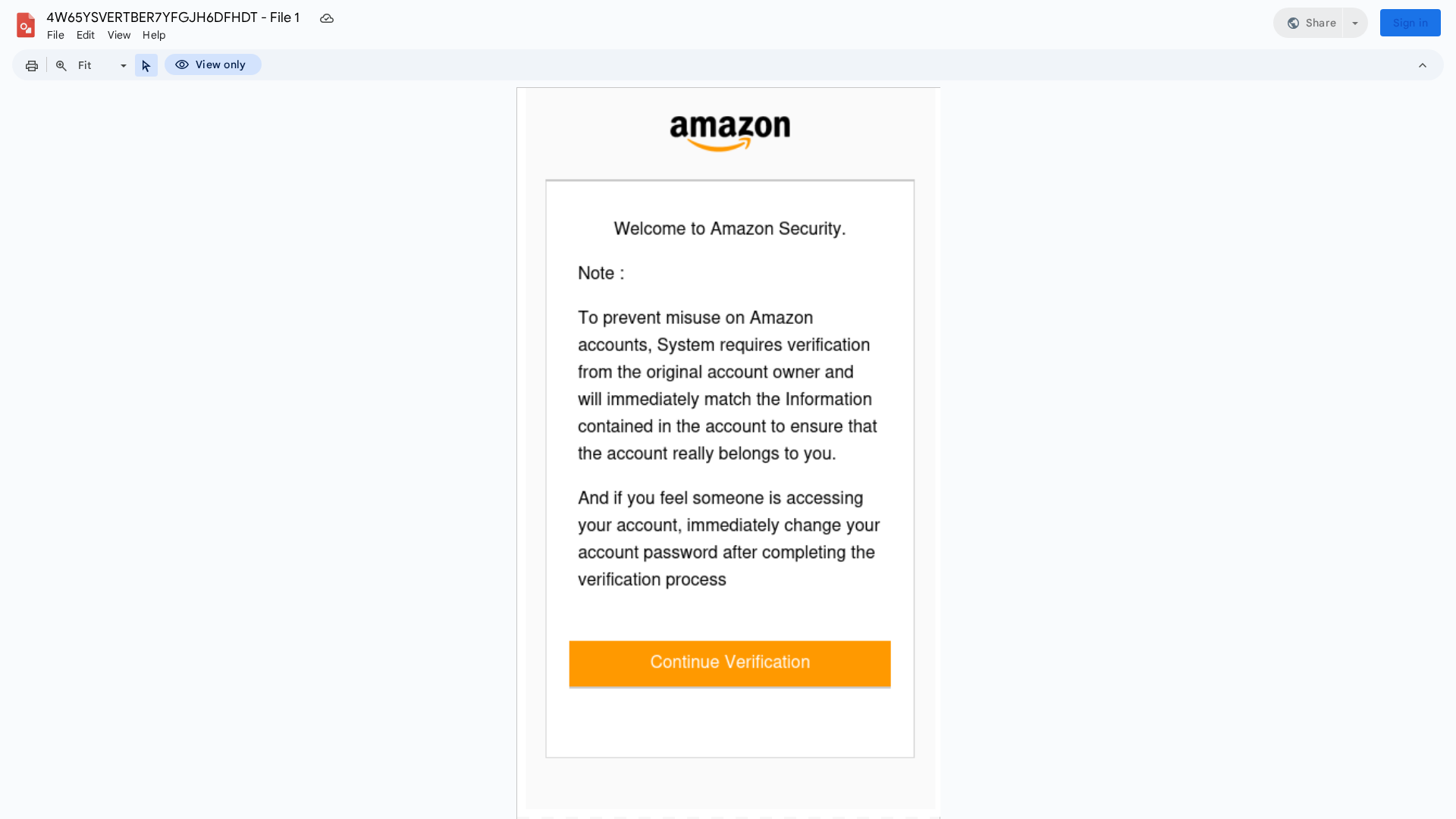
• Impersonating: Amazon
- • Threat: Credential harvesting phishing kit
- • Target: Amazon users worldwide
- • Method: Fake account verification form stealing login credentials
- • Exfil: Data sent via JavaScript form submission
- • Indicators: Free hosting, mismatched domain, obfuscated JavaScript
- • Risk: HIGH - Immediate credential theft
⚠ Risk Factors
- Brand impersonation of Amazon on non-official domain
- Contains 1 form(s) with JavaScript submission
- JavaScript obfuscation detected (8 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
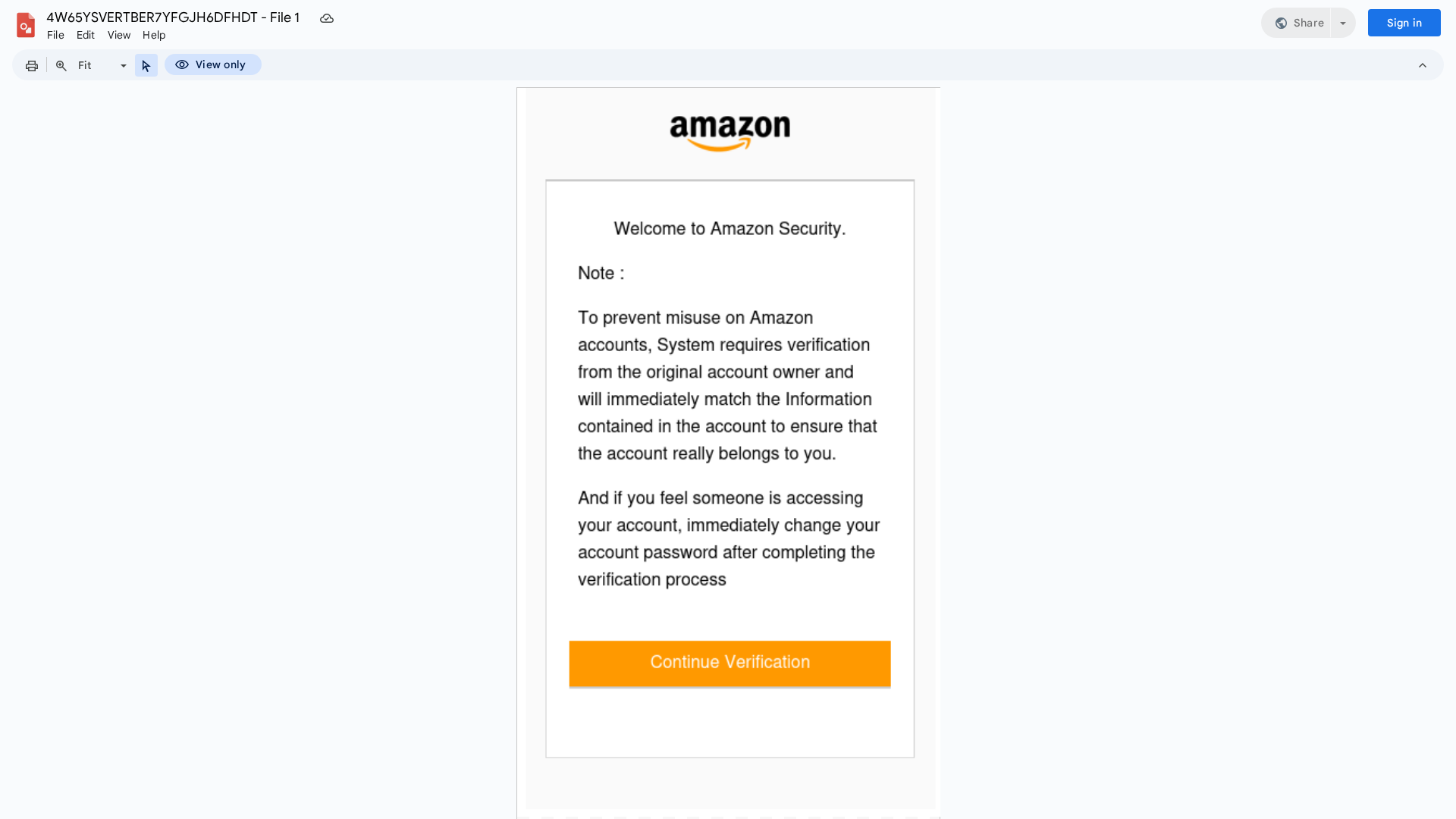
Detection Info
https://docs.google.com/drawings/d/190Yk_V_-cLjEeIhR1C1LOScKVKQ11-ArXUNFz4pQzcI/edit
Detected Brand
Amazon
Country
International
Confidence
100%
HTTP Status
200
Report ID
30f22e46-624…
Analyzed
2026-01-11 02:48
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T158130233C0132132525B52E9F8A0775A2293C32EDE4708491B7CDB913BFBDAA798795D |
|
CONTENT
ssdeep
|
768:aPlnP7P3Rk/CzpbsP6P1L13/lf8J6a+co6v+c6o4IE/Irb5dEoGEqOzVWsPk6TRz:aPRP7P3RkazSP6P1L13/Z8J6fco6Gc6i |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
b3154d171515dd55 |
|
VISUAL
aHash
|
26e7ffe7e7e7e7ff |
|
VISUAL
dHash
|
cc0d484c4c4c4c00 |
|
VISUAL
wHash
|
00c7c3c3c3c3c3df |
|
VISUAL
colorHash
|
07000030000 |
|
VISUAL
cropResistant
|
cc0d484c4c4c4c00 |
Code Analysis
Risk Score
85/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Card Stealer
🎣 Banking
🎣 Personal Info
🔬 Threat Analysis Report
• Threat: Credential harvesting phishing kit
• Target: Amazon users worldwide
• Method: Fake account verification form stealing login credentials
• Exfil: Data sent via JavaScript form submission
• Indicators: Free hosting, mismatched domain, obfuscated JavaScript
• Risk: HIGH - Immediate credential theft
🔒 Obfuscation Detected
- atob
- eval
- fromCharCode
- unescape
- document.write
- hex_escape
- unicode_escape
- base64_strings
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
Amazon
https://docs.google.com/drawings/d/11xexd5UMT6QESF02HqMmkPEU...
Jan 11, 2026
Amazon
https://docs.google.com/drawings/d/15ov9VhR-tRaq9DIx4tNJwWzy...
Jan 11, 2026
Amazon
https://docs.google.com/drawings/d/1_h_1iCfS3W1Ur1yGh_Y1Nzlp...
Jan 11, 2026
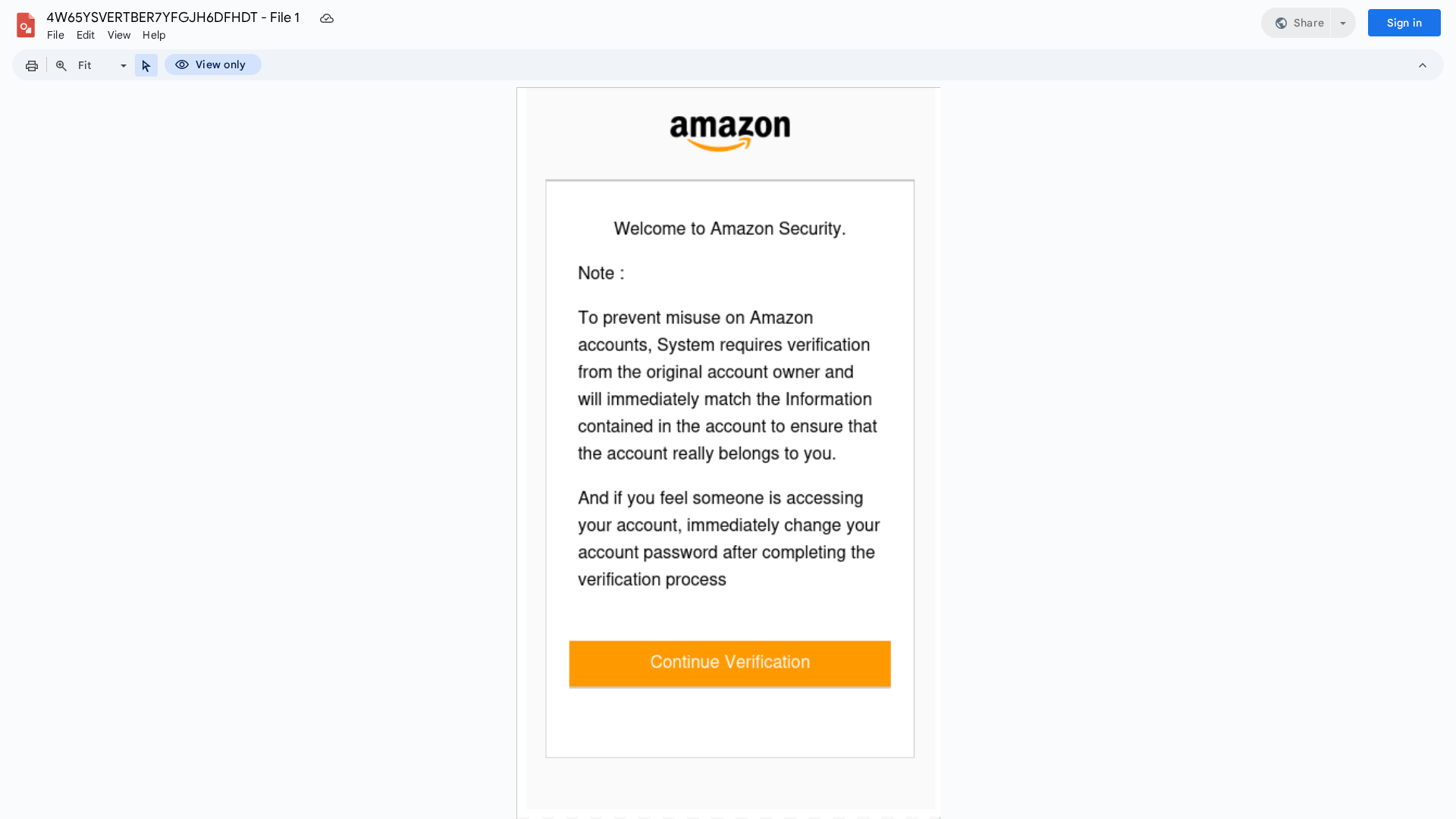
Amazon
https://docs.google.com/drawings/d/1dQMa47Fd8vnFDell9g2SZue1...
Jan 11, 2026
Amazon
https://docs.google.com/drawings/d/1Lea2nevYu24J3vHPj5nczYK1...
Jan 11, 2026
Scan History for docs.google.com
Found 10 other scans for this domain
-
https://docs.google.com/drawings/d/11xexd5UMT6QESF...
https://docs.google.com/drawings/d/13Ry6oOPFPy8tbt...
https://docs.google.com/drawings/d/15ov9VhR-tRaq9D...
https://docs.google.com/drawings/d/1957BITCF-CtdbS...
https://docs.google.com/drawings/d/1_h_1iCfS3W1Ur1...
https://docs.google.com/drawings/d/1dQMa47Fd8vnFDe...
https://docs.google.com/drawings/d/1Lea2nevYu24J3v...
https://docs.google.com/drawings/d/1OpmsKCMLq52t1Q...
https://docs.google.com/drawings/d/1oQCBCopkebz7iG...
https://docs.google.com/drawings/d/1pC-6gJ7jvRL8d_...