
Phishing Analysis
Detailed analysis of captured phishing page
100
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: Keplr
- • Threat: Seed phrase phishing attack
- • Target: Keplr wallet users
- • Method: Fake form requests wallet recovery phrase
- • Exfil: User submitted seed phrase
- • Indicators: Non official domain, asking for keyphrase
- • Risk: CRITICAL - Immediate wallet compromise
⚠ Risk Factors
- JavaScript obfuscation detected (5 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
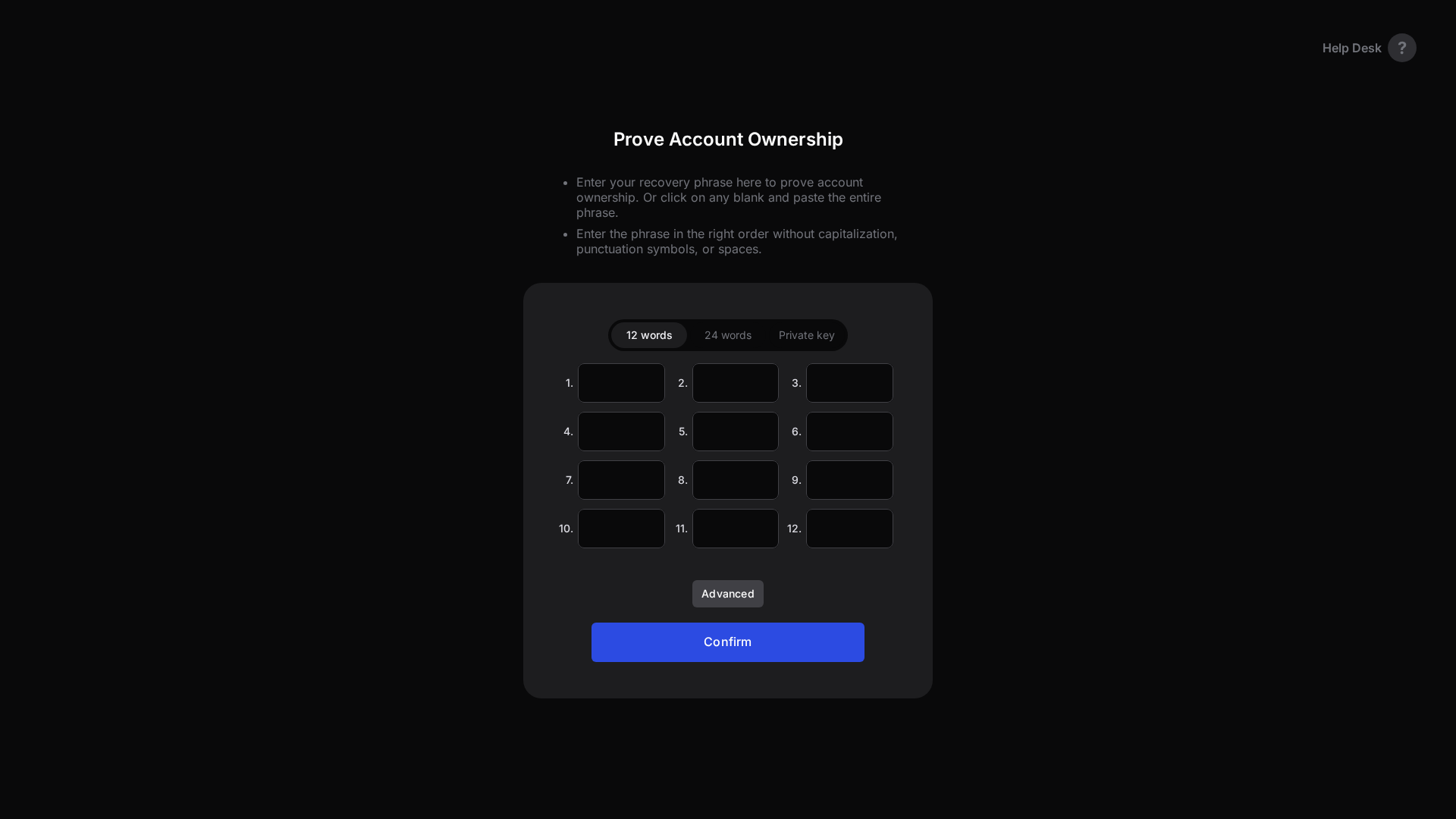
Detection Info
https://keplr.zone
Detected Brand
Keplr
Country
International
Confidence
100%
HTTP Status
200
Report ID
3709dfde-ed0…
Analyzed
2026-01-11 08:33
Final URL (after redirects)
https://keplr.zone/
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T1E36235364501FC2A40A3B3E052B5438F22A1E759DED7476A03F28769AFC7DE8CD2549A |
|
CONTENT
ssdeep
|
96:nVAdLrqWqjDS2YG3qXiTMBhT8GhT85KPFDLFD4FDpFDeFDfFDsFDNFDiFDOFDxb0:VAdnGDrDTohT8GhT85KqwH |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
cc263199279c6677 |
|
VISUAL
aHash
|
0018181818181800 |
|
VISUAL
dHash
|
113230302032320c |
|
VISUAL
wHash
|
01183c3c3c3c3c0c |
|
VISUAL
colorHash
|
380000001c0 |
|
VISUAL
cropResistant
|
113230302032320c |
Code Analysis
Risk Score
100/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Card Stealer
🎣 Banking
🎣 Personal Info
🔬 Threat Analysis Report
• Threat: Seed phrase phishing attack
• Target: Keplr wallet users
• Method: Fake form requests wallet recovery phrase
• Exfil: User submitted seed phrase
• Indicators: Non official domain, asking for keyphrase
• Risk: CRITICAL - Immediate wallet compromise
🔒 Obfuscation Detected
- atob
- eval
- fromCharCode
- unescape
- base64_strings