
Phishing Analysis
Detailed analysis of captured phishing page
100
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: bright.net
⚠ Risk Factors
- Brand impersonation of bright.net on non-official domain
- Contains 5 form(s) with JavaScript submission
- JavaScript obfuscation detected (7 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
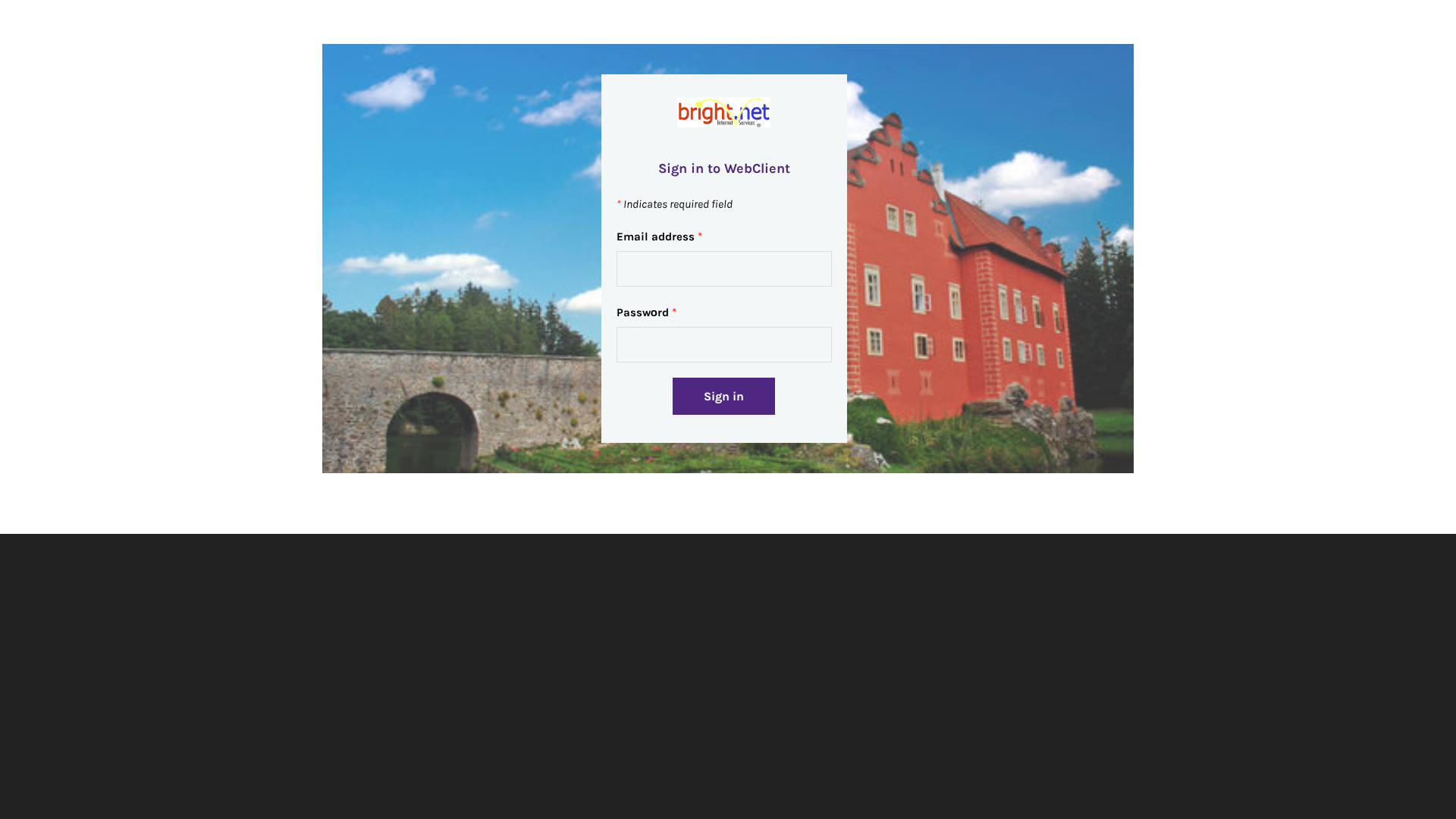
Detection Info
https://icewarpwebclientbright.weebly.com/
Detected Brand
bright.net
Country
USA
Confidence
100%
HTTP Status
200
Report ID
447b6461-2f3…
Analyzed
2026-01-07 10:18
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T1B0F10FF1D040ED3B435385DAA7B96B0B7291C349CB071A4493F883AB6BDACA0CB25599 |
|
CONTENT
ssdeep
|
96:nkdn/zD71tDlt8v67ZSwVBKhoSS8ctmMT/GCwvFoUQeJXcHFTexXEz/dmYfd2J:kdn/zD715lt8iDBKh2YM7i+Miz4cdw |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
e9e91692e84bc3c6 |
|
VISUAL
aHash
|
ffdbfbdbff000000 |
|
VISUAL
dHash
|
33333333334c3200 |
|
VISUAL
wHash
|
ffdbdbdbdb000000 |
|
VISUAL
colorHash
|
064010000c0 |
|
VISUAL
cropResistant
|
1733373333333313,0c72e2d2f262d2d2,73b1707272686a70,0f2f8bebcd6d0480,0000000000000000 |
Code Analysis
Risk Score
100/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Card Stealer
🎣 Banking
🎣 Personal Info
🔐 Credential Harvesting Forms
🔒 Obfuscation Detected
- atob
- eval
- fromCharCode
- unescape
- hex_escape
- unicode_escape
- base64_strings