Phishing Analysis
Detailed analysis of captured phishing page
65
Risk Score
Medium Risk
Threat Level: CRITICAL
• Impersonating: Microsoft
- • Threat: Microsoft login page phishing
- • Target: Users of Microsoft services
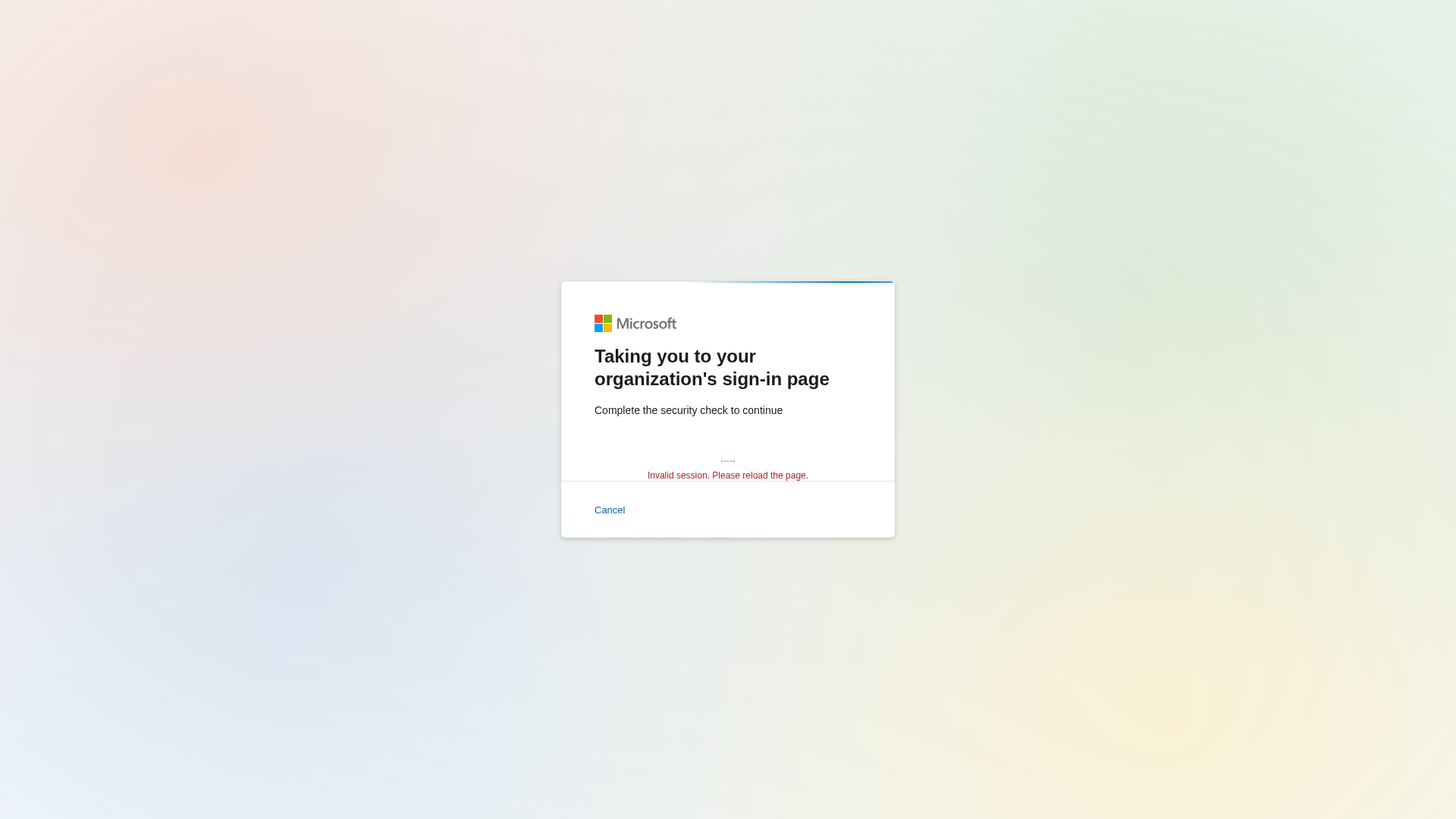
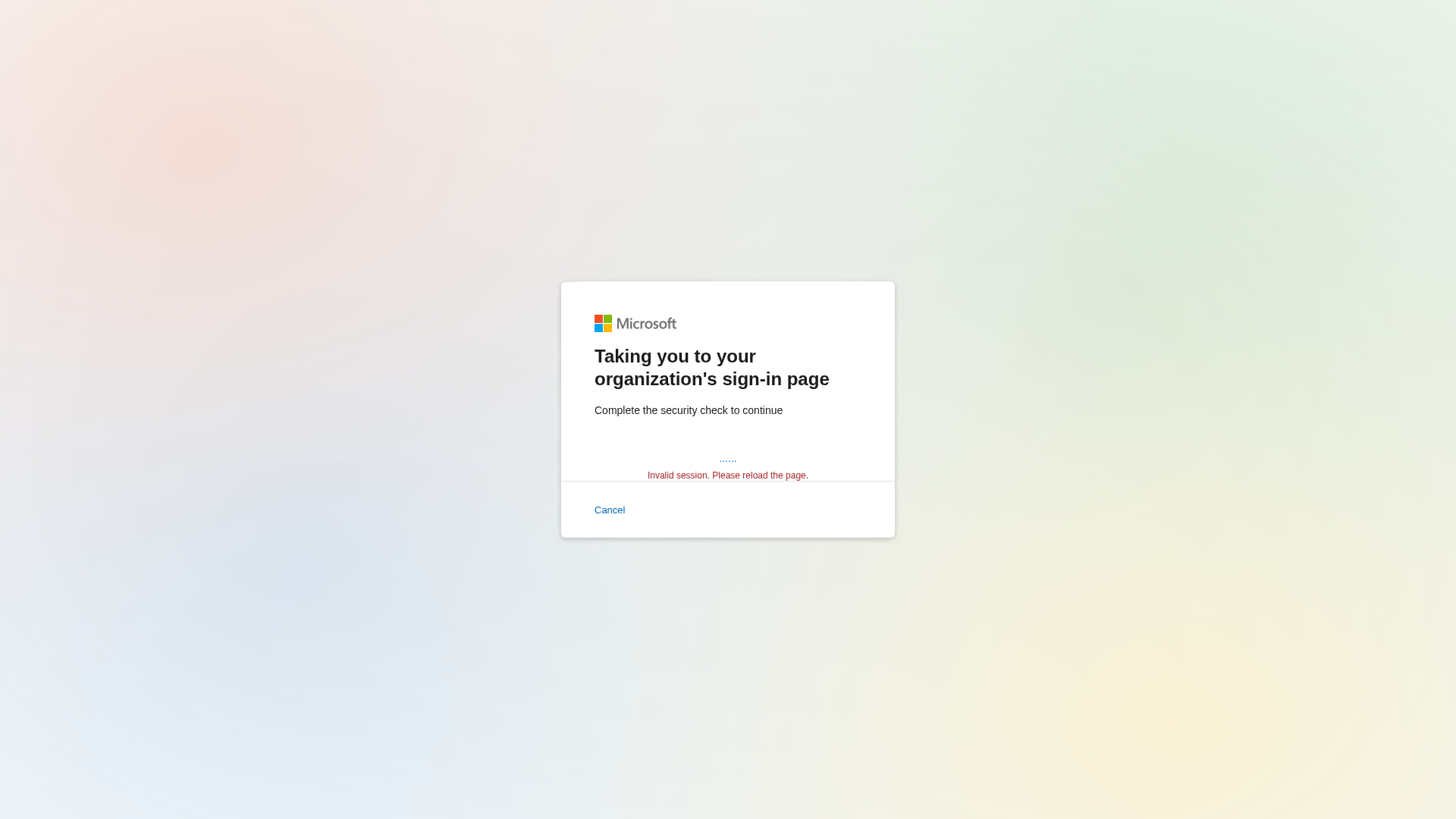
- • Method: Displays fake 'Taking you to your organization's sign-in page' message
- • Exfil: No form visible, likely redirects to a credential harvesting page
- • Indicators: Domain mismatch, hosted on r2.dev, no login form directly visible
- • Risk: HIGH - Could redirect to a credential harvesting login form
⚠ Risk Factors
- Brand impersonation of Microsoft on non-official domain
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
Detection Info
http://pub-60feb3b0da144b72b0f8c76714a15abf.r2.dev/index.html?error
Detected Brand
Microsoft
Country
International
Confidence
100%
HTTP Status
200
Report ID
4774b15e-3d4…
Analyzed
2025-12-25 21:43
Final URL (after redirects)
https://pub-60feb3b0da144b72b0f8c76714a15abf.r2.dev/index.html?error
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T181218B68E048893747A3D1D9A5A1A35F3AA0878CD7130B055FF8039927DFEA8CD021D9 |
|
CONTENT
ssdeep
|
24:n/nTxVx/cIgDETsCVlWJnPBrNPALc756Fl+Nit8zZrAd:ntf/cIgwYCvA/PW8CMiN |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
9b4ae68cd933cc8c |
|
VISUAL
aHash
|
180018081d1f1fbf |
|
VISUAL
dHash
|
7161717b33717d79 |
|
VISUAL
wHash
|
391818081f1f1fff |
Code Analysis
Risk Score
65/100
Threat Level
CRITICAL
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🔬 Threat Analysis Report
• Threat: Microsoft login page phishing
• Target: Users of Microsoft services
• Method: Displays fake 'Taking you to your organization's sign-in page' message
• Exfil: No form visible, likely redirects to a credential harvesting page
• Indicators: Domain mismatch, hosted on r2.dev, no login form directly visible
• Risk: HIGH - Could redirect to a credential harvesting login form
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
Scan History for pub-60feb3b0da144b72b0f8c76714a15abf.r2.dev
Found 3 other scans for this domain