
Phishing Analysis
Detailed analysis of captured phishing page
100
Risk Score
High Risk
Threat Level: ALTO
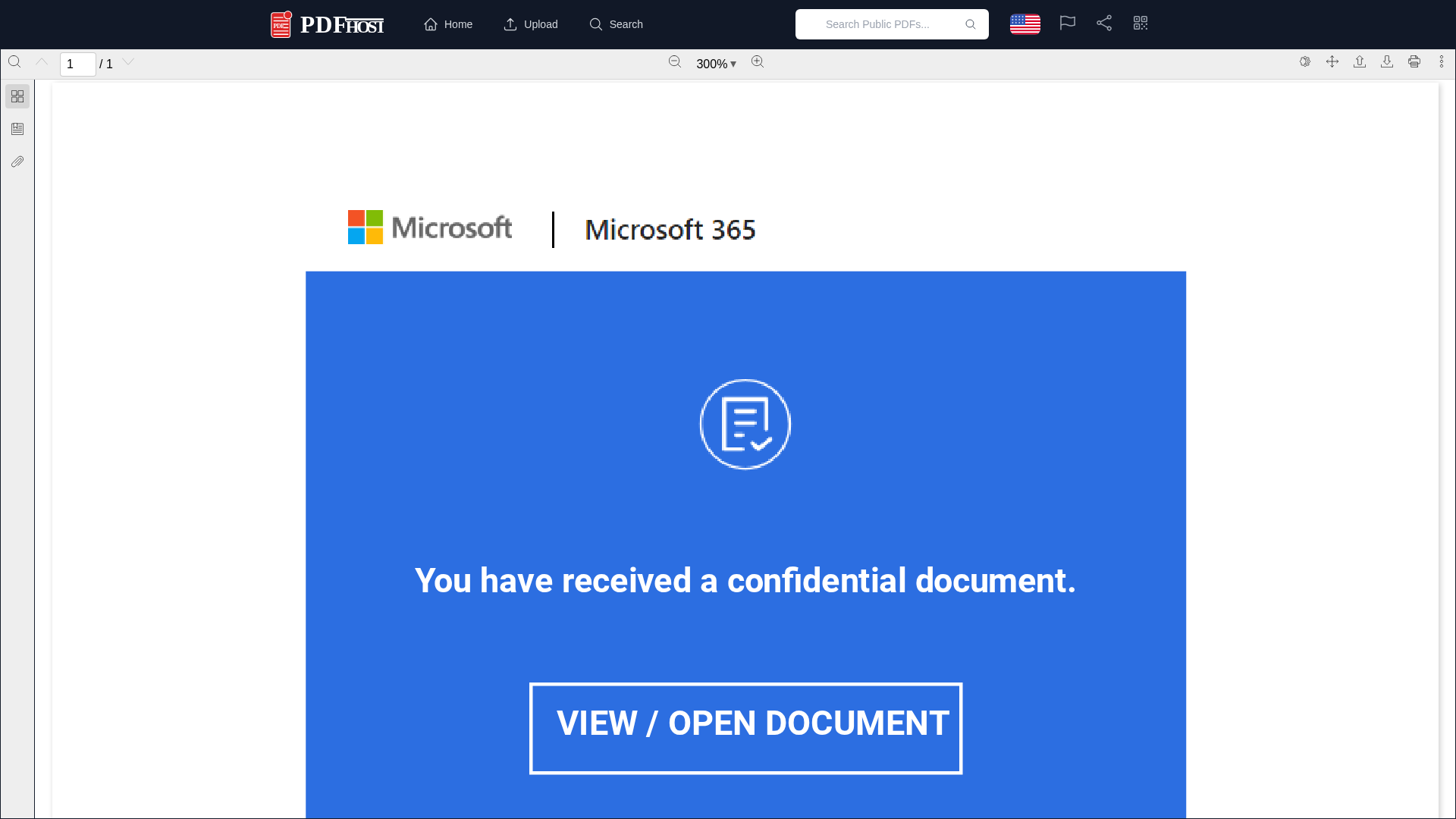
• Impersonating: Microsoft
- • Threat: Document phishing using brand impersonation
- • Target: Microsoft users, specifically those using Microsoft 365
- • Method: A fake document hosted on a non-Microsoft domain attempts to trick users into clicking a button
- • Exfil: Unknown, likely to a credential harvesting or malware installation site
- • Indicators: Domain mismatch (pdfhost.io vs microsoft.com), Microsoft brand impersonation, generic call to action
- • Risk: HIGH - Potential for credential theft, malware download, or further phishing attacks
⚠ Risk Factors
- Brand impersonation of Microsoft on non-official domain
- JavaScript obfuscation detected (7 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
Detection Info
https://pdfhost.io/v/maTYQa.jg_mqfilserawxgxdgxhhgsx_1
Detected Brand
Microsoft
Country
USA
Confidence
100%
HTTP Status
200
Report ID
57f5df90-24c…
Analyzed
2026-01-01 10:48
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T196E2F9319184263E52074FD8F4E6B339304BD169D587A4909FFA01DA46E9CECE3792F6 |
|
CONTENT
ssdeep
|
384:IniRjd79HwJ7ATzzz2z9tLYHlwaWtMQhsnrEZkfKkOKkCr1lDWmwPxx4hukUiFPH:59QhWKmQxkpLt14bfpOF/4VW |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
f8939313793b1313 |
|
VISUAL
aHash
|
08ffffc1c1c1c1c1 |
|
VISUAL
dHash
|
d9002b13132b3b3b |
|
VISUAL
wHash
|
08ffffc1c1c1c1c1 |
|
VISUAL
colorHash
|
060000001c0 |
|
VISUAL
cropResistant
|
82a00b13132b3b3b,282829dac9aa6aa9,272a2826263c3ca6,261999d9d9999946,08303008c8607969 |
Code Analysis
Risk Score
100/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Banking
🎣 Personal Info
🔬 Threat Analysis Report
• Threat: Document phishing using brand impersonation
• Target: Microsoft users, specifically those using Microsoft 365
• Method: A fake document hosted on a non-Microsoft domain attempts to trick users into clicking a button
• Exfil: Unknown, likely to a credential harvesting or malware installation site
• Indicators: Domain mismatch (pdfhost.io vs microsoft.com), Microsoft brand impersonation, generic call to action
• Risk: HIGH - Potential for credential theft, malware download, or further phishing attacks
🔒 Obfuscation Detected
- atob
- eval
- fromCharCode
- unescape
- hex_escape
- unicode_escape
- base64_strings
Scan History for pdfhost.io
Found 3 other scans for this domain