
Phishing Analysis
Detailed analysis of captured phishing page
10
Risk Score
Low Risk
Threat Level: ALTO
• Impersonating: Social Security Administration
- • Threat: Phishing attempt targeting Social Security recipients
- • Target: Social Security Administration users in the USA
- • Method: Fake document prompting users to download an attachment
- • Exfil: Potential malware or credential theft via downloaded file
- • Indicators: Domain mismatch, hosted on Amazon S3, unusual instructions
- • Risk: HIGH - Potential for malware infection or credential theft
⚠ Risk Factors
- Brand impersonation of Social Security Administration on non-official domain
Visual Capture
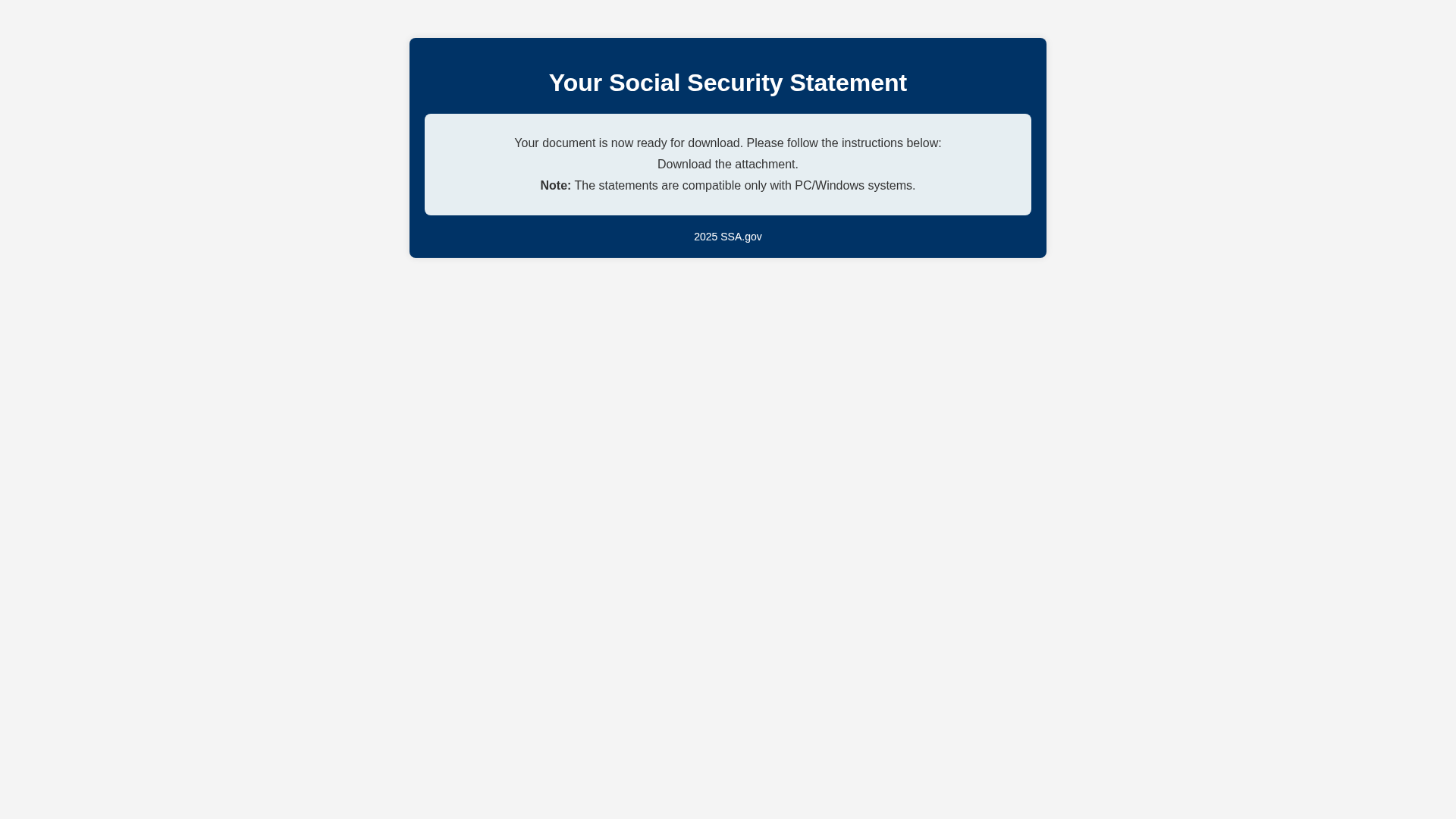
Detection Info
https://newss2026.s3.us-east-2.amazonaws.com/OPENS.html
Detected Brand
Social Security Administration
Country
USA
Confidence
95%
HTTP Status
200
Report ID
5aa89280-951…
Analyzed
2026-01-11 04:02
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T101F00223A04148798CE6C1605F6AC24DA748D0C5FB0B1A013DCAA21C5EE9E5BC4B71C8 |
|
CONTENT
ssdeep
|
12:nwMy7FUN1vRR8LAy7ZWy8CfvRtS3llTRilfRetUe4m:n/C21JR8LACZFhfJol9RMe1 |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
b1313171dfc76464 |
|
VISUAL
aHash
|
c3c3c3ffffffffff |
|
VISUAL
dHash
|
9696966806000000 |
|
VISUAL
wHash
|
03030303f0f0f0f0 |
|
VISUAL
colorHash
|
070000001c0 |
|
VISUAL
cropResistant
|
9696966806000000,004007e8ece81782,a2a2412c32320810 |
Code Analysis
Risk Score
10/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🔬 Threat Analysis Report
• Threat: Phishing attempt targeting Social Security recipients
• Target: Social Security Administration users in the USA
• Method: Fake document prompting users to download an attachment
• Exfil: Potential malware or credential theft via downloaded file
• Indicators: Domain mismatch, hosted on Amazon S3, unusual instructions
• Risk: HIGH - Potential for malware infection or credential theft
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
No screenshot
Social Security Administration
https://opens72.s3.us-east-2.amazonaws.com/OPENS.html
Dec 21, 2025
No screenshot
Social Security Administration
https://odsfl.s3.us-east-2.amazonaws.com/NEW.html
Dec 15, 2025
No screenshot
Social Security Administration
https://brok6.s3.us-east-2.amazonaws.com/SSA.html
Dec 13, 2025