
Phishing Analysis
Detailed analysis of captured phishing page
100
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: Bitget
- • Threat: Credential harvesting phishing kit
- • Target: Bitget users internationally
- • Method: Fake login form stealing email and password
- • Exfil: Data sent to unknown server
- • Indicators: Domain mismatch, obfuscated JavaScript, unrelated TLD
- • Risk: HIGH - Immediate credential theft
⚠ Risk Factors
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
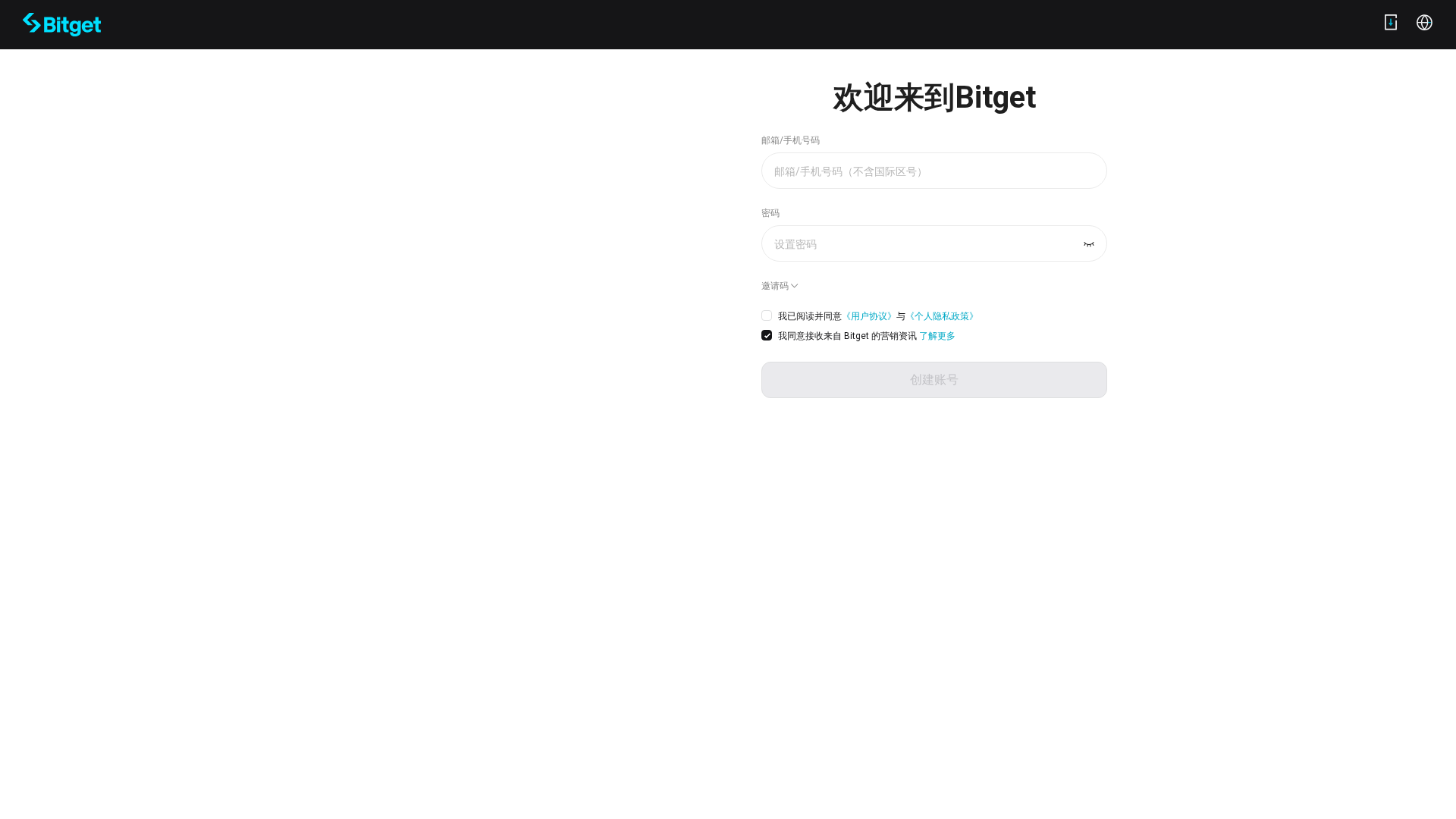
Detection Info
https://bitget.lol
Detected Brand
Bitget
Country
International
Confidence
100%
HTTP Status
200
Report ID
6046839b-0f5…
Analyzed
2026-01-11 08:34
Final URL (after redirects)
https://www.bitget.com/zh-CN/expressly?channelCode=wsqx&vipCode=j84h8205&languageType=1&groupId=543823
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T1379285E6B50098A6A133C7E5E471771A6197F32FCA1546E043EC82AD0EE7CFDF916848 |
|
CONTENT
ssdeep
|
192:se6e62RclRAph5lZZwHQAeDuY0eEkEePGv3hYeEhk8l2cVphYQ77KC9iQE+QnQRw:42RSRnnRvdECeL9WQGprpl5Ee1z |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
ec6c6d696c66121b |
|
VISUAL
aHash
|
00ffffffffffffff |
|
VISUAL
dHash
|
07040c0602000000 |
|
VISUAL
wHash
|
00f1f1f10f0f0f0f |
|
VISUAL
colorHash
|
07001000180 |
|
VISUAL
cropResistant
|
0604060600000000,0000414141418000 |
Code Analysis
Risk Score
100/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Card Stealer
🎣 Banking
🎣 Personal Info
🔬 Threat Analysis Report
• Threat: Credential harvesting phishing kit
• Target: Bitget users internationally
• Method: Fake login form stealing email and password
• Exfil: Data sent to unknown server
• Indicators: Domain mismatch, obfuscated JavaScript, unrelated TLD
• Risk: HIGH - Immediate credential theft
🔒 Obfuscation Detected
- atob
- fromCharCode
- base64_strings