Phishing Analysis
Detailed analysis of captured phishing page
100
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: Great Plains Federal Credit Union
- • Threat: Credential harvesting phishing
- • Target: Great Plains Federal Credit Union customers
- • Method: Fake login form stealing user ID and password
- • Exfil: Unknown, likely to a compromised server or email address.
- • Indicators: Free hosting, mismatched domain, login form.
- • Risk: HIGH - Immediate credential theft risk.
⚠ Risk Factors
- Brand impersonation of Great Plains Federal Credit Union on non-official domain
- Contains 5 form(s) with JavaScript submission
- JavaScript obfuscation detected (7 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
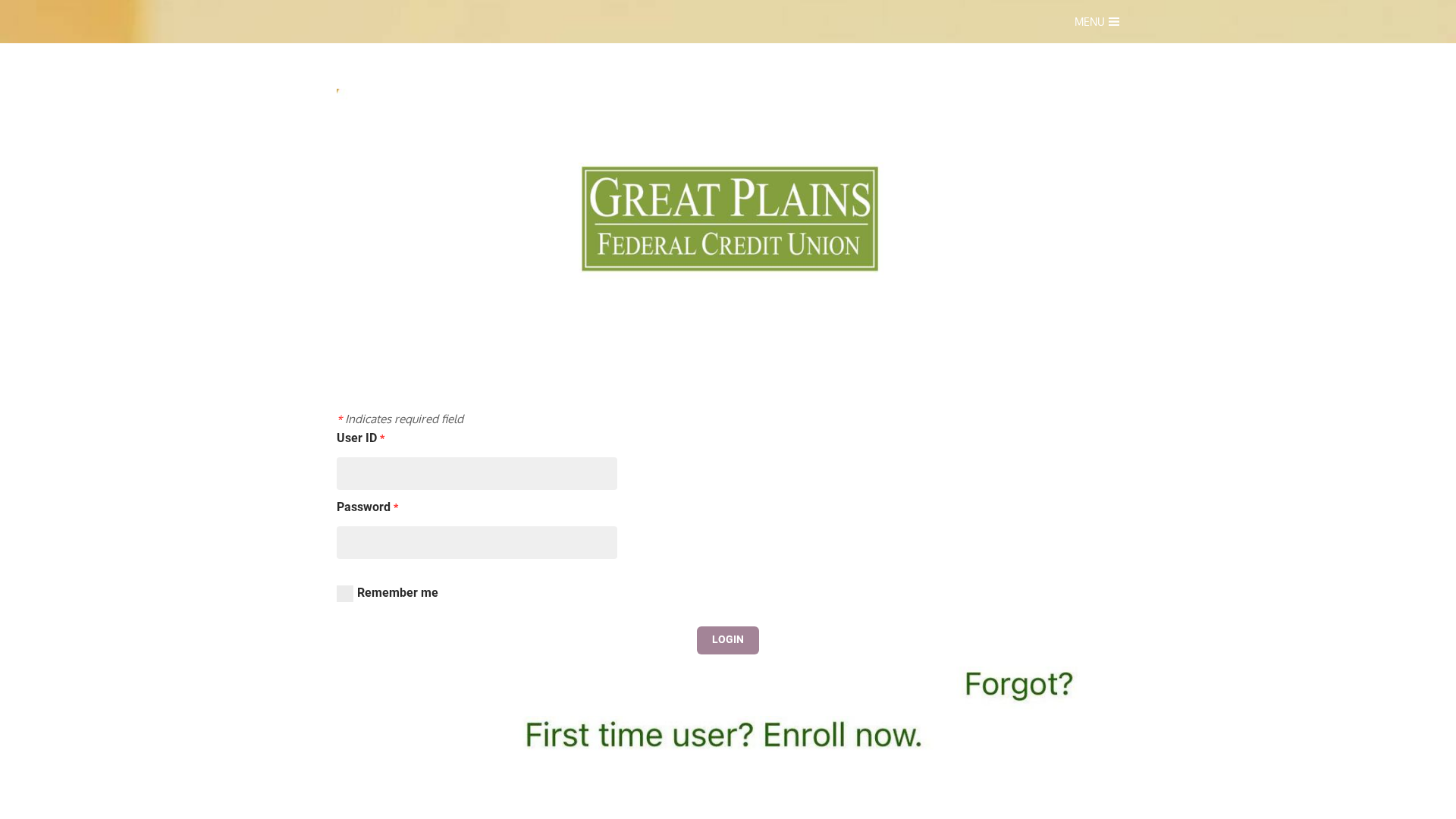
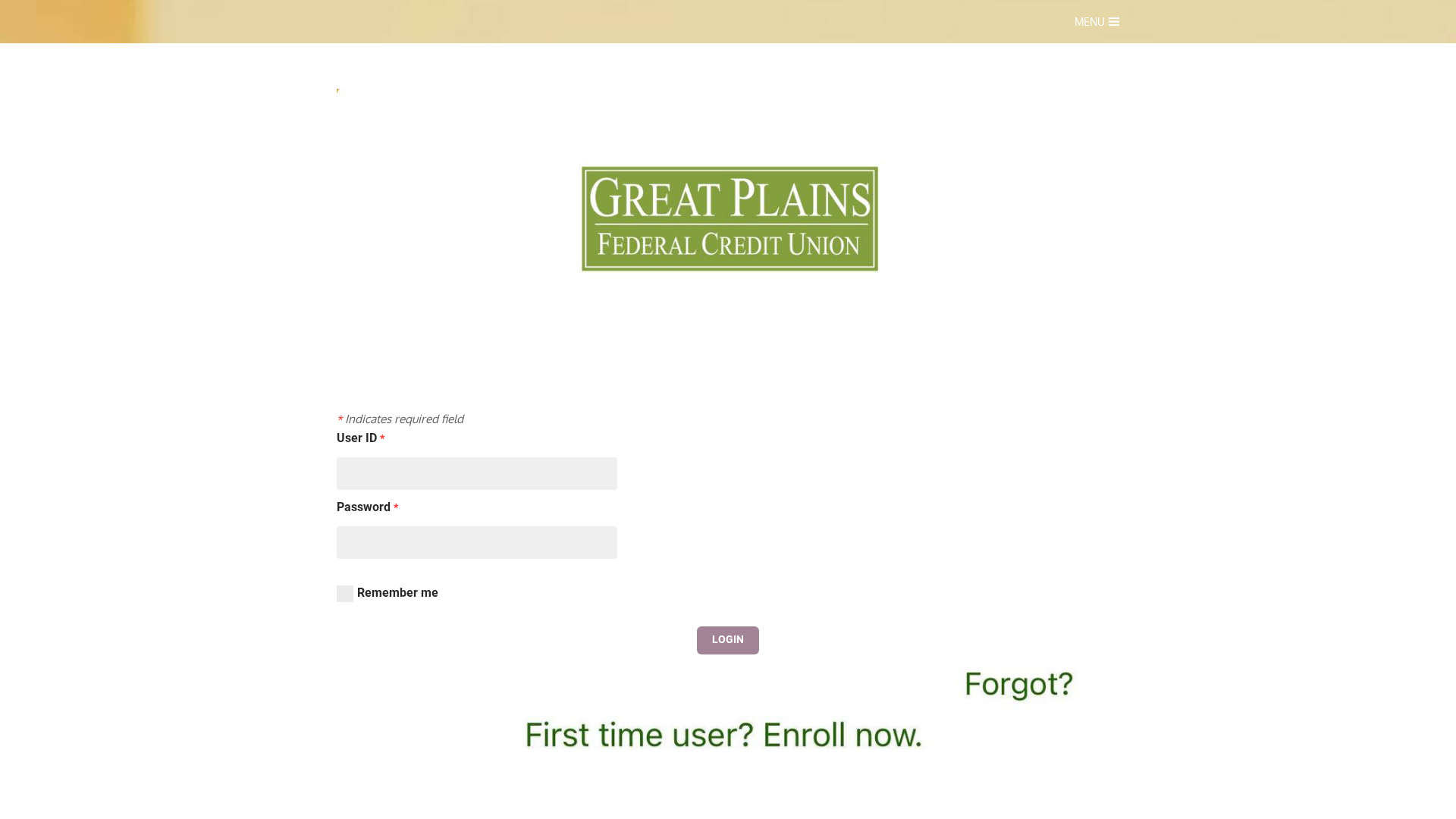
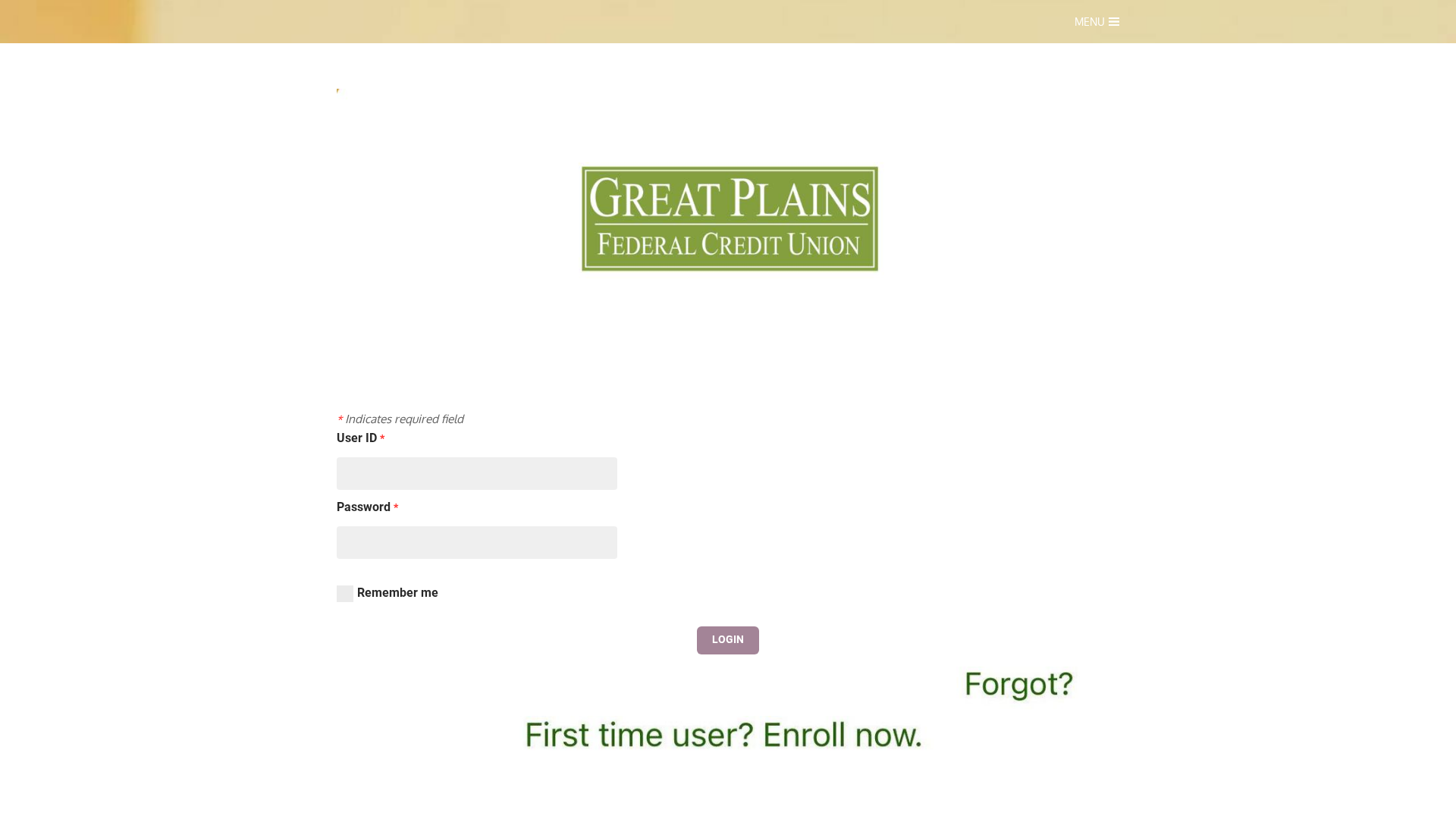
Visual Capture
Detection Info
https://vfygpfcu.weebly.com/
Detected Brand
Great Plains Federal Credit Union
Country
USA
Confidence
100%
HTTP Status
200
Report ID
6d38d95a-abb…
Analyzed
2025-12-31 14:12
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T17C1234D2C404DE3A031685D9F7F52B5FB996C359CB06098493FC82AB9BDBC60CA12799 |
|
CONTENT
ssdeep
|
192:kQHkahHW1UadyjlGjWwy04rIM1OIMGnpBjQR:k6Q5QjlGi10M17MGnTM |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
b626631c994d3667 |
|
VISUAL
aHash
|
00e7e7ffdfdfe3e7 |
|
VISUAL
dHash
|
f00c4d2034380a0e |
|
VISUAL
wHash
|
00e7e0f88f8fc3c3 |
|
VISUAL
colorHash
|
073c0000000 |
|
VISUAL
cropResistant
|
f00c4d2034380a0e |
Code Analysis
Risk Score
100/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Card Stealer
🎣 Banking
🎣 Personal Info
🔬 Threat Analysis Report
• Threat: Credential harvesting phishing
• Target: Great Plains Federal Credit Union customers
• Method: Fake login form stealing user ID and password
• Exfil: Unknown, likely to a compromised server or email address.
• Indicators: Free hosting, mismatched domain, login form.
• Risk: HIGH - Immediate credential theft risk.
🔐 Credential Harvesting Forms
🔒 Obfuscation Detected
- atob
- eval
- fromCharCode
- unescape
- hex_escape
- unicode_escape
- base64_strings
Similar Websites
Pages with identical visual appearance (based on perceptual hash)