
Phishing Analysis
Detailed analysis of captured phishing page
95
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: Yahoo!
⚠ Risk Factors
- Brand impersonation of Yahoo! on non-official domain
- Contains 1 credential harvesting form(s)
- JavaScript obfuscation detected (5 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
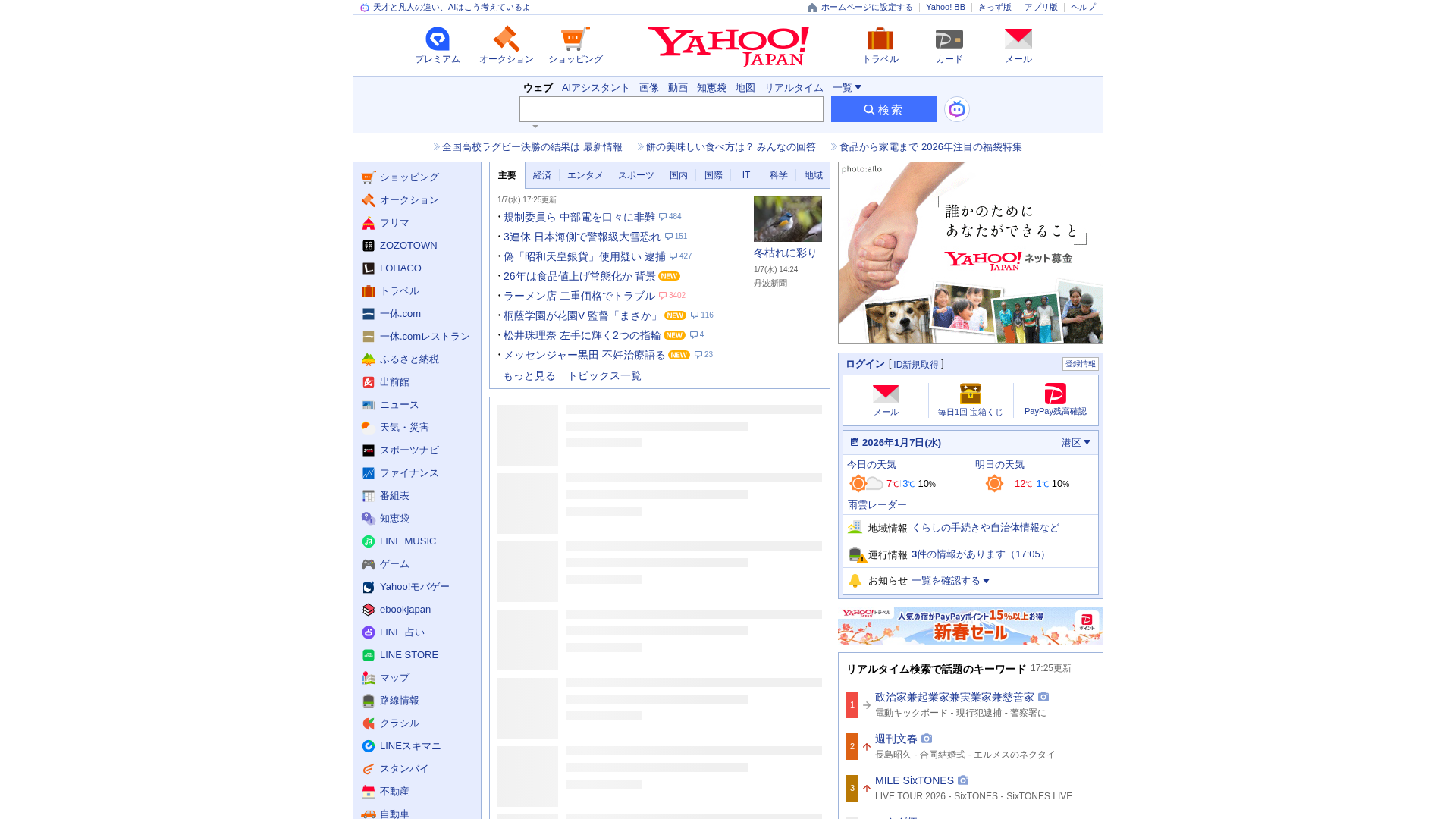
Detection Info
https://rstGGw.hbpetud.cn
Detected Brand
Yahoo!
Country
Unknown
Confidence
100%
HTTP Status
200
Report ID
6d4ee5d9-f75…
Analyzed
2026-01-07 08:32
Final URL (after redirects)
https://www.yahoo.co.jp/
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T11223A8BEA1A26837013F60CDA955277D70F65E3EDF5B5810EBBC8798138ED47B24180A |
|
CONTENT
ssdeep
|
768:2lgHL2pDjsz3nuMCc60FsJCDeTBLPk4eSWKNYvJKcCsugXDZ6D5rskmdjSgjxHkQ:2lgHLk4Cc60FsJCDeTBdenOyJzCtgTZF |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
ec67929299692cb6 |
|
VISUAL
aHash
|
c3c3c3c3dfd3d3d7 |
|
VISUAL
dHash
|
0606273336363636 |
|
VISUAL
wHash
|
c3c3c3c1c3c3c3d3 |
|
VISUAL
colorHash
|
07402008040 |
|
VISUAL
cropResistant
|
0606273336363636 |
Code Analysis
Risk Score
95/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Banking
🎣 Personal Info
🔐 Credential Harvesting Forms
🔒 Obfuscation Detected
- atob
- fromCharCode
- document.write
- unicode_escape
- base64_strings