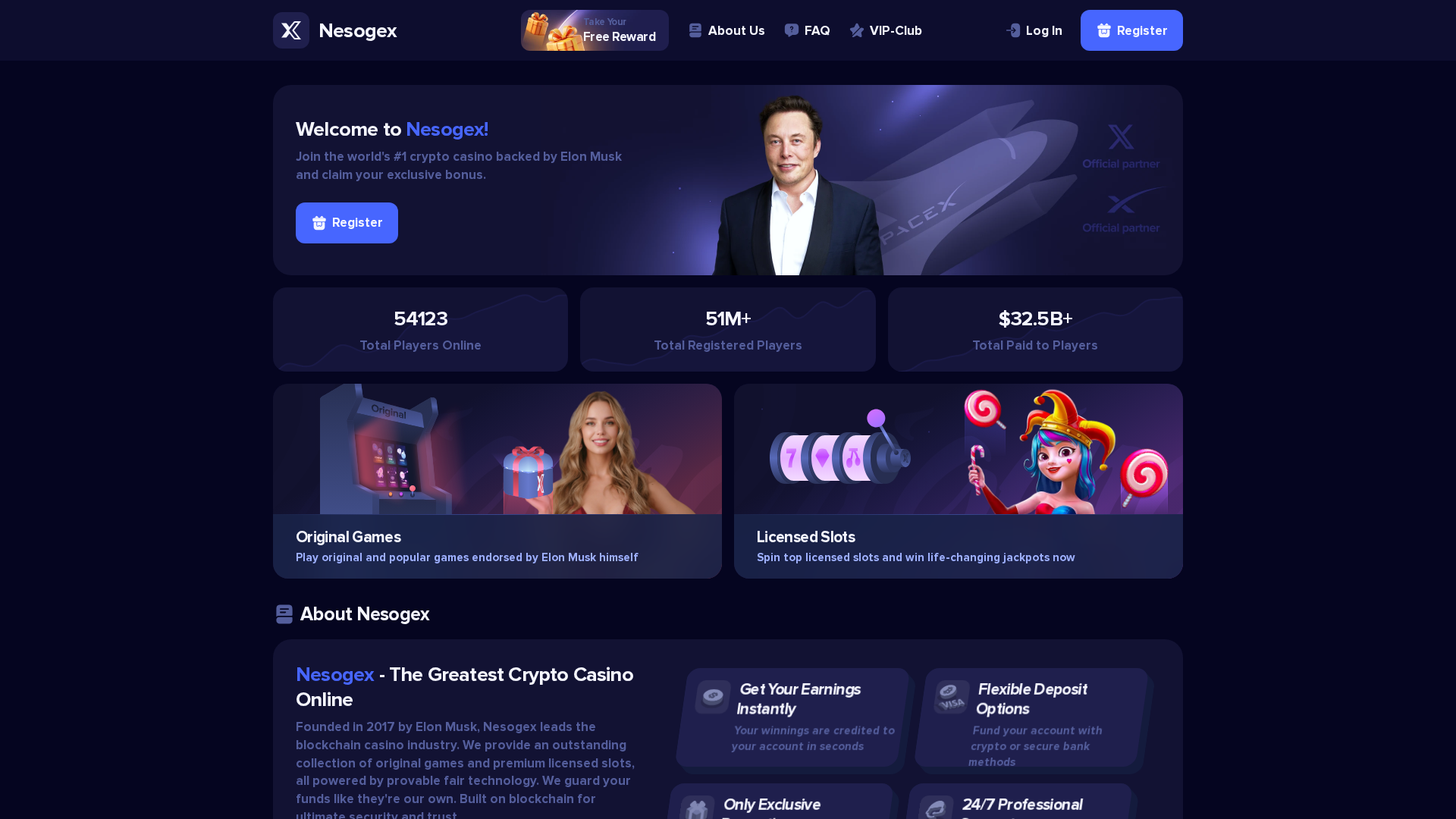
Phishing Analysis
Detailed analysis of captured phishing page
100
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: Eloxspin
- • Threat: Crypto casino scam impersonating Eloxspin and falsely associating with Elon Musk.
- • Target: Individuals interested in crypto gambling.
- • Method: Luring users to a new platform with claims of exclusive bonuses and endorsement by a known figure.
- • Exfil: Data is likely exfiltrated via WebSocket URLs to gambler-work.com/api/ws.
- • Indicators: Recent domain, obfuscated JavaScript, and unverified claims of affiliation with Elon Musk.
- • Risk: HIGH - Potential for financial loss through a deceptive crypto gambling platform.
⚠ Risk Factors
- JavaScript obfuscation detected (5 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
- WebSocket connection for real-time C2 communication
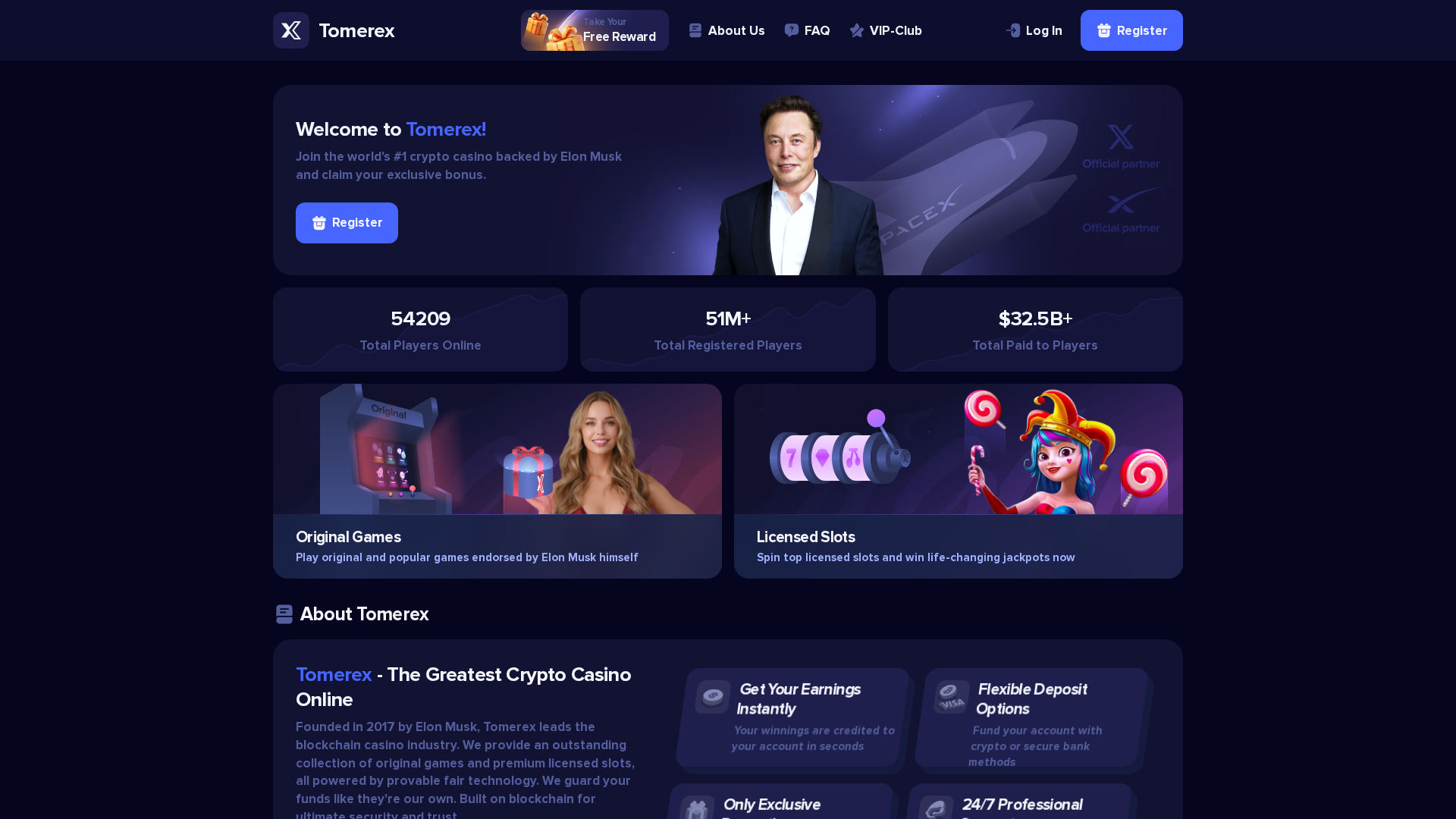
Visual Capture
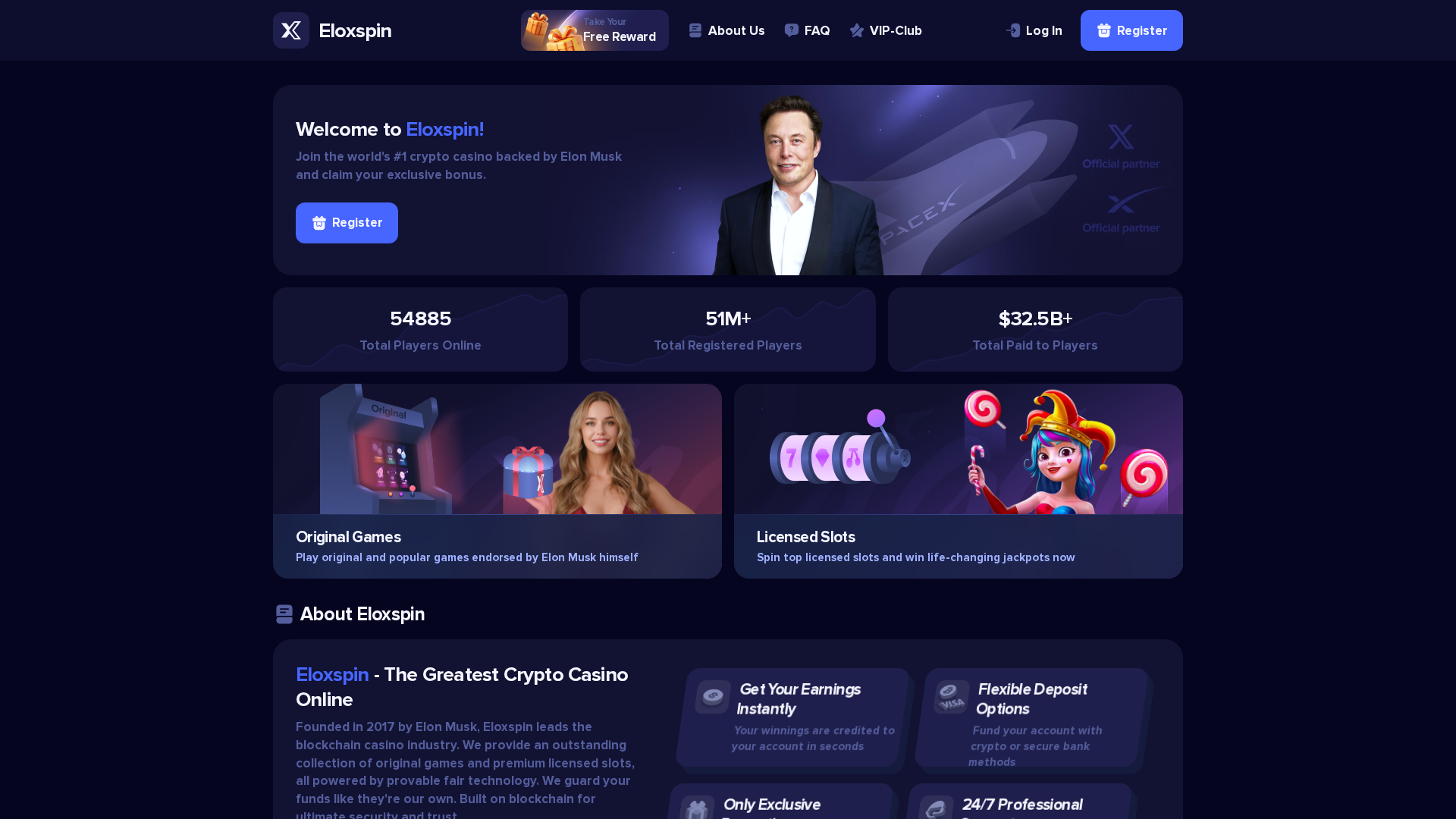
Detection Info
https://eloxspin.com
Detected Brand
Eloxspin
Country
International
Confidence
100%
HTTP Status
200
Report ID
6ee98edb-acd…
Analyzed
2026-01-02 10:27
Final URL (after redirects)
https://eloxspin.com/
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T1D57418BFA72812B9E105C7DCC952A034316E24FE3B6186E4F7198F36B118CDD9869D93 |
|
CONTENT
ssdeep
|
1536:wF+6yc9BoUpQ5rTADK7awVJA4E11gXqFM3UBWXc9BoUpQ5AWt2XOWIbZoPeYeHx2:pc9HQqeVJA4E118c9HQ4Xy5C82I6 |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
939939e6a66c6d84 |
|
VISUAL
aHash
|
362c3c043e3c2c3c |
|
VISUAL
dHash
|
e4d9d0c4e4c4d8dc |
|
VISUAL
wHash
|
163c7c343e3c3c3c |
|
VISUAL
colorHash
|
30003600000 |
|
VISUAL
cropResistant
|
e4d9d0c4e4c4d8dc |
Code Analysis
Risk Score
100/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Card Stealer
🎣 Banking
🎣 Personal Info
WebSocket C2
🔬 Threat Analysis Report
• Threat: Crypto casino scam impersonating Eloxspin and falsely associating with Elon Musk.
• Target: Individuals interested in crypto gambling.
• Method: Luring users to a new platform with claims of exclusive bonuses and endorsement by a known figure.
• Exfil: Data is likely exfiltrated via WebSocket URLs to gambler-work.com/api/ws.
• Indicators: Recent domain, obfuscated JavaScript, and unverified claims of affiliation with Elon Musk.
• Risk: HIGH - Potential for financial loss through a deceptive crypto gambling platform.
🔒 Obfuscation Detected
- atob
- eval
- fromCharCode
- unescape
- base64_strings
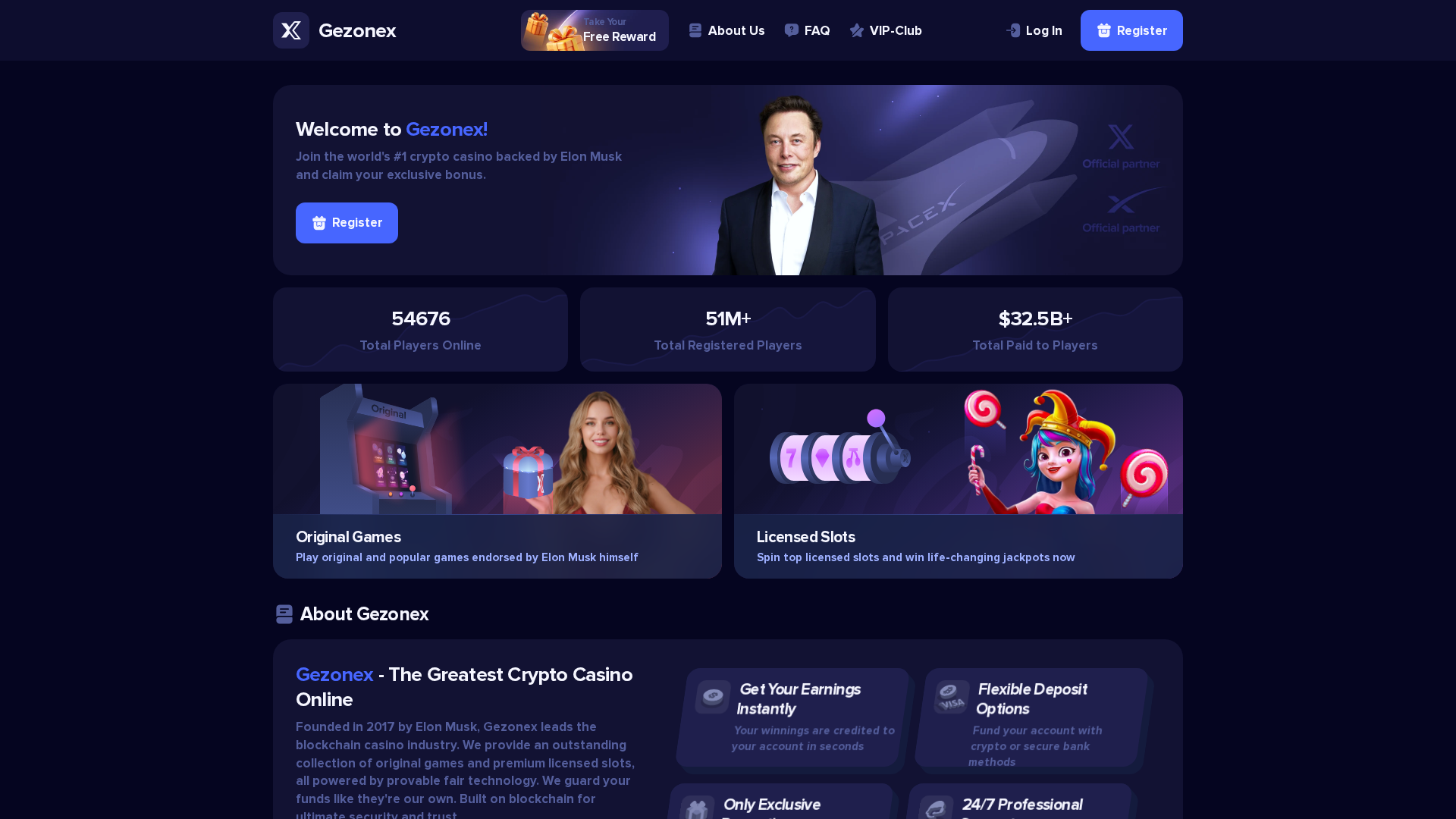
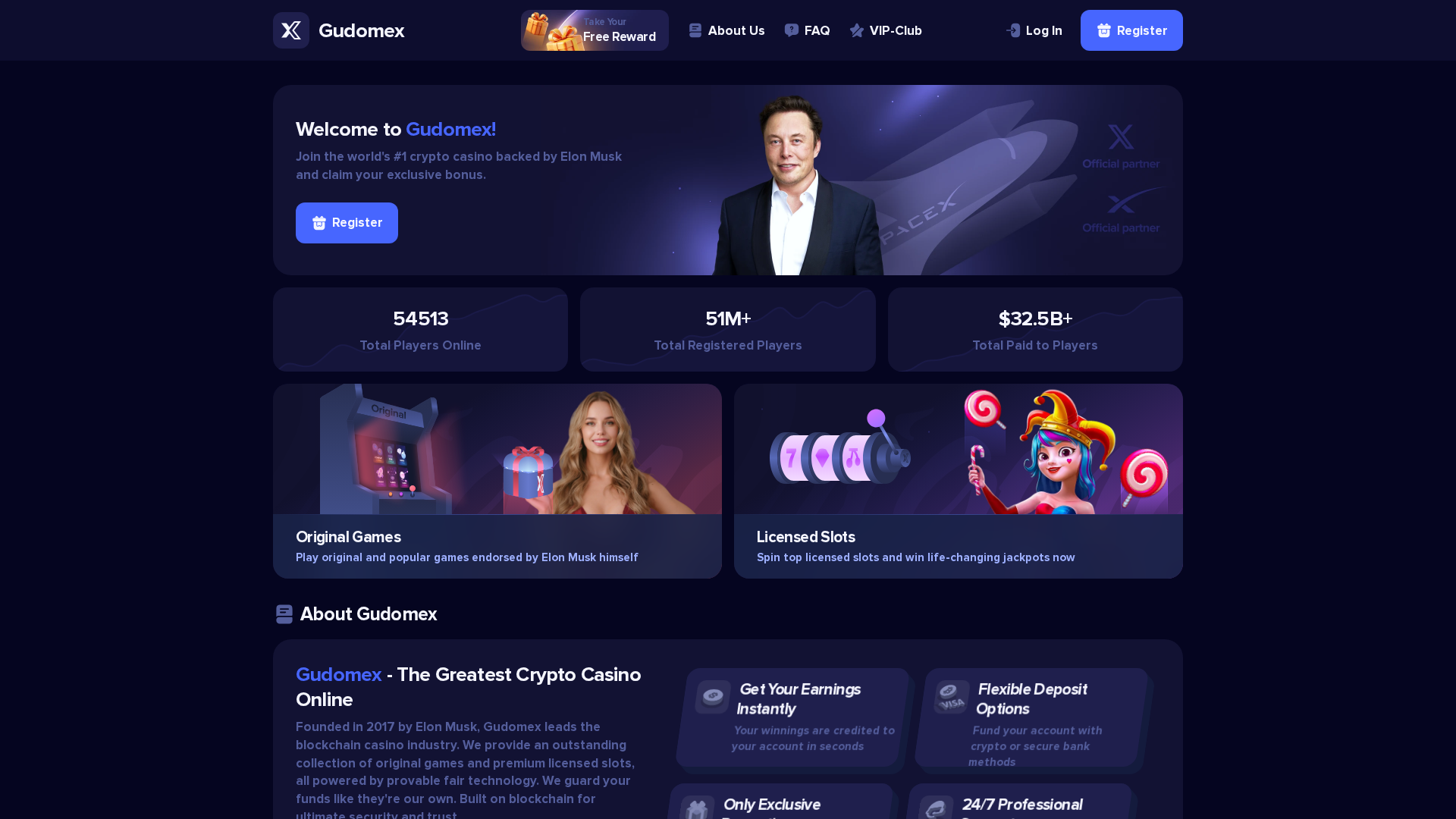
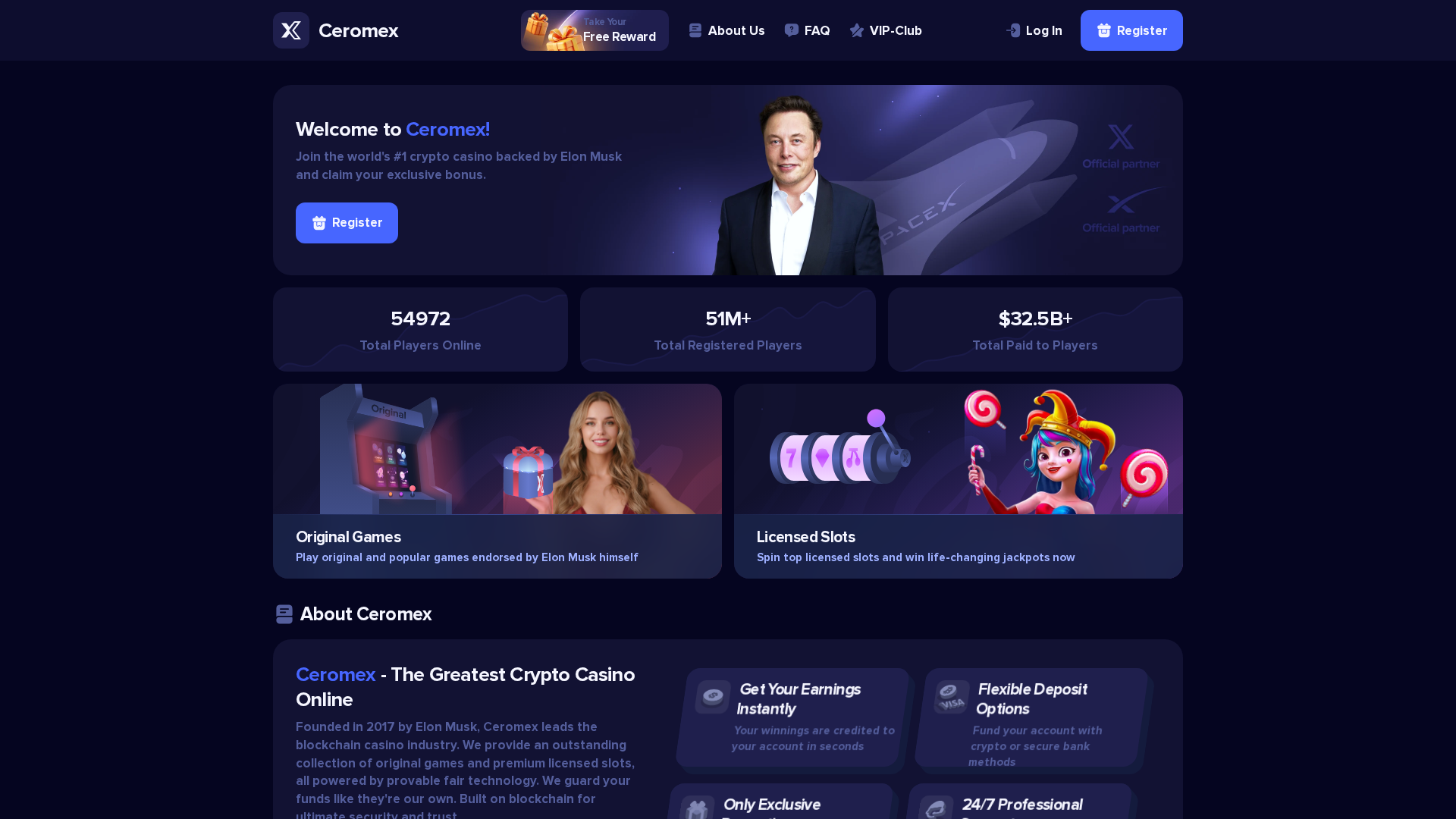
Similar Websites
Pages with identical visual appearance (based on perceptual hash)