
Phishing Analysis
Detailed analysis of captured phishing page
85
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: Exodus
- • Threat: Phishing site impersonating Exodus Pay app
- • Target: Exodus users globally
- • Method: Fake download button leading to potential malware
- • Exfil: Unknown, but likely collects user data or installs malware
- • Indicators: Domain mismatch, unfamiliar TLD, suspicious download
- • Risk: HIGH - Potential malware infection and data theft
⚠ Risk Factors
- Banking fraud indicators detected
Visual Capture
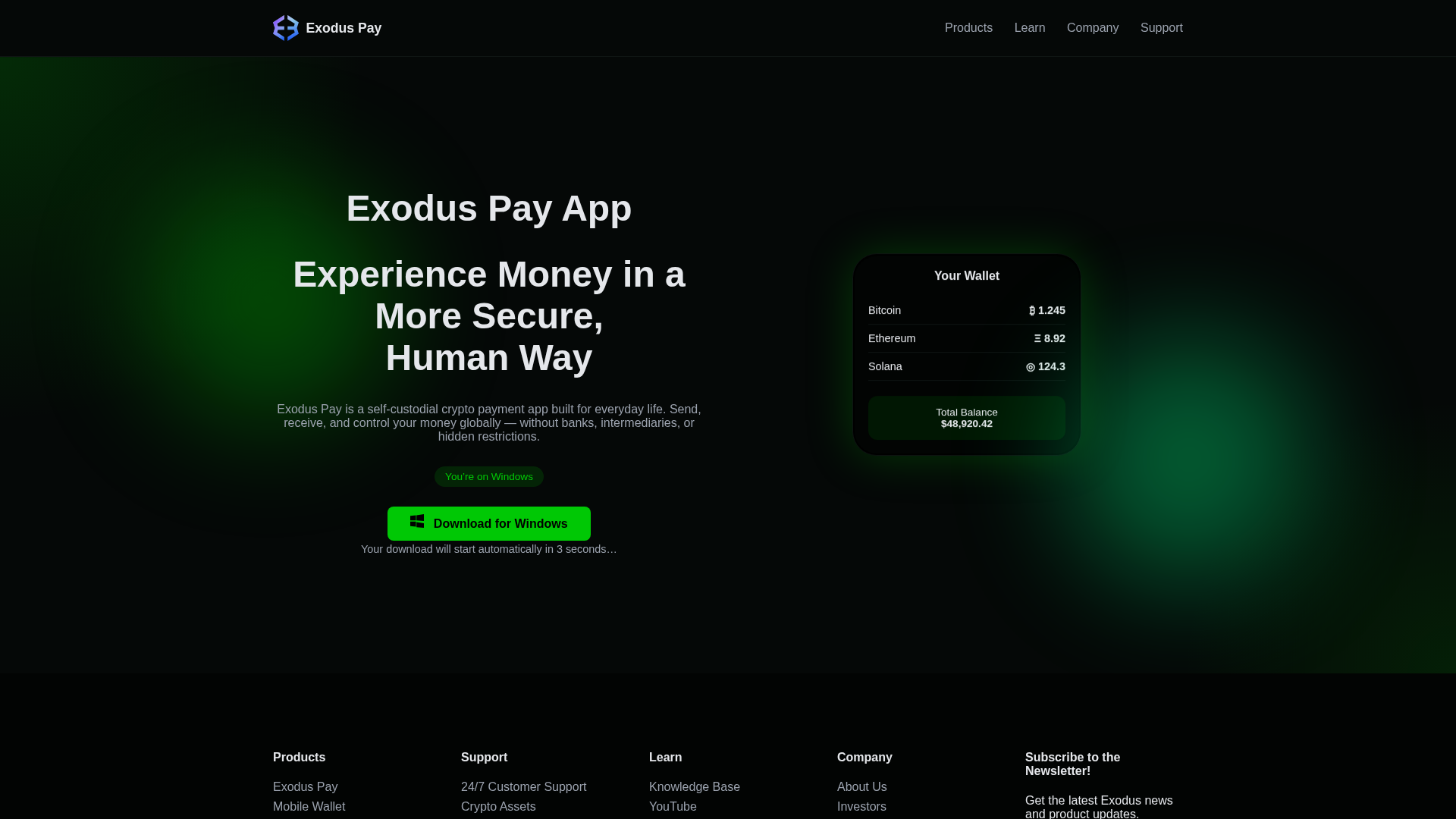
Detection Info
https://officialexodusdownload.live
Detected Brand
Exodus
Country
International
Confidence
95%
HTTP Status
200
Report ID
71fac2eb-bc4…
Analyzed
2026-01-11 06:32
Final URL (after redirects)
https://officialexodusdownload.live/
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T144B1A7749120B23F40C282D49BA65BEBA39681C4FA560F5656FCC72C5FE7E44CC32A68 |
|
CONTENT
ssdeep
|
96:nXACaAcZLSkbR+xofwU7chJWZ5+CQDlFyD:QbUir4IchJU51cnyD |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
e7e27a3d954ac700 |
|
VISUAL
aHash
|
00e0f0f637330000 |
|
VISUAL
dHash
|
1c00c4cece6e93e4 |
|
VISUAL
wHash
|
c0e0f6ff77370104 |
|
VISUAL
colorHash
|
38000000e00 |
|
VISUAL
cropResistant
|
1c00c4cece6e93e4 |
Code Analysis
Risk Score
85/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Banking
🔬 Threat Analysis Report
• Threat: Phishing site impersonating Exodus Pay app
• Target: Exodus users globally
• Method: Fake download button leading to potential malware
• Exfil: Unknown, but likely collects user data or installs malware
• Indicators: Domain mismatch, unfamiliar TLD, suspicious download
• Risk: HIGH - Potential malware infection and data theft