
Phishing Analysis
Detailed analysis of captured phishing page
68
Risk Score
Medium Risk
Threat Level: ALTO
• Impersonating: Microsoft
- • Threat: Credential harvesting phishing kit
- • Target: Microsoft users
- • Method: Fake login form stealing email, phone, or Skype credentials
- • Exfil: Potential data exfiltration via obfuscated JavaScript
- • Indicators: Domain mismatch, obfuscation detected, form present
- • Risk: HIGH - Immediate credential theft
⚠ Risk Factors
- Brand impersonation of Microsoft on non-official domain
- Contains 1 credential harvesting form(s)
- Credential harvesting indicators detected
Visual Capture
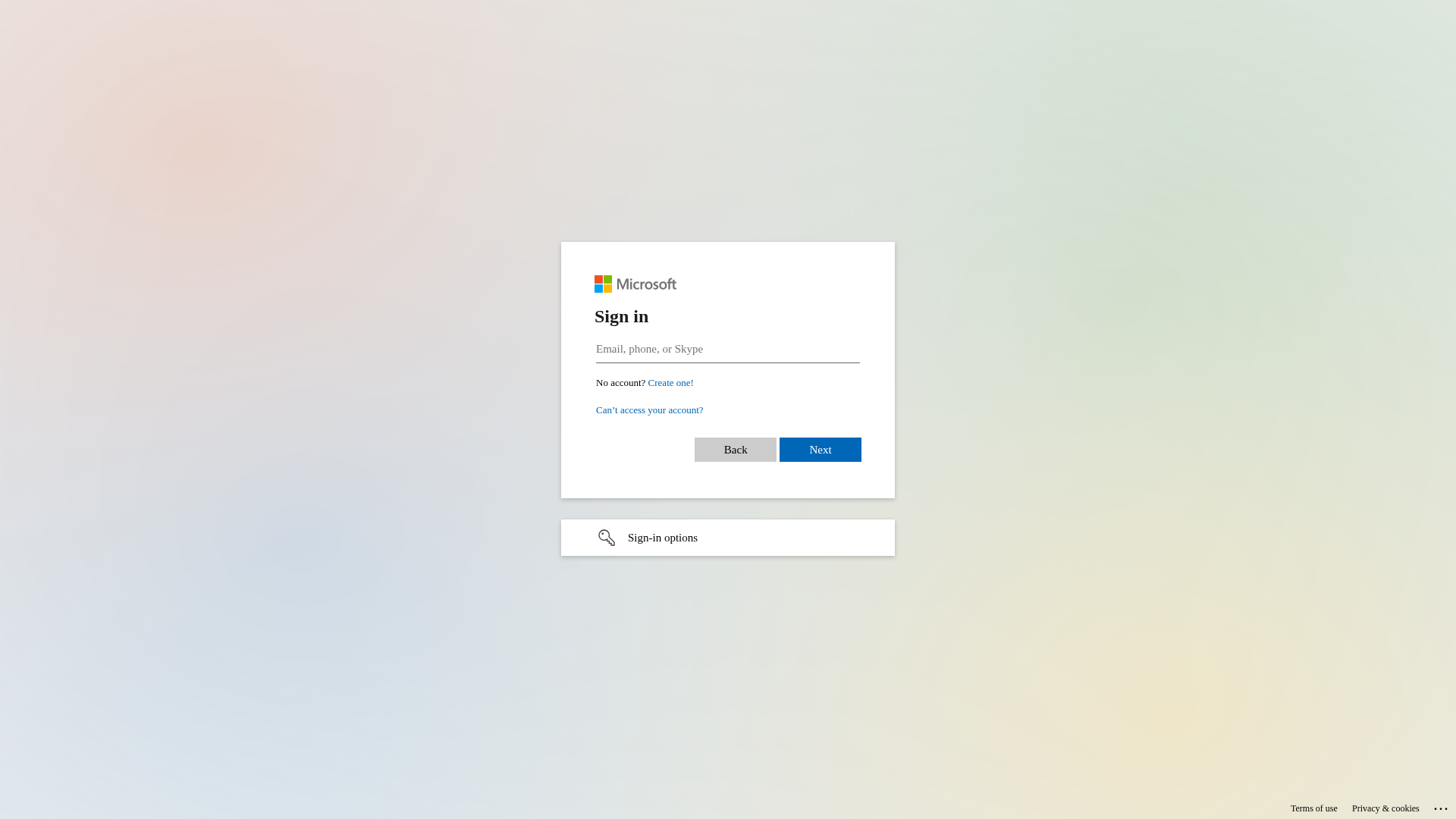
Detection Info
https://inner.website/y023e62ecc47bd45efl8a100d2888677a163.html
Detected Brand
Microsoft
Country
International
Confidence
95%
HTTP Status
200
Report ID
7dbaf205-042…
Analyzed
2026-01-09 14:20
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T168D1113160409D3712C3C6C8B3B56B1B3784C205DE8757AA57E8C39D4EFBE61CC19292 |
|
CONTENT
ssdeep
|
96:qvWFAzQgIeu0nPK/AmvUAK5KbdPs/l+veRzKDafEAD9NltZdSsTZS4C5QQOGAM2B:3gI0/lnRWDeZ9NVhC5UEIf |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
9c497326cc99d966 |
|
VISUAL
aHash
|
180018181d1f1f9f |
|
VISUAL
dHash
|
7161713325727d38 |
|
VISUAL
wHash
|
191818181f1f1fff |
|
VISUAL
colorHash
|
07000000180 |
|
VISUAL
cropResistant
|
7161713325727d38 |
Code Analysis
Risk Score
68/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🔬 Threat Analysis Report
• Threat: Credential harvesting phishing kit
• Target: Microsoft users
• Method: Fake login form stealing email, phone, or Skype credentials
• Exfil: Potential data exfiltration via obfuscated JavaScript
• Indicators: Domain mismatch, obfuscation detected, form present
• Risk: HIGH - Immediate credential theft
🔒 Obfuscation Detected
- atob
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
Microsoft
http://inner.website/pf634f4f2hd8ab4b242bbe81b751df04e613.ht...
Jan 10, 2026
Microsoft
https://channelhub.online/i726b304461aba42d8t9fdfa816j7fa03d...
Jan 10, 2026
Microsoft
http://channelhub.online/ia7581e5e63fc64c89ta0b064c8j1210e4f...
Jan 10, 2026
Microsoft
https://channelhub.online/ia7581e5e63fc64c89ta0b064c8j1210e4...
Jan 10, 2026
Microsoft
http://inner.website/pcdde712fh20d94f742bc3a42131444b38b5.ht...
Jan 09, 2026
Scan History for inner.website
Found 10 other scans for this domain
-
http://inner.website/pf634f4f2hd8ab4b242bbe81b751d...
http://inner.website/pcdde712fh20d94f742bc3a421314...
https://inner.website/yba964a42c4b7d4e62la770d4a18...
https://inner.website/yd0dd9503c13e84494l82ec464e8...
https://inner.website/p8f95d256hfeeb436d2a4b540cc1...
https://inner.website/p0a7c407fh1ace49e52910b24141...
https://inner.website/p3f8f8768hbcaf416d2b32055461...
https://inner.website/p6395e104ha23c401428bc1e9711...
https://inner.website/pf7801534ha1ad4577288b219741...
https://inner.website/p4c15006eh53e445ca2a8512dbe1...