Phishing Analysis
Detailed analysis of captured phishing page
100
Risk Score
High Risk
Threat Level: ALTO
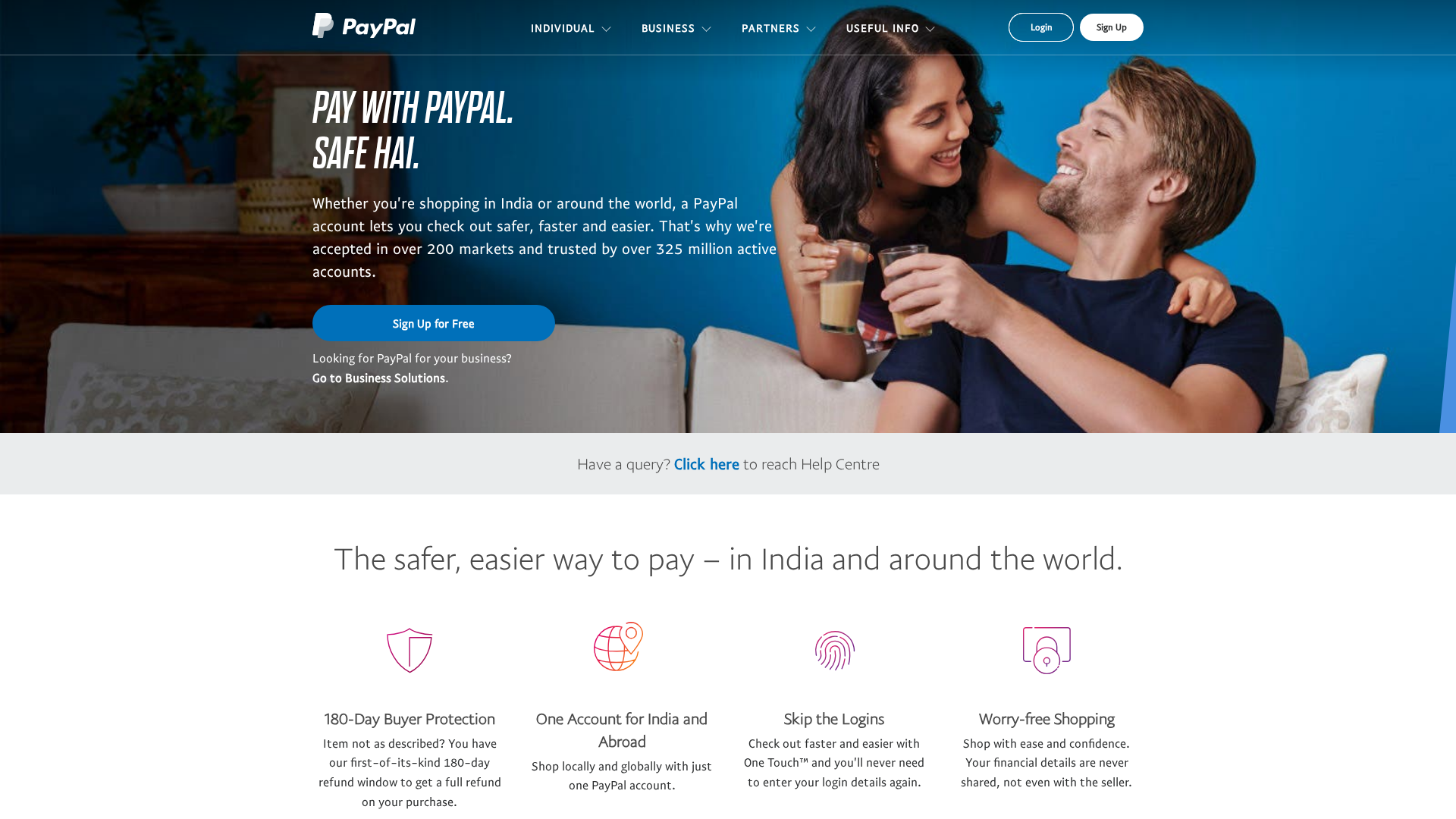
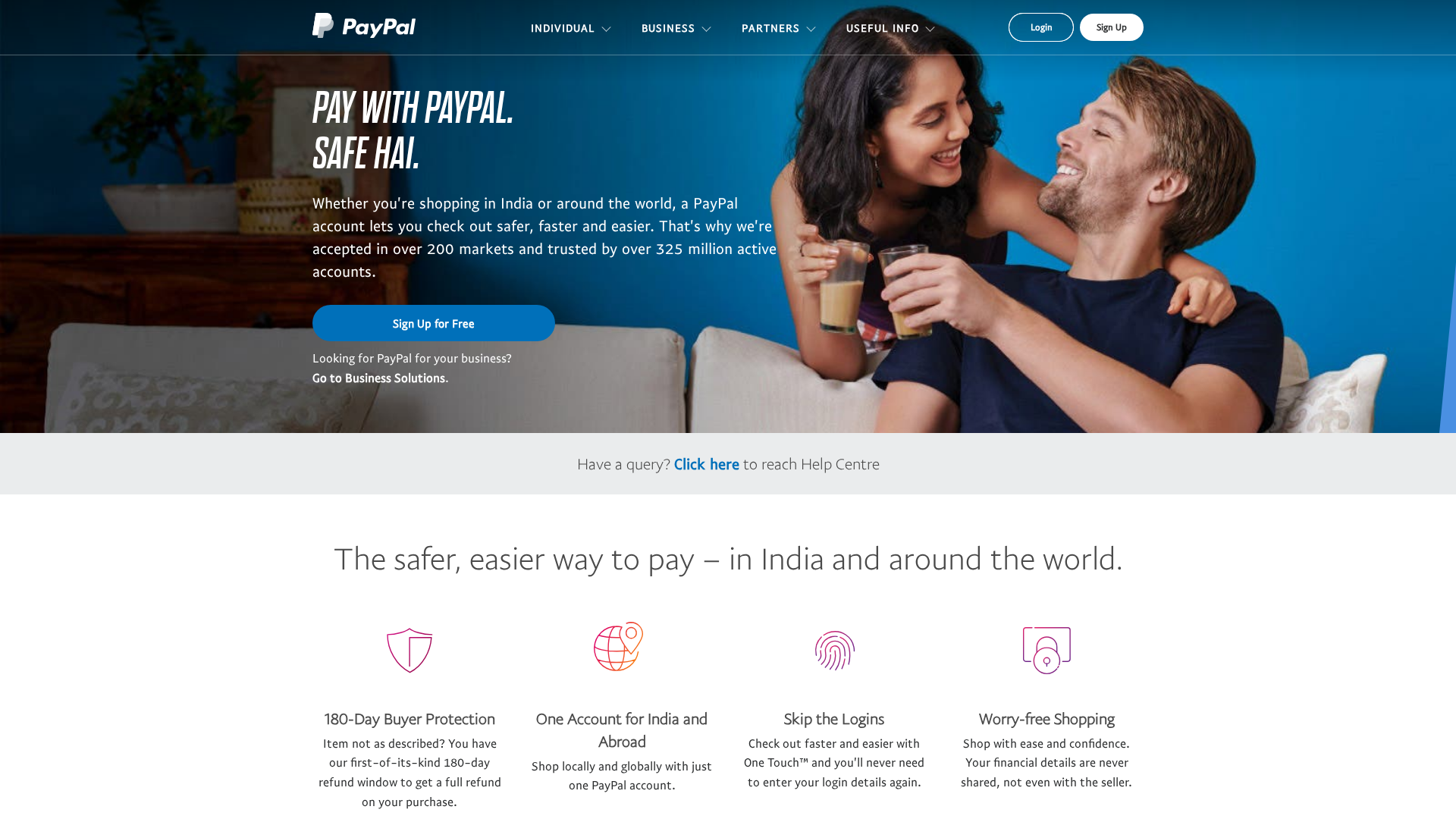
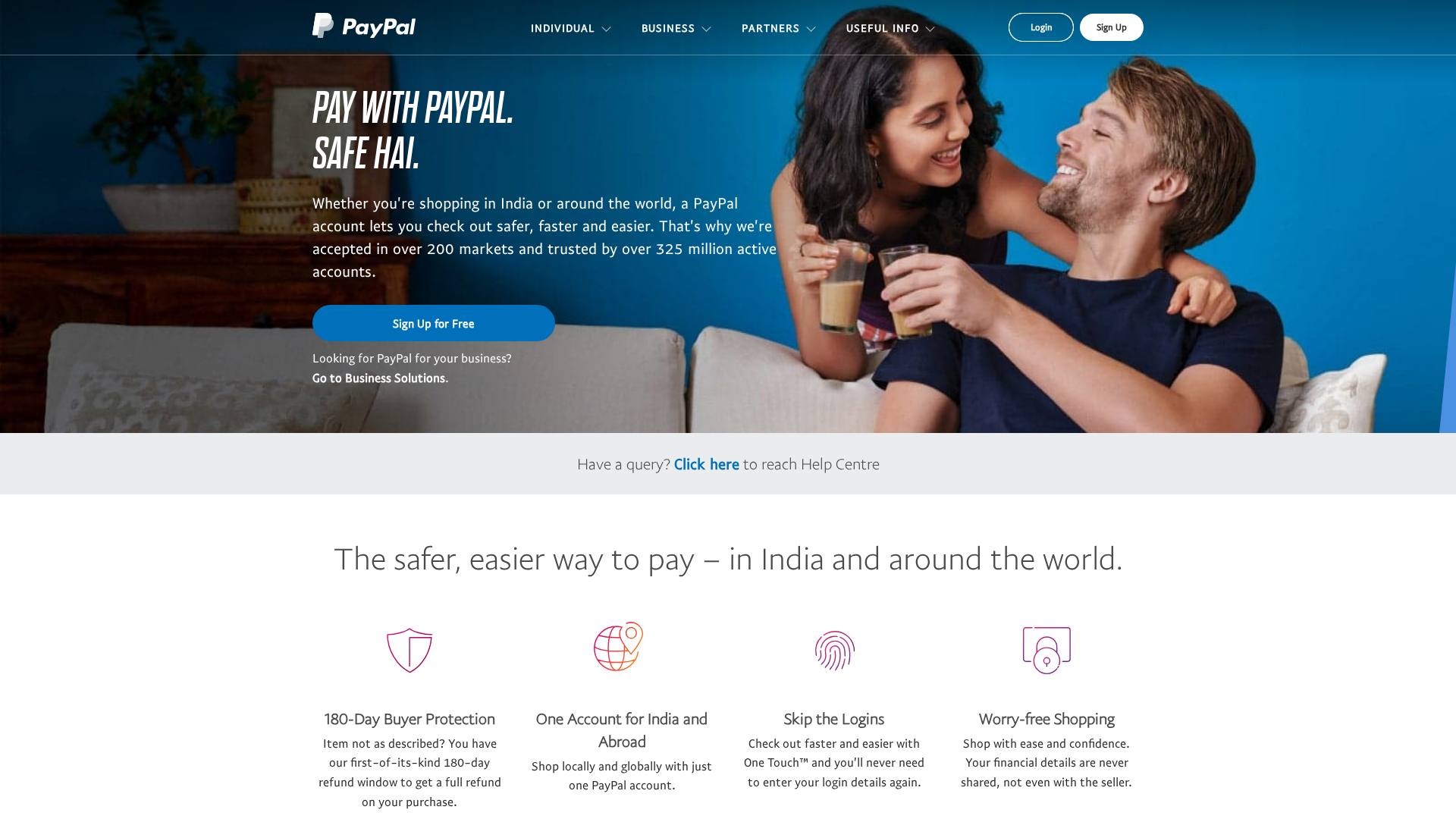
• Impersonating: PayPal
- • Threat: Brand impersonation phishing.
- • Target: PayPal users.
- • Method: The site uses PayPal's branding to appear legitimate.
- • Exfil: N/A, there is no form to exfiltrate from in the cropped image.
- • Indicators: Domain mismatch (not paypal.com), PayPal logo.
- • Risk: HIGH - Attempt to deceive users by impersonating a known brand.
⚠ Risk Factors
- Brand impersonation of PayPal on non-official domain
- Known phishing kit detected: angler
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
No screenshot available
Detection Info
http://638ca12d-ba2f-451c-8418-faf56b7de7ff.htmlcomponentservice.com/get_draft?id=638ca1_14694f4a84161543466426a12288de1a.html
Detected Brand
PayPal
Country
International
Confidence
100%
HTTP Status
200
Report ID
8144e717-4d8…
Analyzed
2025-12-20 15:35
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T18823EEFB1040AD2E5316E1CE683A7709E193530ECEA65CD5FBA84FF35686B73941182B |
|
CONTENT
ssdeep
|
384:6scndyIKd5u1IUj1fpI7InwszPK1mBpCFIeWVVwsk3fMa86PznRTH:6Jn/NznhYFrWQ1fMZ6bnRD |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
8406b6f74909babd |
|
VISUAL
aHash
|
00000000ffffffff |
|
VISUAL
dHash
|
d4d5f5f1b20c3223 |
|
VISUAL
wHash
|
00000000ffffffff |
|
VISUAL
colorHash
|
0e2000001c0 |
|
VISUAL
cropResistant
|
64d4c0a0c6ec78d0,f9f5f20d120a2323,f4ddddf5f6f9f5f2 |
Code Analysis
Risk Score
100/100
Threat Level
ALTO
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Card Stealer
🎣 Banking
🎣 Personal Info
🔬 Threat Analysis Report
• Threat: Brand impersonation phishing.
• Target: PayPal users.
• Method: The site uses PayPal's branding to appear legitimate.
• Exfil: N/A, there is no form to exfiltrate from in the cropped image.
• Indicators: Domain mismatch (not paypal.com), PayPal logo.
• Risk: HIGH - Attempt to deceive users by impersonating a known brand.
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
Scan History for 638ca12d-ba2f-451c-8418-faf56b7de7ff.htmlcomponentservice.com
Found 3 other scans for this domain