Phishing Analysis
Detailed analysis of captured phishing page
95
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: DPD
- • Threat: Package delivery scam phishing
- • Target: DPD customers
- • Method: Informs users about a failed delivery and prompts them to reschedule, potentially leading to credential theft or malware installation.
- • Exfil: Unknown, potentially form submissions or redirects to malicious sites.
- • Indicators: Domain mismatch, urgency, requests for rescheduling.
- • Risk: HIGH - Potential credential theft or malware installation.
⚠ Risk Factors
- Brand impersonation of DPD on non-official domain
- Contains 4 credential harvesting form(s)
- JavaScript obfuscation detected (5 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
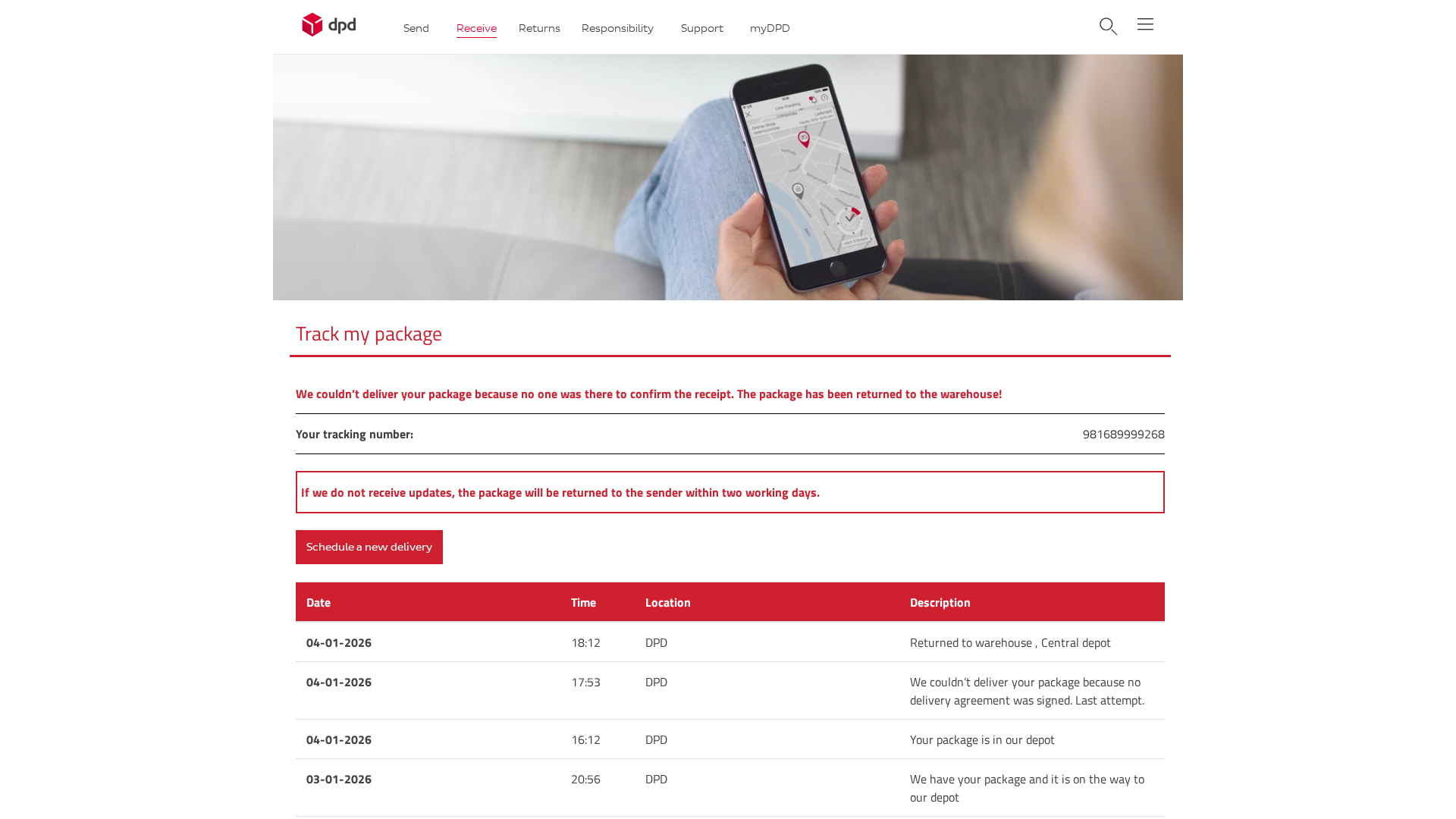
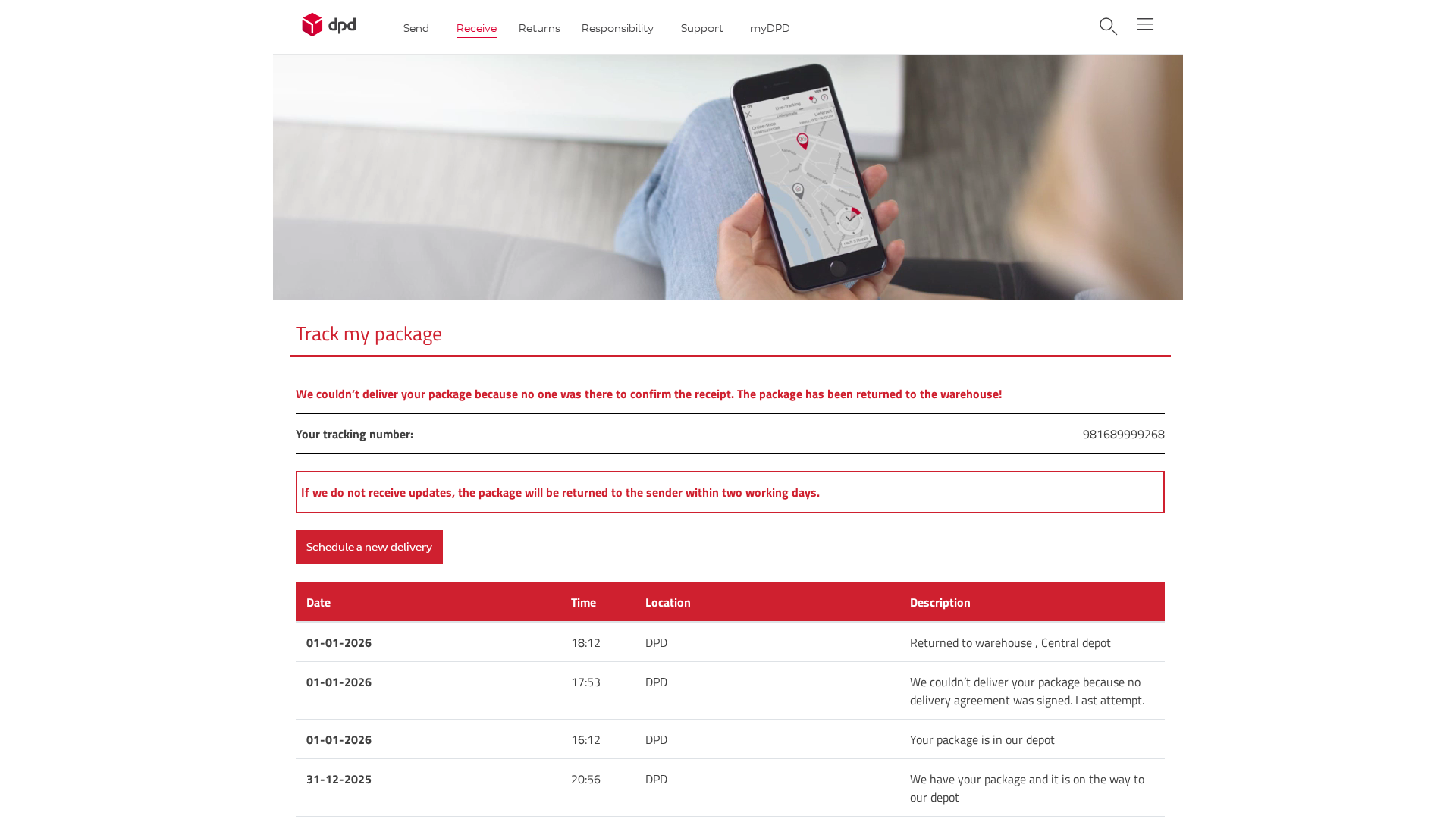
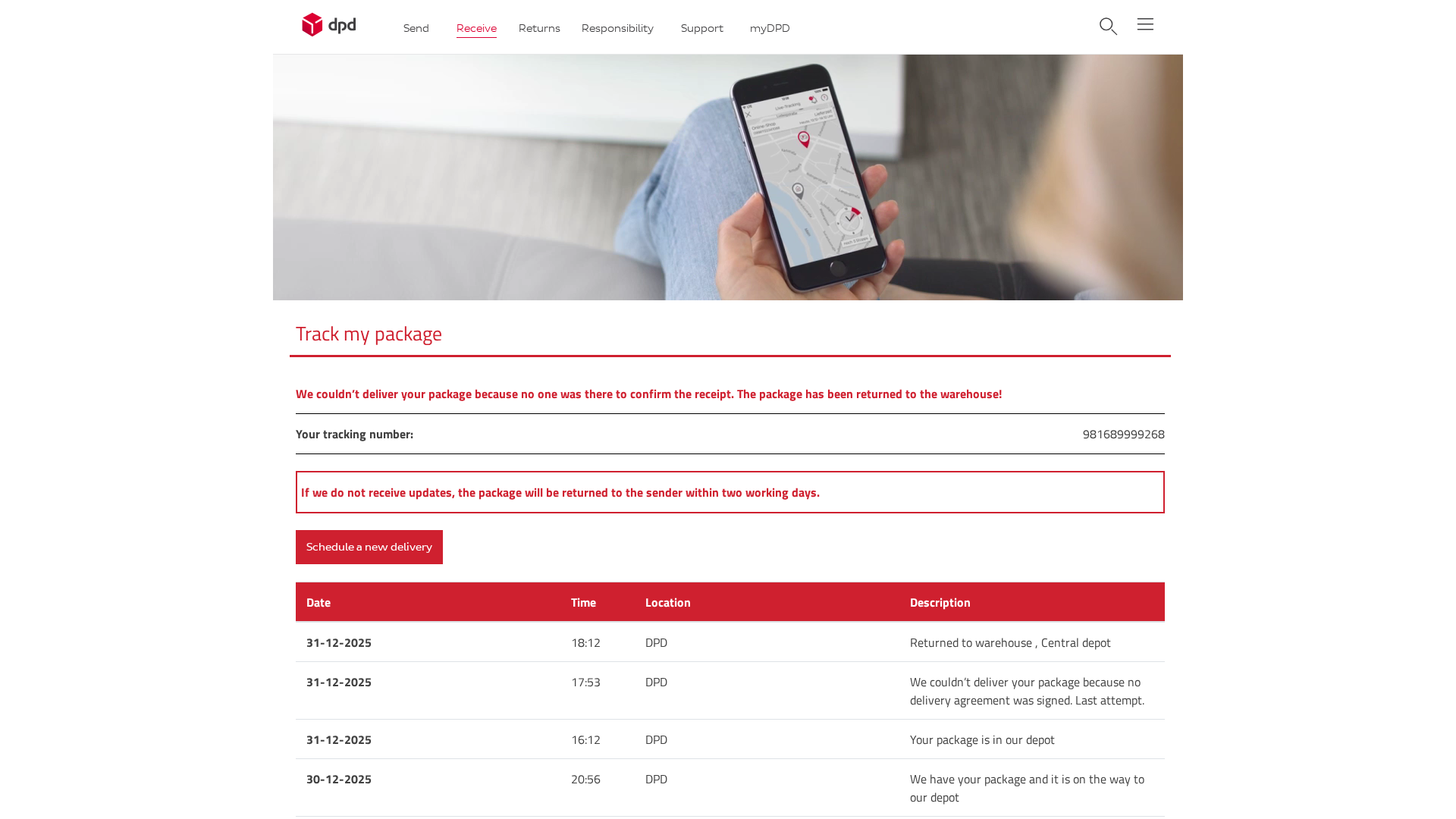
Visual Capture
Detection Info
https://212-227-48-175.cprapid.com/de/update.php
Detected Brand
DPD
Country
International
Confidence
100%
HTTP Status
200
Report ID
853661fd-4d5…
Analyzed
2026-01-02 00:10
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T1E6B2017094B5B63F009F7391A7386709A3D39383CB520BE567F8936D5B8AE84DC23169 |
|
CONTENT
ssdeep
|
192:bixLoxwz77qKHv/ySchJrVUmvGkoRXTCReWyRMOsUFf9kIT/JO:mx8xw7pvKpJrVUIGk0+TxFUH/JO |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
ed6dc19a92963c92 |
|
VISUAL
aHash
|
f1c1c1ffff83c3ff |
|
VISUAL
dHash
|
23030727392b1342 |
|
VISUAL
wHash
|
e18181d7c781c3fb |
|
VISUAL
colorHash
|
07200000006 |
|
VISUAL
cropResistant
|
23030727392b1342,67e5258787c39767,0000db6464649b24 |
Code Analysis
Risk Score
95/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Banking
🎣 Personal Info
🔬 Threat Analysis Report
• Threat: Package delivery scam phishing
• Target: DPD customers
• Method: Informs users about a failed delivery and prompts them to reschedule, potentially leading to credential theft or malware installation.
• Exfil: Unknown, potentially form submissions or redirects to malicious sites.
• Indicators: Domain mismatch, urgency, requests for rescheduling.
• Risk: HIGH - Potential credential theft or malware installation.
🔐 Credential Harvesting Forms
🔒 Obfuscation Detected
- atob
- eval
- fromCharCode
- unescape
- base64_strings
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
Scan History for 212-227-48-175.cprapid.com
Found 6 other scans for this domain