
Phishing Analysis
Detailed analysis of captured phishing page
100
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: mweb
⚠ Risk Factors
- Brand impersonation of mweb on non-official domain
- Contains 6 form(s) with JavaScript submission
- JavaScript obfuscation detected (7 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
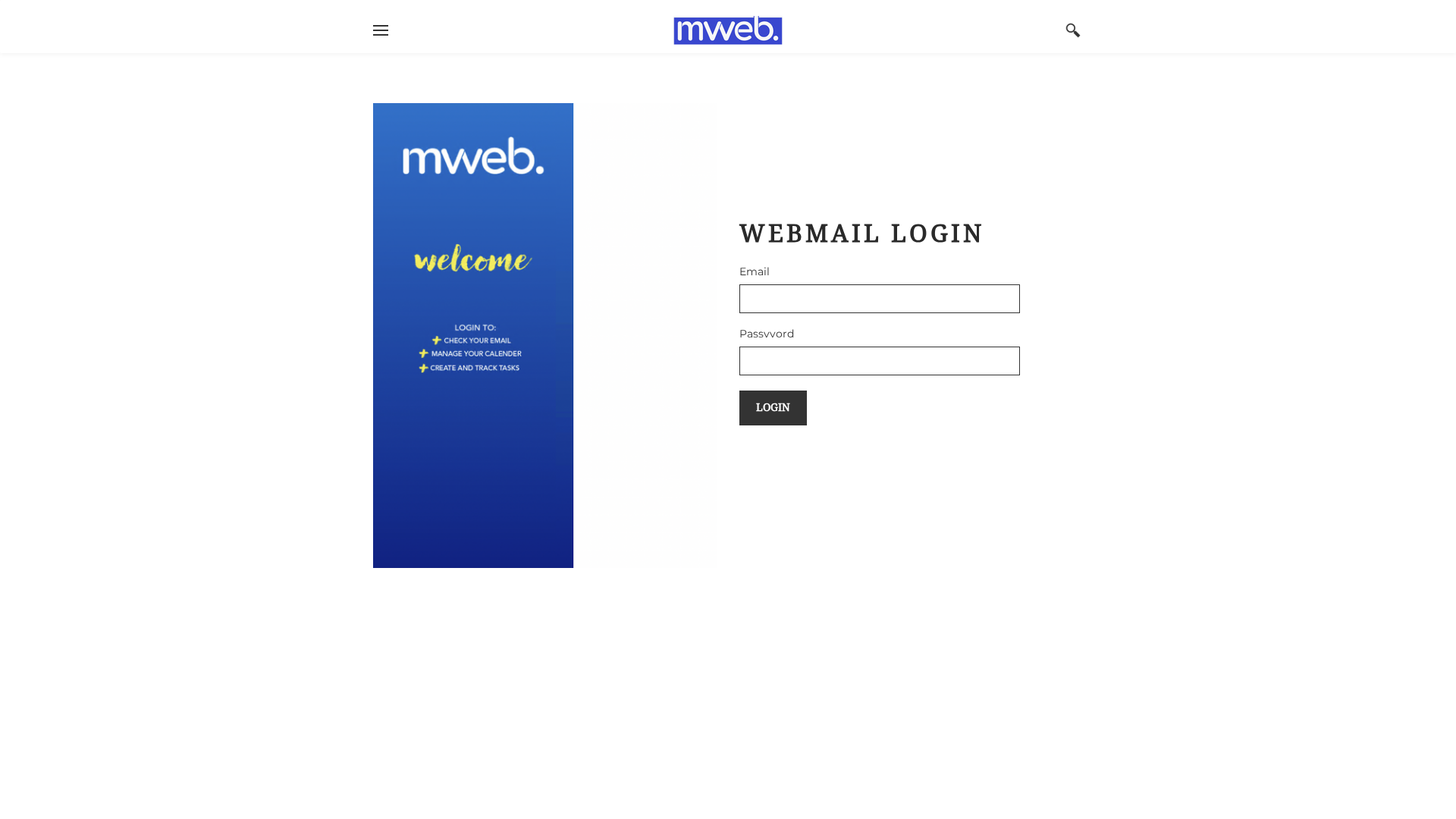
Detection Info
https://mweb-passwordnotices.weebly.com/
Detected Brand
mweb
Country
South Africa
Confidence
100%
HTTP Status
200
Report ID
85c7ac97-1c4…
Analyzed
2026-01-07 08:22
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T1FAF121F1C414DD3A436285D5FBF13B4BB6D1C346DB02094453F883AB9BDAC50CA56A9A |
|
CONTENT
ssdeep
|
96:nkWVf6zYh7MSnLtVSTahUSPRttb8v67MYXwytfI7FpfBFqyX+HFe+X6X/DbC8Elc:kWVf6zYhhnOU/l8iIowy5I7LKEXHFElc |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
b838c7c726c73934 |
|
VISUAL
aHash
|
ffcfcfcfcfcfffff |
|
VISUAL
dHash
|
2ab4b6b6bcb40030 |
|
VISUAL
wHash
|
00cfc3c3040c3030 |
|
VISUAL
colorHash
|
070000001c0 |
|
VISUAL
cropResistant
|
2ab4b6b6bcb40030,cce8e9f1e9074100 |
Code Analysis
Risk Score
100/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Card Stealer
🎣 Banking
🎣 Personal Info
🔐 Credential Harvesting Forms
🔒 Obfuscation Detected
- atob
- eval
- fromCharCode
- unescape
- hex_escape
- unicode_escape
- base64_strings