
Phishing Analysis
Detailed analysis of captured phishing page
100
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: Avalabs
- • Threat: Cryptocurrency phishing site
- • Target: AVAX and Solana users
- • Method: Fake comparison page to mislead users
- • Exfil: Potential data exfiltration via WebSocket URLs
- • Indicators: Recent domain, obfuscated JavaScript, unofficial domain
- • Risk: HIGH - Potential for credential theft or malware distribution
⚠ Risk Factors
- JavaScript obfuscation detected (5 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
- WebSocket connection for real-time C2 communication
Visual Capture
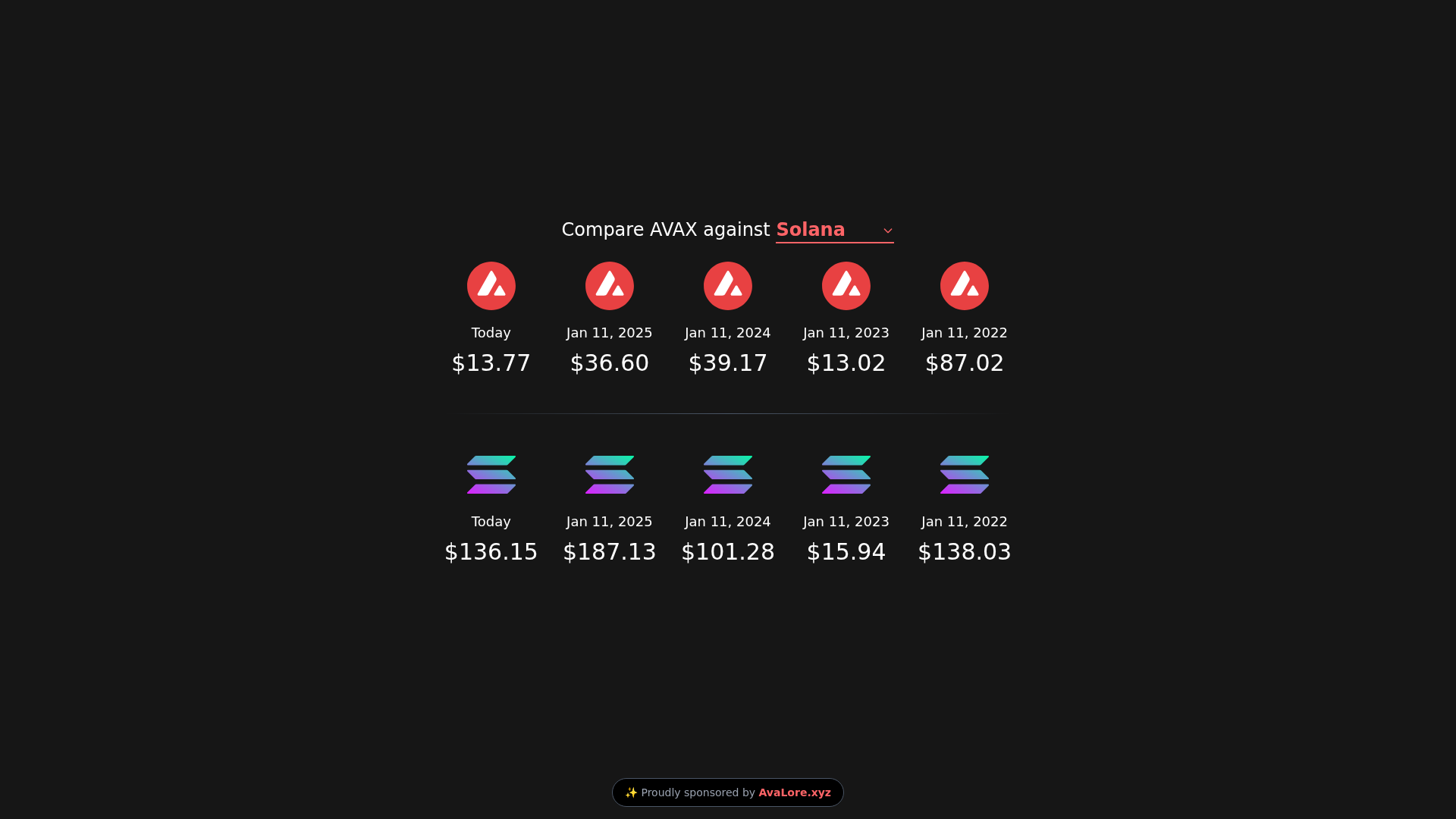
Detection Info
https://didavalabsdeposit30milliontocoinbaseprimetoday.xyz
Detected Brand
Avalabs
Country
International
Confidence
100%
HTTP Status
200
Report ID
8c132980-c90…
Analyzed
2026-01-11 06:38
Final URL (after redirects)
https://www.didavalabsdeposit30milliontocoinbaseprimetoday.xyz/
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T11EF32CB43595F4930BB746A7806F0002F3385D3F140E5960A3A5ECDE766989EA0F3F9A |
|
CONTENT
ssdeep
|
1536:546/5TGtihLfa6Ih6hARs5Vx2t8qL2cJCSFeyCRFXmCk4vM9sPatObuur8EyWFvO:NhLfSQORgV86I4p8r |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
9ecc6133339a9acc |
|
VISUAL
aHash
|
00003c3c3c3c0000 |
|
VISUAL
dHash
|
0016716969691608 |
|
VISUAL
wHash
|
30303c3c3c3c0000 |
|
VISUAL
colorHash
|
38001000003 |
|
VISUAL
cropResistant
|
0016716969691608 |
Code Analysis
Risk Score
100/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Card Stealer
🎣 Banking
🎣 Personal Info
WebSocket C2
🔬 Threat Analysis Report
• Threat: Cryptocurrency phishing site
• Target: AVAX and Solana users
• Method: Fake comparison page to mislead users
• Exfil: Potential data exfiltration via WebSocket URLs
• Indicators: Recent domain, obfuscated JavaScript, unofficial domain
• Risk: HIGH - Potential for credential theft or malware distribution
🔒 Obfuscation Detected
- atob
- fromCharCode
- unescape
- unicode_escape
- base64_strings