
Phishing Analysis
Detailed analysis of captured phishing page
65
Risk Score
Medium Risk
Threat Level: ALTO
• Impersonating: DPD
- • Threat: Package tracking phishing targeting DPD customers.
- • Target: DPD customers globally.
- • Method: Falsely claims delivery issues and requests updates to redirect packages.
- • Exfil: Potentially collects tracking number and related details.
- • Indicators: IP address as domain, non-matching URL.
- • Risk: HIGH - Attempting to harvest package information for malicious purposes.
⚠ Risk Factors
- Brand impersonation of DPD on non-official domain
- Contains 2 credential harvesting form(s)
- Credential harvesting indicators detected
- Banking fraud indicators detected
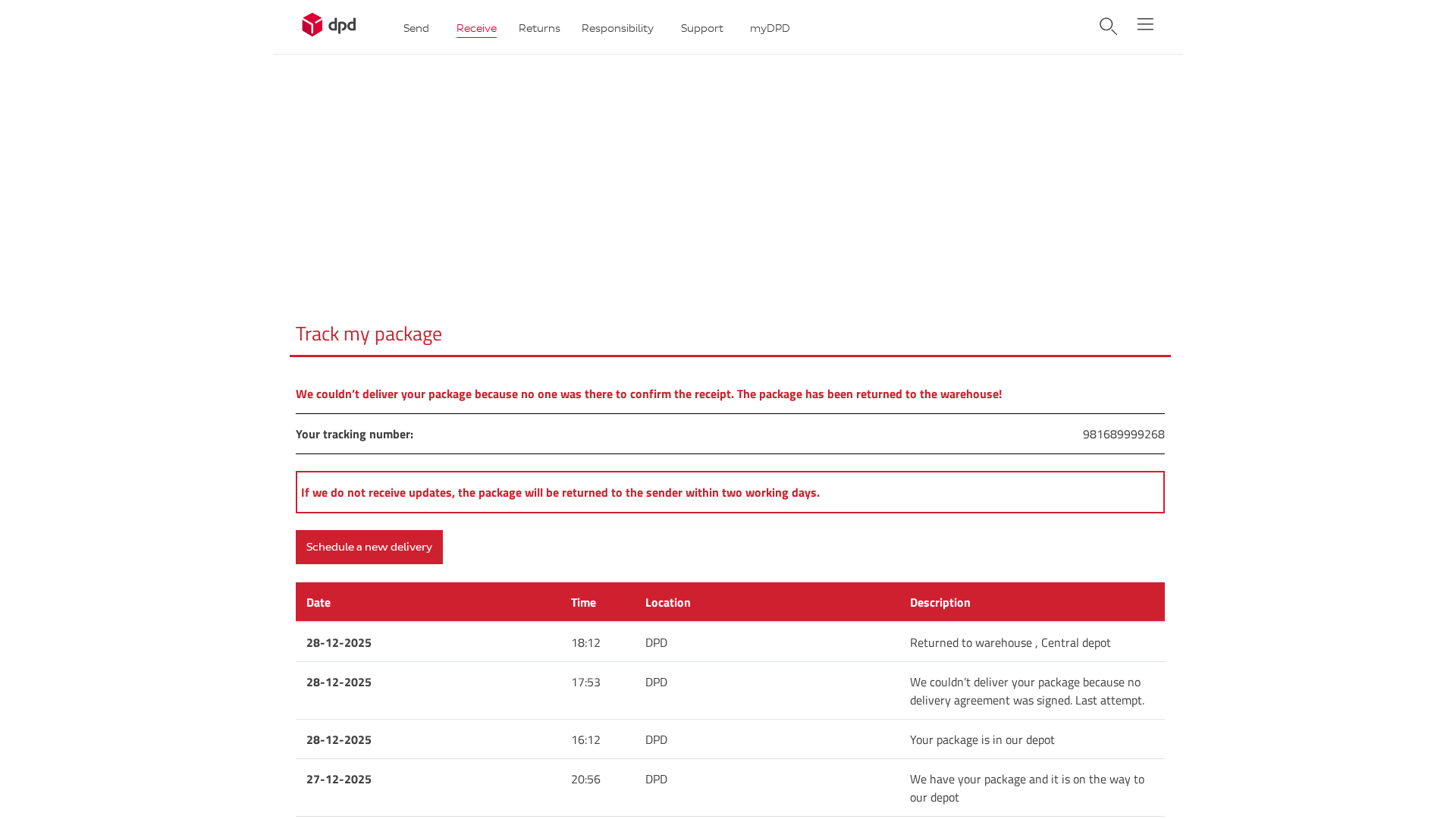
Visual Capture
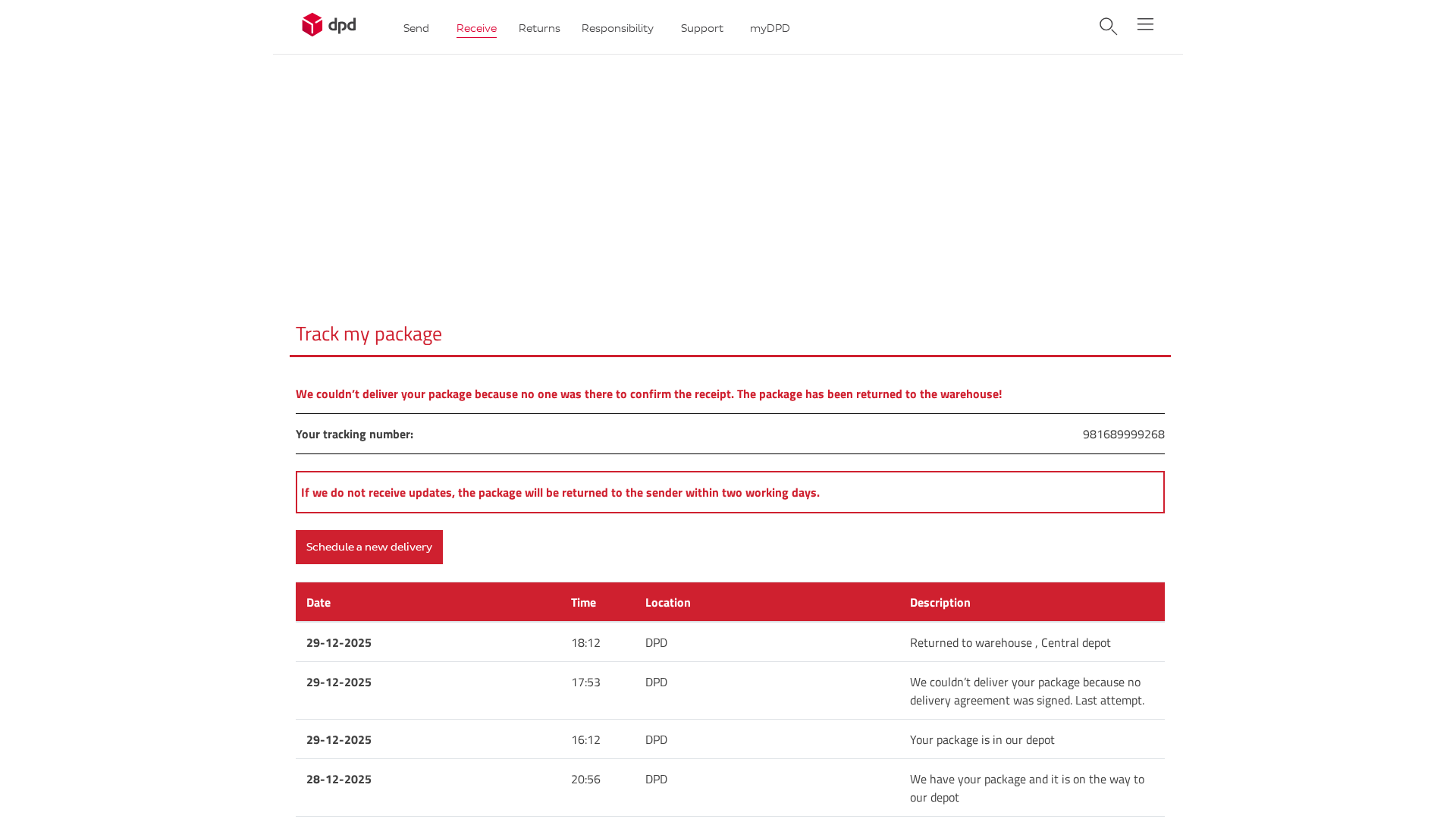
Detection Info
https://72-146-195-11.cprapid.com/ch/update.php?38acq5nykn6yp82r9s2x
Detected Brand
DPD
Country
International
Confidence
100%
HTTP Status
200
Report ID
928afab8-fe9…
Analyzed
2025-12-30 04:31
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T1A2B2027094B5B63F009F7391A7386709A3D39783CB520BE567F8936D4B8AE84DC23169 |
|
CONTENT
ssdeep
|
192:bixLoxwz77qKHv/ySchJrVUmZGko5XTCReWyRMOsUFf9kIT/JO:mx8xw7pvKpJrVUIGkc+TxFUH/JO |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
bcc3c33c83693cc3 |
|
VISUAL
aHash
|
ffffffc3df8181ff |
|
VISUAL
dHash
|
39000027292b1342 |
|
VISUAL
wHash
|
8fffff8181818189 |
|
VISUAL
colorHash
|
07000000007 |
|
VISUAL
cropResistant
|
39000027292b1342,0000db6464649b24 |
Code Analysis
Risk Score
65/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 Banking
🔬 Threat Analysis Report
• Threat: Package tracking phishing targeting DPD customers.
• Target: DPD customers globally.
• Method: Falsely claims delivery issues and requests updates to redirect packages.
• Exfil: Potentially collects tracking number and related details.
• Indicators: IP address as domain, non-matching URL.
• Risk: HIGH - Attempting to harvest package information for malicious purposes.
🔐 Credential Harvesting Forms
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
DPD
https://212-227-48-175.cprapid.com/de/update.php
Jan 07, 2026
No screenshot
DPD
https://138-68-183-9.cprapid.com/de/update.php
Dec 31, 2025
DPD
https://138-68-183-9.cprapid.com/de/update.php
Dec 31, 2025
DPD
https://217-160-164-192.cprapid.com/de/update.php?g1hdiel1pc...
Dec 30, 2025
DPD
https://69-164-193-72.cprapid.com/de/update.php
Dec 30, 2025