
Phishing Analysis
Detailed analysis of captured phishing page
95
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: Trezor
- • Threat: Credential harvesting phishing kit
- • Target: Trezor users internationally
- • Method: Fake CAPTCHA page stealing user input
- • Exfil: Data likely sent to attacker's server
- • Indicators: Domain mimics Trezor, obfuscated JavaScript, form submission detected
- • Risk: HIGH - Potential for credential theft
⚠ Risk Factors
- JavaScript obfuscation detected (5 patterns)
- OTP/2FA stealing indicators detected
- Banking fraud indicators detected
Visual Capture
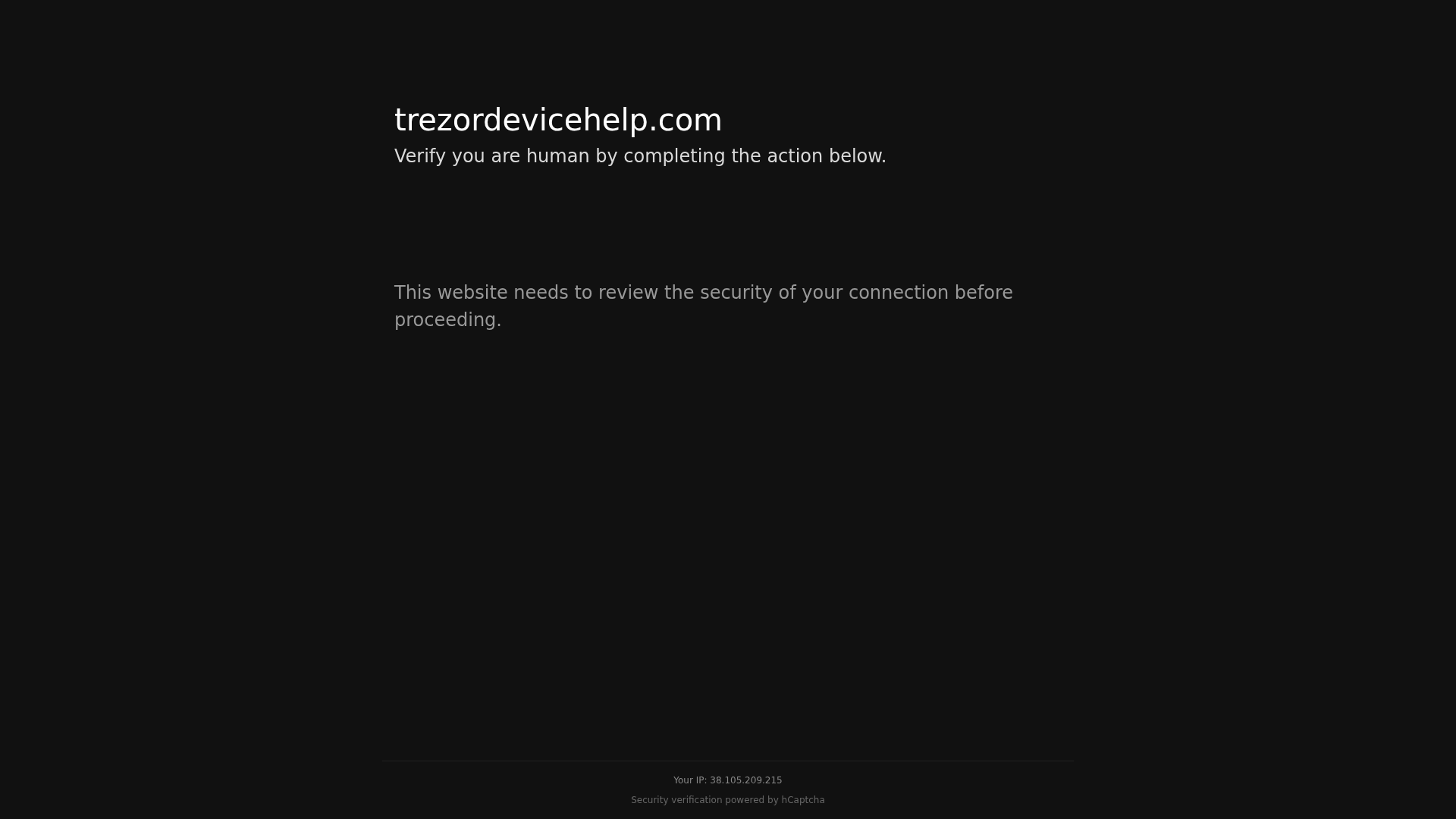
Detection Info
https://trezordevicehelp.com/captcha/
Detected Brand
Trezor
Country
International
Confidence
100%
HTTP Status
200
Report ID
96faa9ca-203…
Analyzed
2026-01-11 07:46
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T10D411E30614918380887C3CC72B5D38FA7B39344EB47059862E5E6906BDFFA8CD566C5 |
|
CONTENT
ssdeep
|
24:4OWCqy7sv5zKz3qwuhc0MNJhjENJhadFt+GnQ8+ac9xcjT3Cwsy3vKfbAd0f1DZ3:rP85zKz3oLirjaryt+GQ2vC0Ksy1DN15 |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
cfcfcc3431333131 |
|
VISUAL
aHash
|
30383c3800000018 |
|
VISUAL
dHash
|
6062584014000010 |
|
VISUAL
wHash
|
3c3c3c3c00003c3c |
|
VISUAL
colorHash
|
38000000000 |
|
VISUAL
cropResistant
|
6062584014000010 |
Code Analysis
Risk Score
95/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 OTP Stealer
🎣 Banking
🎣 Personal Info
🔬 Threat Analysis Report
• Threat: Credential harvesting phishing kit
• Target: Trezor users internationally
• Method: Fake CAPTCHA page stealing user input
• Exfil: Data likely sent to attacker's server
• Indicators: Domain mimics Trezor, obfuscated JavaScript, form submission detected
• Risk: HIGH - Potential for credential theft
🔒 Obfuscation Detected
- atob
- fromCharCode
- unescape
- document.write
- base64_strings
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
No screenshot
Trezor
https://trezorwalletsupport.com/captcha
Jan 01, 2026
No screenshot
Trezor
https://trezorwalletsupport.com
Jan 01, 2026
No screenshot
Ledger
http://scanledgerwallet.com/captcha
Jan 01, 2026
No screenshot
Trezor
http://trezorwalletsupport.com
Dec 31, 2025
No screenshot
Trezor
https://trezorwalletsupport.com/captcha/
Dec 31, 2025
Scan History for trezordevicehelp.com
Found 1 other scan for this domain