
Phishing Analysis
Detailed analysis of captured phishing page
66
Risk Score
Medium Risk
Threat Level: ALTO
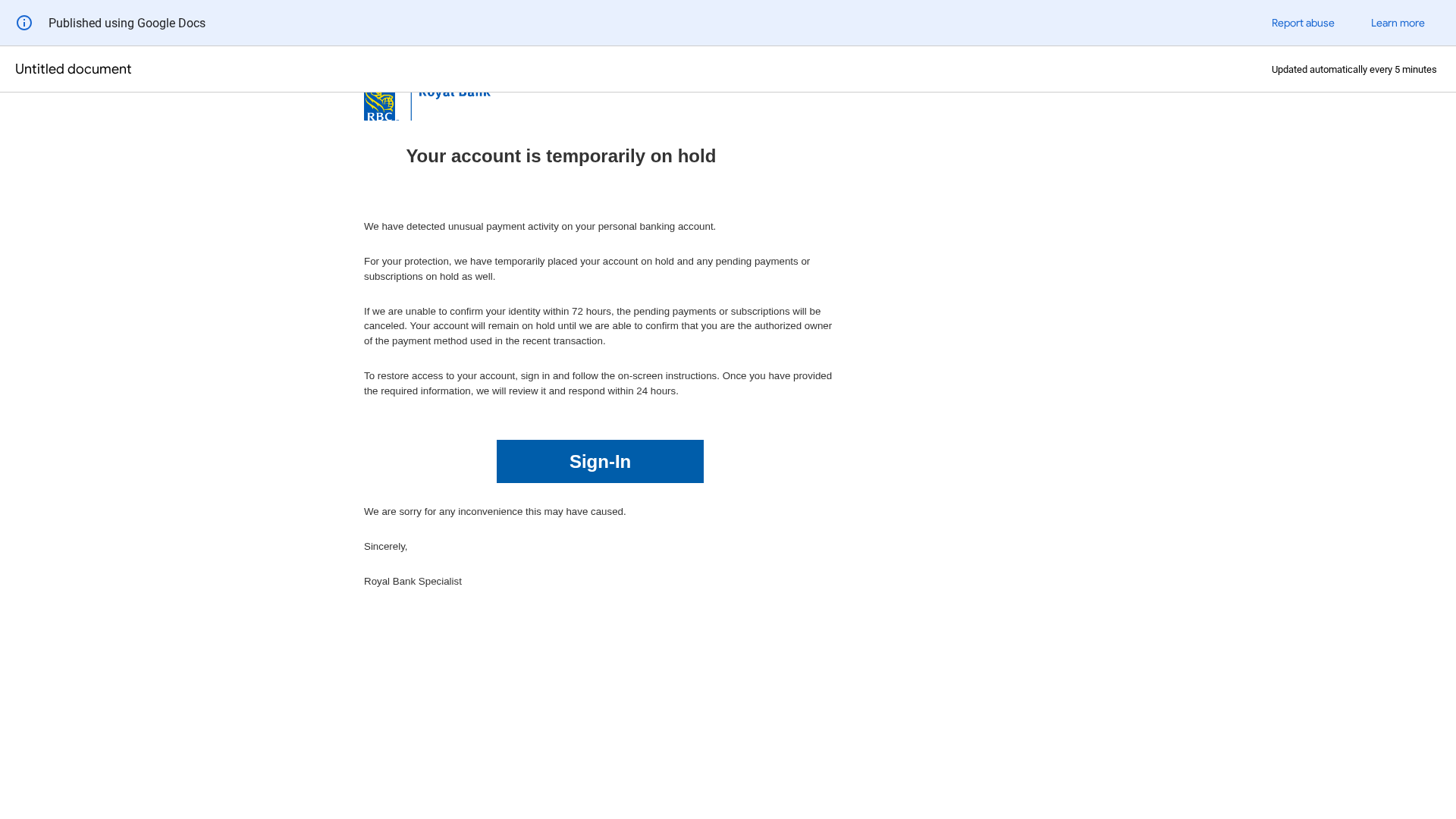
• Impersonating: Royal Bank
- • Threat: Phishing attempt impersonating Royal Bank
- • Target: Royal Bank customers
- • Method: Fake account hold notification to steal login credentials
- • Exfil: Potential data exfiltration via obfuscated JavaScript
- • Indicators: Free hosting on Google Docs, domain mismatch, urgent language
- • Risk: HIGH - Immediate risk of credential theft
⚠ Risk Factors
- Brand impersonation of Royal Bank on non-official domain
- Banking fraud indicators detected
Visual Capture
Detection Info
https://docs.google.com/document/d/e/2PACX-1vTh3iya0ov7P49Rk9eJOZGqnUEUk8FNa2mkY389heRtlwx4MNOyHl1MlhnWBZ8sxnsqTk8i5uySMQ68/pub?embedded=true
Detected Brand
Royal Bank
Country
UK
Confidence
95%
HTTP Status
200
Report ID
99f98326-d79…
Analyzed
2026-01-09 23:04
Final URL (after redirects)
https://docs.google.com/document/d/e/2PACX-1vTh3iya0ov7P49Rk9eJOZGqnUEUk8FNa2mkY389heRtlwx4MNOyHl1MlhnWBZ8sxnsqTk8i5uySMQ68/pub
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T1C87174A7B06424375A2749C879F6076931D2A03EE3831C78E7FC02AC43DDF9AB816027 |
|
CONTENT
ssdeep
|
96:VgRYCfDEmesqPCwk2zzLuQq/pT8eQ5awq+QPiI5TPNUV42k+:6RYADdqVkk3OvQPqY3j |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
b11cce3133ce4e33 |
|
VISUAL
aHash
|
00cfcfc7cfdfffff |
|
VISUAL
dHash
|
a0181c1c1a380000 |
|
VISUAL
wHash
|
008f87870000f0f0 |
|
VISUAL
colorHash
|
070000001c0 |
|
VISUAL
cropResistant
|
a0181c1c1a380000 |
Code Analysis
Risk Score
66/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Banking
🔬 Threat Analysis Report
• Threat: Phishing attempt impersonating Royal Bank
• Target: Royal Bank customers
• Method: Fake account hold notification to steal login credentials
• Exfil: Potential data exfiltration via obfuscated JavaScript
• Indicators: Free hosting on Google Docs, domain mismatch, urgent language
• Risk: HIGH - Immediate risk of credential theft
🔒 Obfuscation Detected
- fromCharCode
- unescape
Scan History for docs.google.com
Found 10 other scans for this domain
-
https://docs.google.com/presentation/d/e/2PACX-1vS...
https://docs.google.com/presentation/d/e/2PACX-1vT...
https://docs.google.com/presentation/d/e/2PACX-1vS...
https://docs.google.com/forms/d/1ZrJdSKe4SJ2QUAPcf...
https://docs.google.com/forms/d/e/1FAIpQLSdMQ4frGs...
https://docs.google.com/presentation/d/e/2PACX-1vQ...
https://docs.google.com/forms/d/1qUV0ZKLYHGW_4y4Pf...
https://docs.google.com/forms/d/e/1FAIpQLSdrYyw_8J...
https://docs.google.com/forms/d/e/1FAIpQLSdbKfmfqZ...
https://docs.google.com/presentation/d/e/2PACX-1vS...