
Phishing Analysis
Detailed analysis of captured phishing page
95
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: DPD
- • Threat: Package delivery scam phishing
- • Target: DPD customers
- • Method: Fake tracking page prompts for information or malware install
- • Exfil: Likely to a server under the attacker's control
- • Indicators: IP address domain, brand impersonation, prompts for information
- • Risk: HIGH - Data theft or malware infection
⚠ Risk Factors
- Brand impersonation of DPD on non-official domain
- Contains 4 credential harvesting form(s)
- JavaScript obfuscation detected (5 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
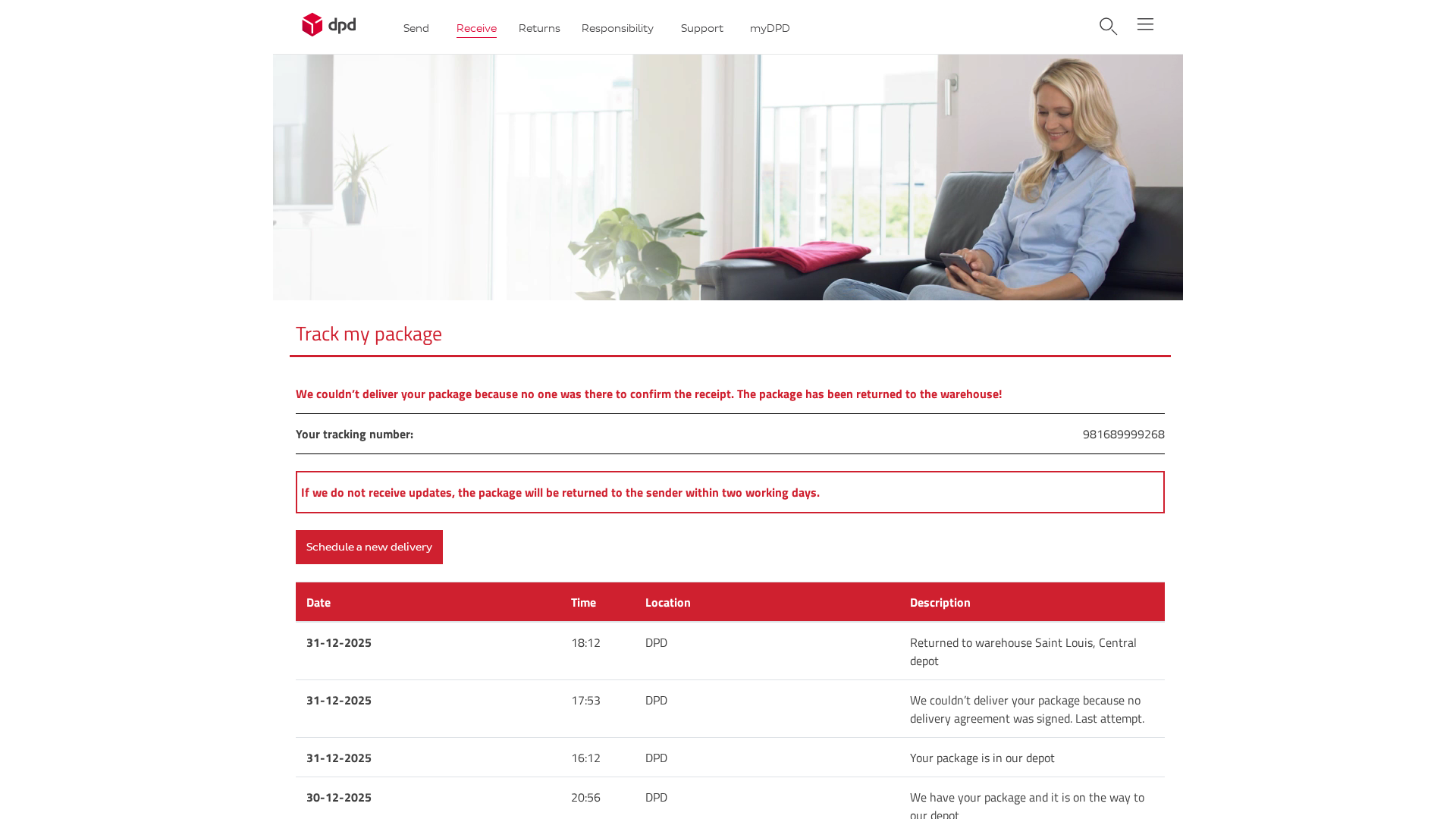
Detection Info
https://194-164-61-191.cprapid.com/de
Detected Brand
DPD
Country
International
Confidence
100%
HTTP Status
200
Report ID
9cce66b2-bf9…
Analyzed
2026-01-02 07:10
Final URL (after redirects)
https://194-164-61-191.cprapid.com/de/update.php?r7agnes3w9i0y8xm6b3p
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T164B2017094B5B63F009F7391A7386709A3D39783CB520BE567F8836D5B8AE84DC23169 |
|
CONTENT
ssdeep
|
192:8ixLoxwz77qKHv/ySchJrVUmZGkouXTCReWyRMOsUFf9kIT/JO:xx8xw7pvKpJrVUIGkl+TxFUH/JO |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
e96b899c962666c3 |
|
VISUAL
aHash
|
f9e9e1f7ff81c3ff |
|
VISUAL
dHash
|
2b030327382b0342 |
|
VISUAL
wHash
|
a9a1e1c7878183fb |
|
VISUAL
colorHash
|
07000000006 |
|
VISUAL
cropResistant
|
2b030327382b0342,696969c9692b3734,337367e5cdcd8d1d,0000db6464649b24 |
Code Analysis
Risk Score
95/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Banking
🎣 Personal Info
🔬 Threat Analysis Report
• Threat: Package delivery scam phishing
• Target: DPD customers
• Method: Fake tracking page prompts for information or malware install
• Exfil: Likely to a server under the attacker's control
• Indicators: IP address domain, brand impersonation, prompts for information
• Risk: HIGH - Data theft or malware infection
🔐 Credential Harvesting Forms
🔒 Obfuscation Detected
- atob
- eval
- fromCharCode
- unescape
- base64_strings
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
DPD
https://74-242-168-24.cprapid.com/de/update.php
Jan 10, 2026
DPD
https://74-242-168-24.cprapid.com/de/update.php
Jan 09, 2026
DPD
https://138-68-183-9.cprapid.com/de/update.php
Jan 07, 2026
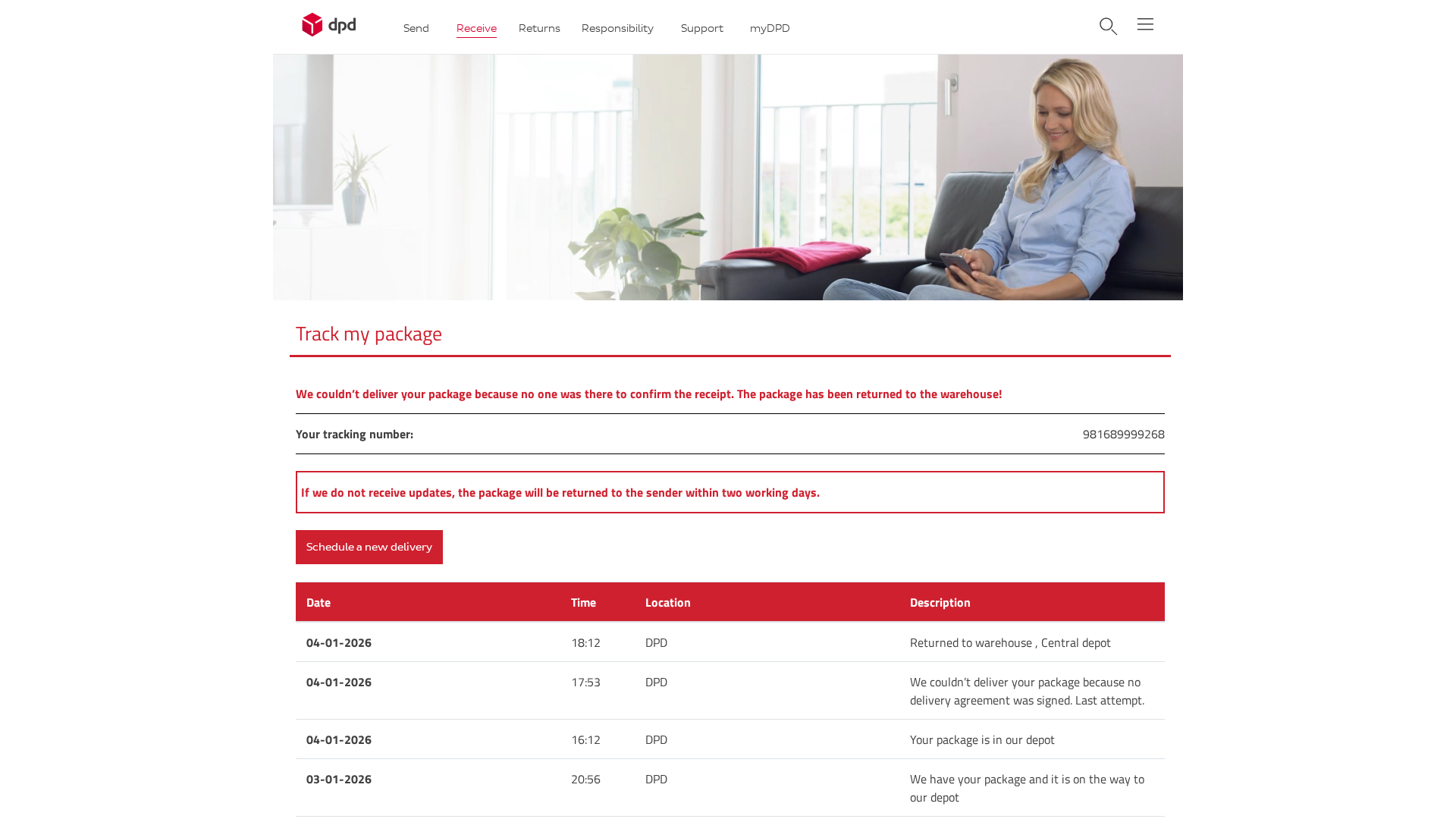
DPD
https://217-160-164-192.cprapid.com/de/update.php?g1hdiel1pc...
Jan 06, 2026
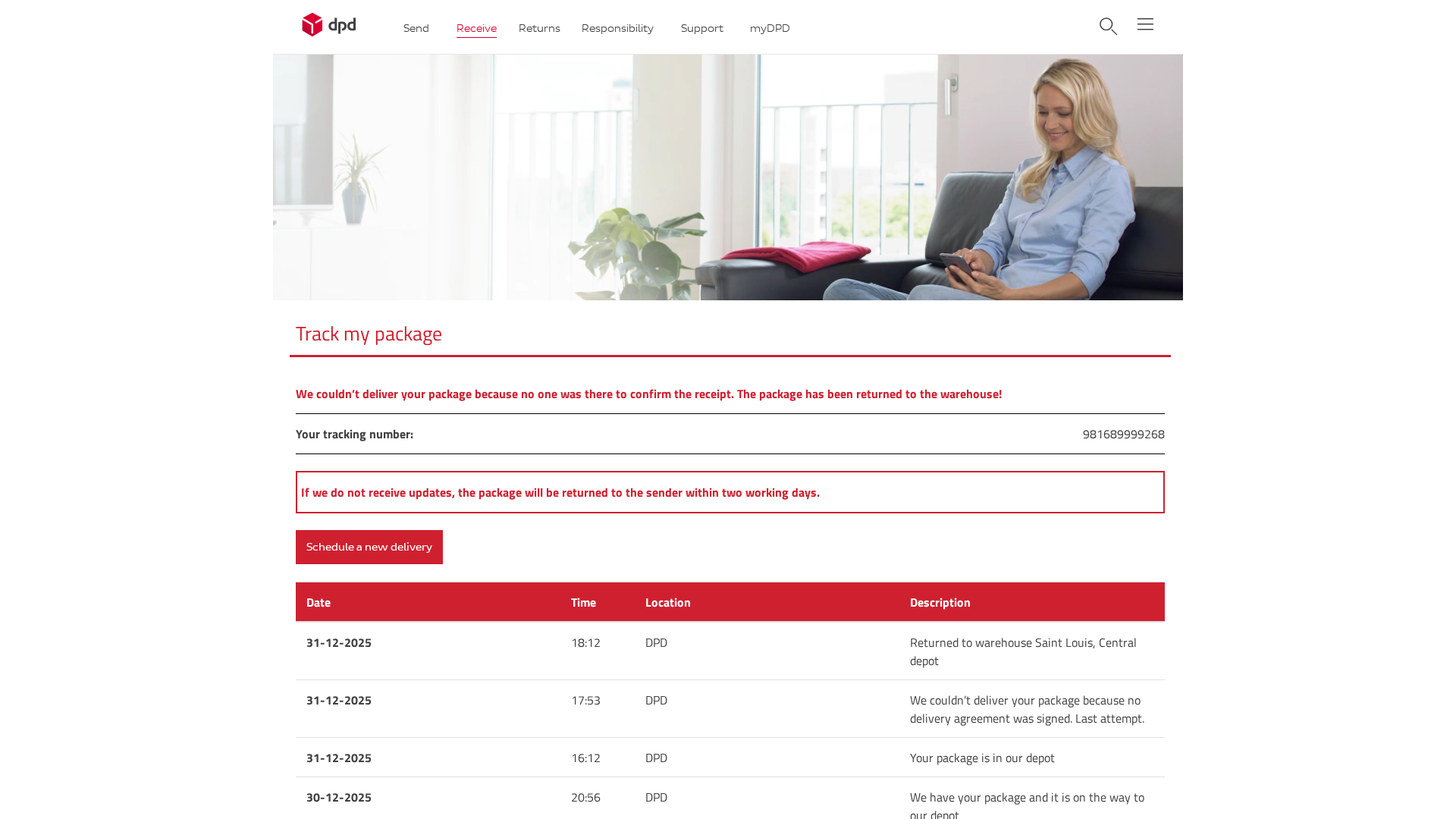
DPD
https://194-164-61-191.cprapid.com/de
Jan 02, 2026
Scan History for 194-164-61-191.cprapid.com
Found 6 other scans for this domain