
Phishing Analysis
Detailed analysis of captured phishing page
100
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: Trust Wallet
- • Threat: Credential harvesting phishing kit
- • Target: Trust Wallet users internationally
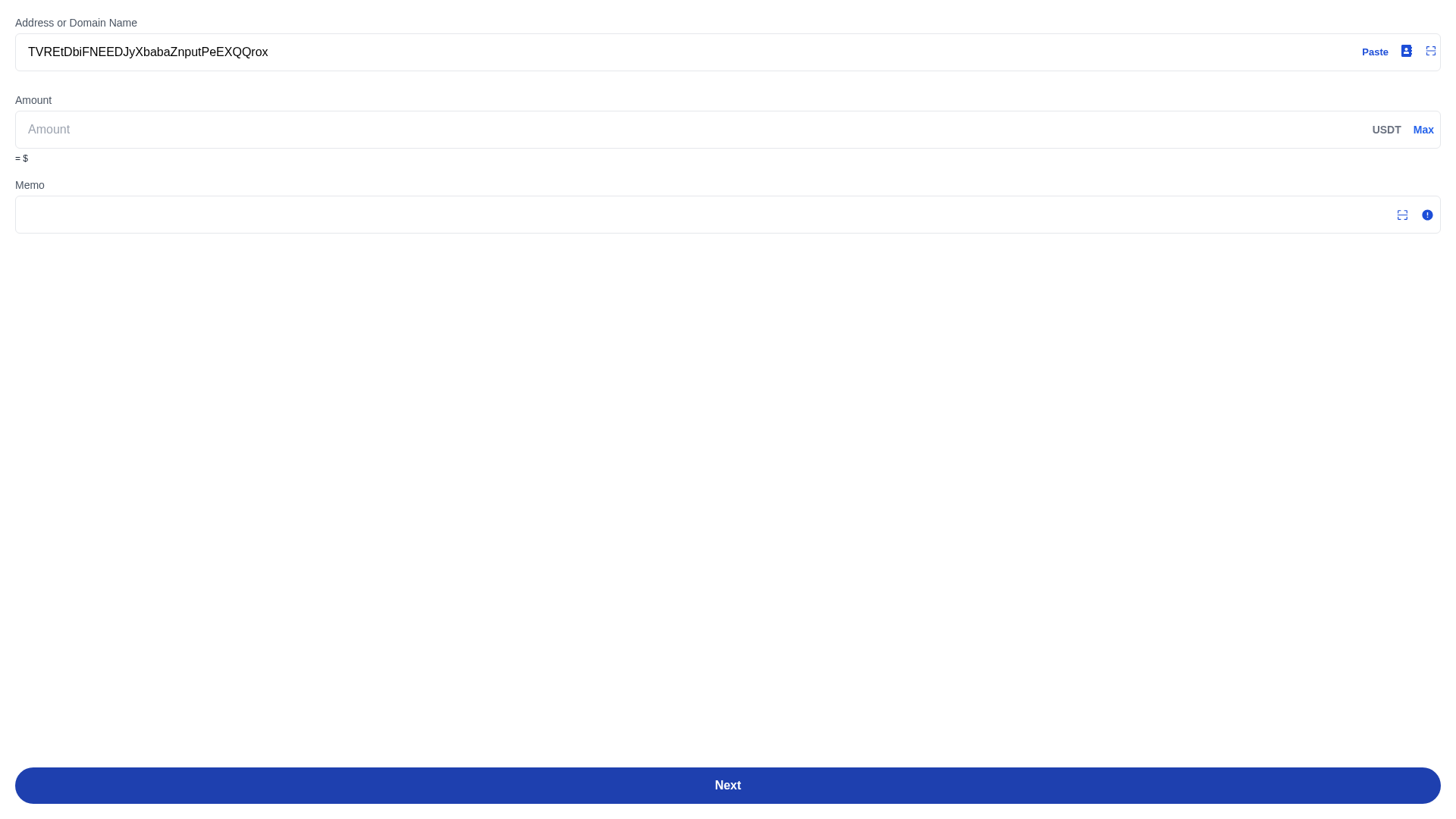
- • Method: Fake form requesting address/domain, amount, and memo
- • Exfil: Data sent to Telegram bot (token: 8096816664:AAG3BsPLHaHwpn8qft-fRVy2JeGdlpAvnog)
- • Indicators: Domain mismatch, obfuscated JavaScript, form submission
- • Risk: HIGH - Immediate credential theft
⚠ Risk Factors
- Contains 1 Telegram bot token(s) for credential exfiltration
- Contains 4 form(s) with JavaScript submission
- JavaScript obfuscation detected (6 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
- WebSocket connection for real-time C2 communication
Visual Capture
Detection Info
https://trustwalletverified.com
Detected Brand
Trust Wallet
Country
International
Confidence
100%
HTTP Status
200
Report ID
9ee4ead5-1bb…
Analyzed
2026-01-11 08:35
Final URL (after redirects)
https://trustwalletverified.com/
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T104F5B54066C06888234B8FFB772BB4E5F41E09AF795C488FE114BC2465A6627FEF5931 |
|
CONTENT
ssdeep
|
49152:7oW+0zU6TITSMbXUcBZBuJyPesVWvvg5MagjgM+J0bDyfXCixyR+qTXtityZBva2:NbDUCR |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
8f850f852f852f95 |
|
VISUAL
aHash
|
7fffffffffffff00 |
|
VISUAL
dHash
|
d0c0000000410051 |
|
VISUAL
wHash
|
000000ffffffff00 |
|
VISUAL
colorHash
|
070000001c0 |
|
VISUAL
cropResistant
|
d0c0000000410051,0100101010000001 |
Code Analysis
Risk Score
100/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Banking
🎣 Personal Info
Telegram Exfiltration
WebSocket C2
🔬 Threat Analysis Report
• Threat: Credential harvesting phishing kit
• Target: Trust Wallet users internationally
• Method: Fake form requesting address/domain, amount, and memo
• Exfil: Data sent to Telegram bot (token: 8096816664:AAG3BsPLHaHwpn8qft-fRVy2JeGdlpAvnog)
• Indicators: Domain mismatch, obfuscated JavaScript, form submission
• Risk: HIGH - Immediate credential theft
🔒 Obfuscation Detected
- atob
- unescape
- hex_escape
- unicode_escape
- js_packer
- base64_strings
🔑 Telegram Bot Tokens (1)
- 8096816664:AAG3...dlpAvnog
💬 Telegram Chat IDs (1)
- 7492173080