
Phishing Analysis
Detailed analysis of captured phishing page
70
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: Microsoft
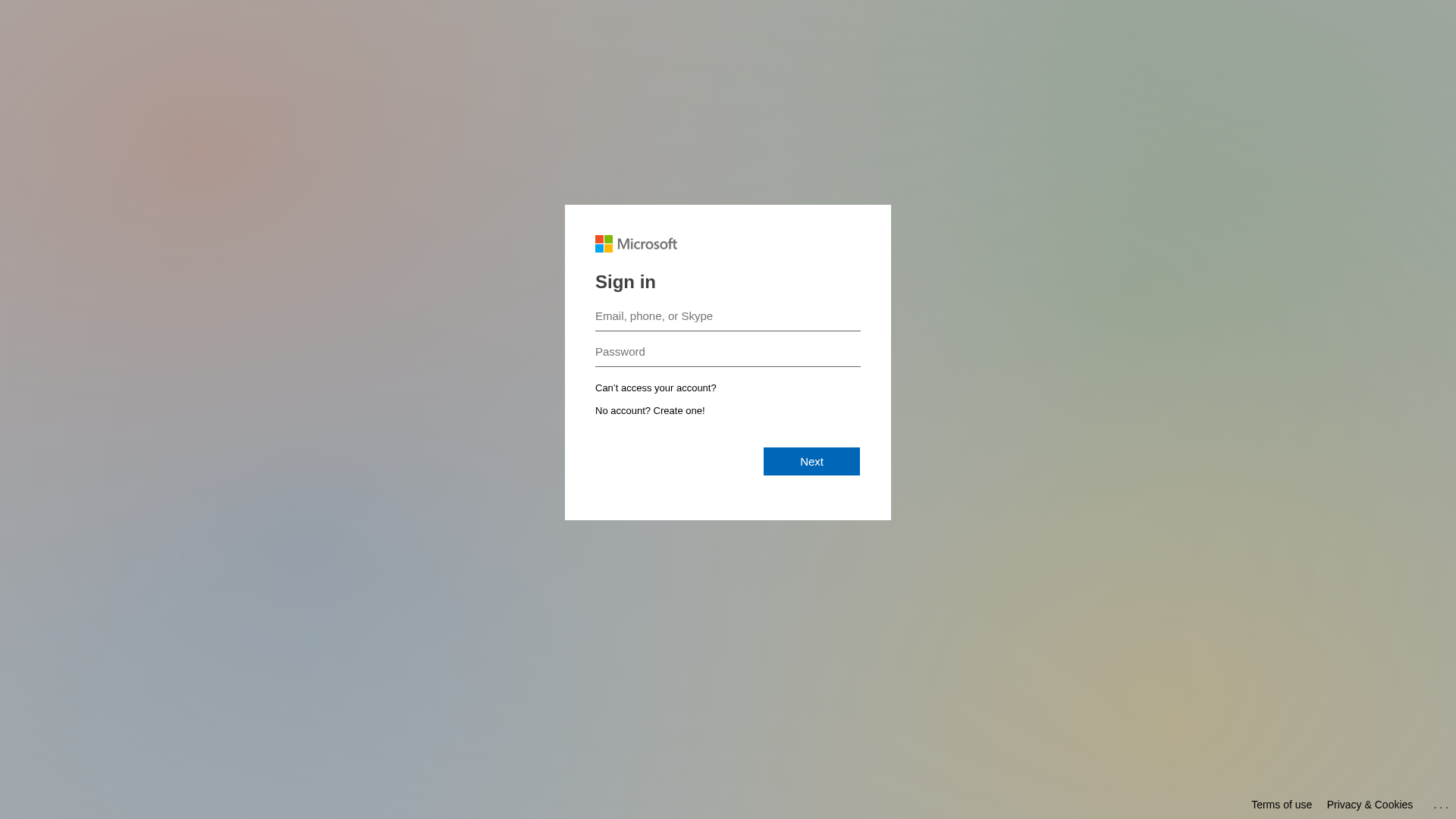
- A phishing attempt impersonating Microsoft has been detected. The Microsoft login form is displayed on a non-Microsoft domain (securityawareness.cc), indicating an attempt to steal credentials.
⚠ Risk Factors
- Brand impersonation of Microsoft on non-official domain
Visual Capture
No screenshot available
Detection Info
https://securityawareness.cc/landing/form/10d2324c-1548-44bc-afd1-5d7ab0fa06f4/
Detected Brand
Microsoft
Country
International
Confidence
100%
HTTP Status
200
Report ID
a01767b7-bdf…
Analyzed
2025-12-11 12:09
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T1BB51981DD2110342A257AE64FA63FB8625200AC2C602853C79BD8676F7CE67553723CD |
|
CONTENT
ssdeep
|
48:nekVJLwlls5hwhFO7c2ZgV0jxJF0jIPcU+5DmG5hkjRtlAjD:nJJLBhn7xg6jxJqjJ9tmKz |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
9cc97326cc99d98c |
|
VISUAL
aHash
|
0000181818180000 |
|
VISUAL
dHash
|
6171333232327c78 |
|
VISUAL
wHash
|
1818181c1f1f1fff |
|
VISUAL
colorHash
|
070000001c0 |
|
VISUAL
cropResistant
|
6171333232327c78 |
Code Analysis
Risk Score
70/100
Threat Level
ALTO
🔬 Threat Analysis Report
A phishing attempt impersonating Microsoft has been detected. The Microsoft login form is displayed on a non-Microsoft domain (securityawareness.cc), indicating an attempt to steal credentials.
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
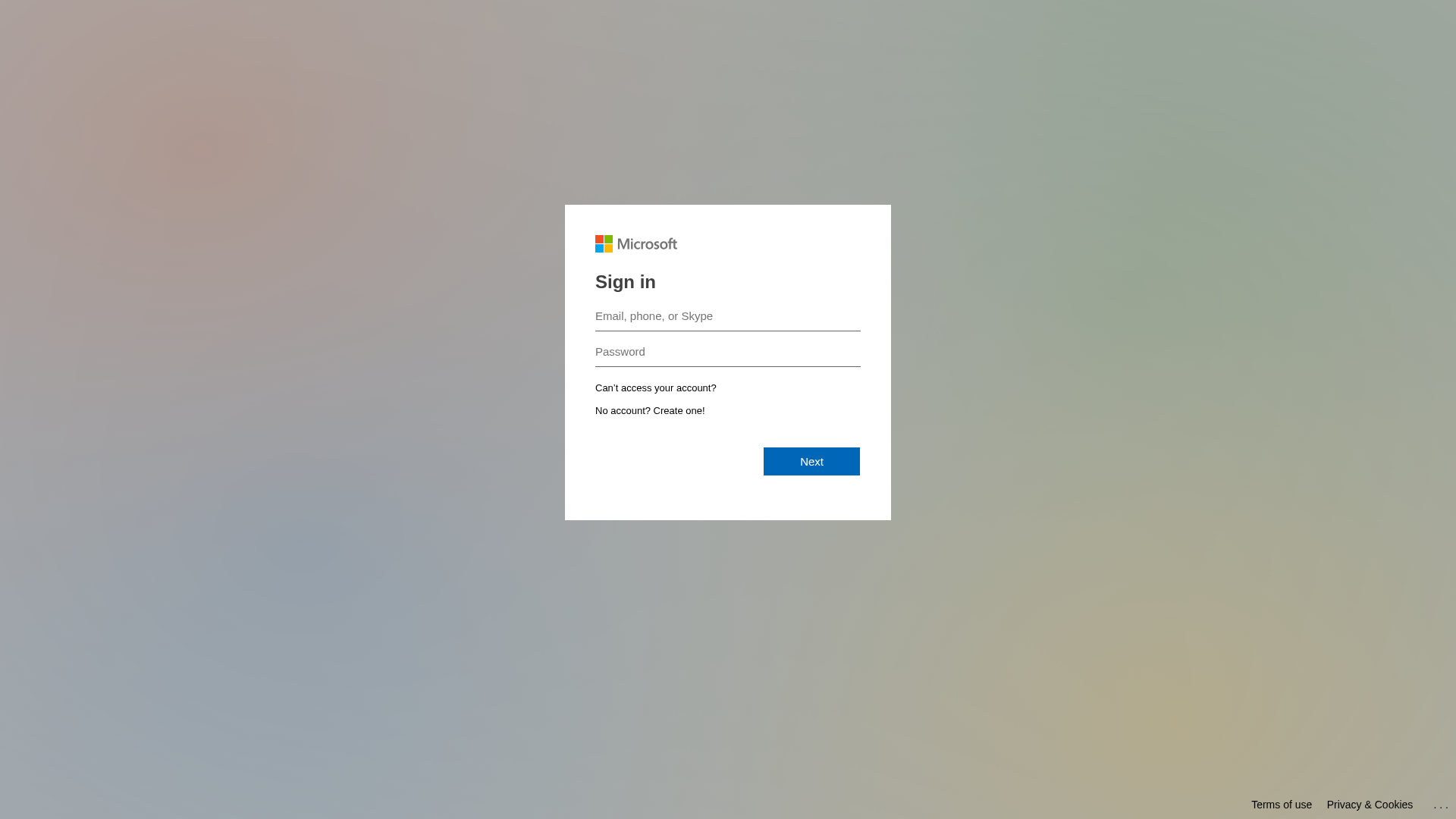
Microsoft
https://securityawareness.cc/landing/form/90273d17-767e-41c3...
Jan 10, 2026
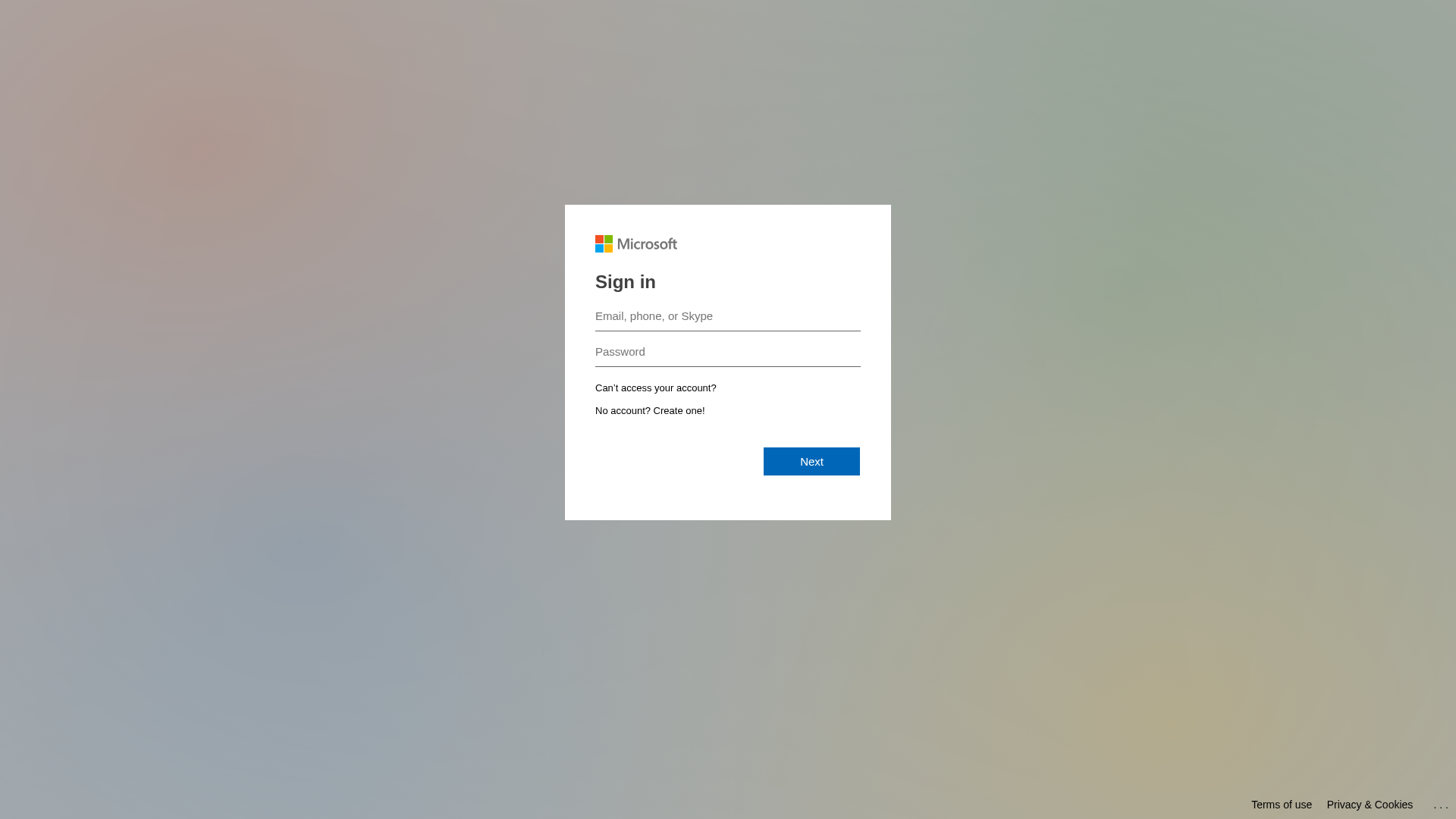
Microsoft
https://securityawareness.cc/landing/form/90273d17-767e-41c3...
Jan 10, 2026
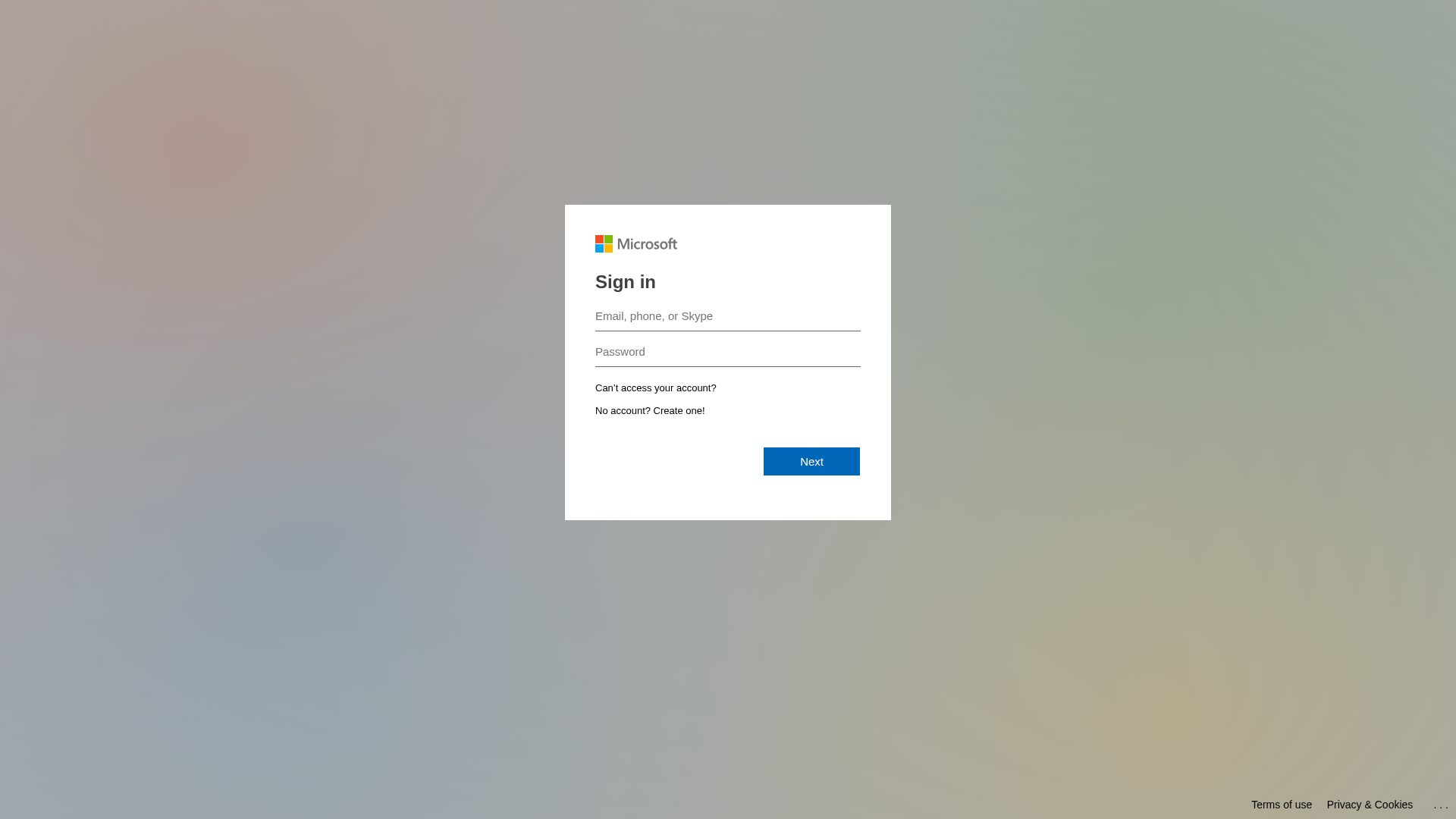
Microsoft
https://securityawareness.cc/landing/form/857b14f2-c167-4dbb...
Jan 01, 2026
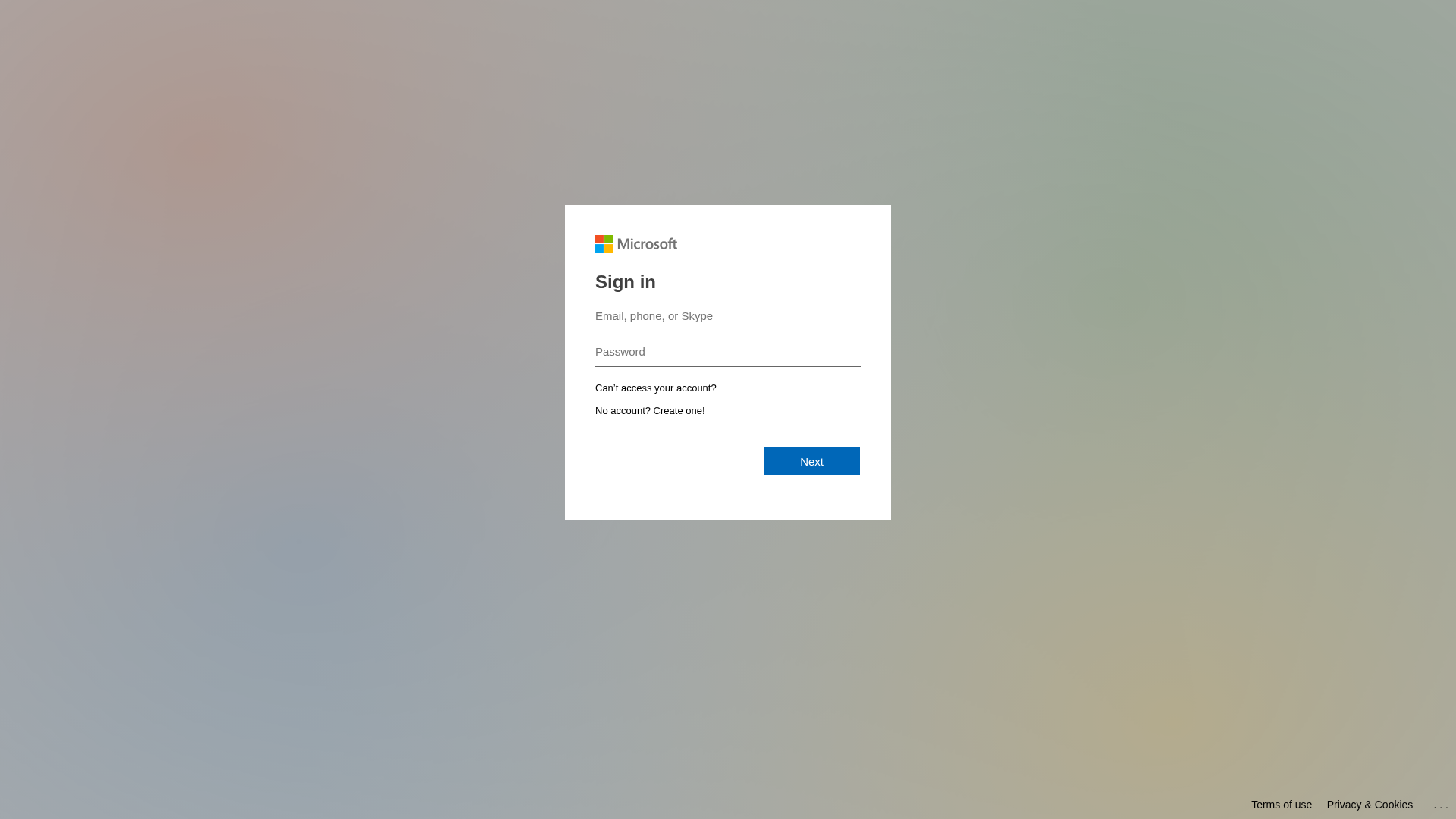
Microsoft
http://mgamt.com/landing/form/3261b7e4-cda3-4263-b1f5-8e5d4d...
Dec 28, 2025
Microsoft
https://mgamt.com/landing/form/2304cdba-1a5e-4680-902b-892d5...
Dec 25, 2025
Scan History for securityawareness.cc
Found 3 other scans for this domain