
Phishing Analysis
Detailed analysis of captured phishing page
100
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: Timeweb
⚠ Risk Factors
- Brand impersonation of Timeweb on non-official domain
- Contains 1 credential harvesting form(s)
- JavaScript obfuscation detected (8 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
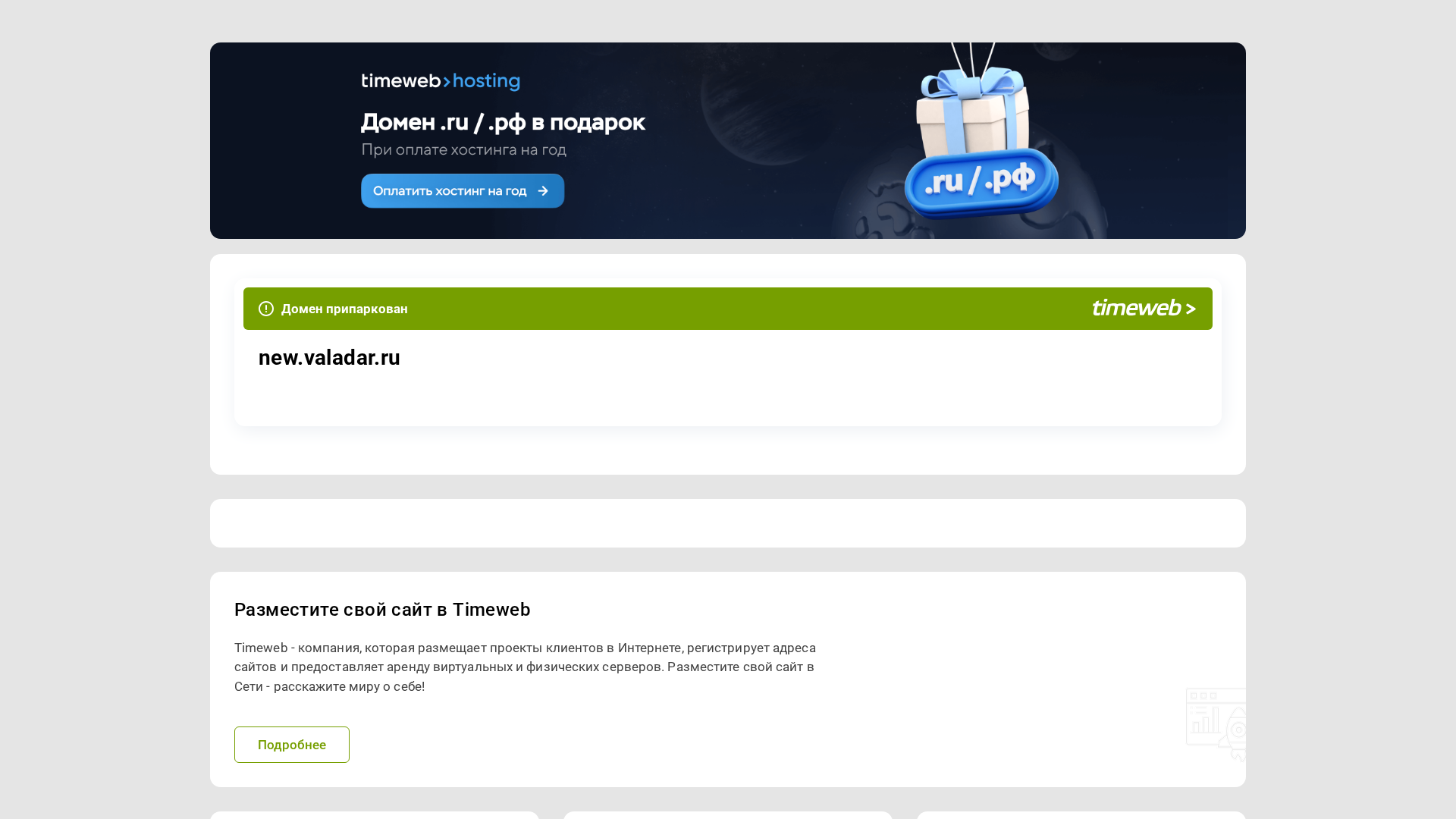
Detection Info
http://new.valadar.ru/shiftlessly/derivator
Detected Brand
Timeweb
Country
International
Confidence
100%
HTTP Status
200
Report ID
a0fcafd5-ee0…
Analyzed
2026-01-08 05:59
Final URL (after redirects)
https://vh422.timeweb.ru/parking/?ref=new.valadar.ru
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T1BC23E8F34194E0E14A8FC3F49D326ADBD67624FDDF825284AADC89107593AF8CD81AD4 |
|
CONTENT
ssdeep
|
384:kmG6SGPbv1Awa5vFLZw7F7XG7HoPz24jE4w1Hm/rtPtctZu3RfOFWxpEu+Rzt2pc:zNHGKBXWIPzGHm/ou3RfOF4EnRzUO256 |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
ba3a3ad0c5c5c5c5 |
|
VISUAL
aHash
|
818181ffffffffff |
|
VISUAL
dHash
|
2b292bb2c8f8b8c0 |
|
VISUAL
wHash
|
000000027f7fffff |
|
VISUAL
colorHash
|
0e002006040 |
|
VISUAL
cropResistant
|
2b292bb2c8f8b8c0,ec62fd1d9d9d9980,7494e4c474cccc6a |
Code Analysis
Risk Score
100/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Card Stealer
🎣 Banking
🎣 Personal Info
🔐 Credential Harvesting Forms
🔒 Obfuscation Detected
- atob
- eval
- fromCharCode
- unescape
- document.write
- hex_escape
- unicode_escape
- base64_strings
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
Timeweb
https://vh434.timeweb.ru/blocked/?ref=ce017851.tw1.ru
Jan 10, 2026
Timeweb
https://vh434.timeweb.ru/parking/?ref=cy792838.tw1.ru
Jan 10, 2026
Timeweb
https://vh434.timeweb.ru/parking/?ref=cb773971.tw1.ru
Jan 10, 2026
Timeweb
https://vh434.timeweb.ru/parking/?ref=co928090.tw1.ru
Jan 10, 2026
Timeweb
http://dekoform.ru/en/webmail-login/index.html
Jan 09, 2026