Phishing Analysis
Detailed analysis of captured phishing page
85
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: Gobierno de México
- • Threat: Credential harvesting phishing kit
- • Target: Mexican passport applicants
- • Method: Fake passport application form stealing personal data
- • Exfil: Data likely sent to unknown server
- • Indicators: Non-official domain, recent domain registration, obfuscated JavaScript
- • Risk: HIGH - Immediate personal data theft
⚠ Risk Factors
- Brand impersonation of Gobierno de México on non-official domain
- Contains 3 form(s) with JavaScript submission
- JavaScript obfuscation detected (5 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
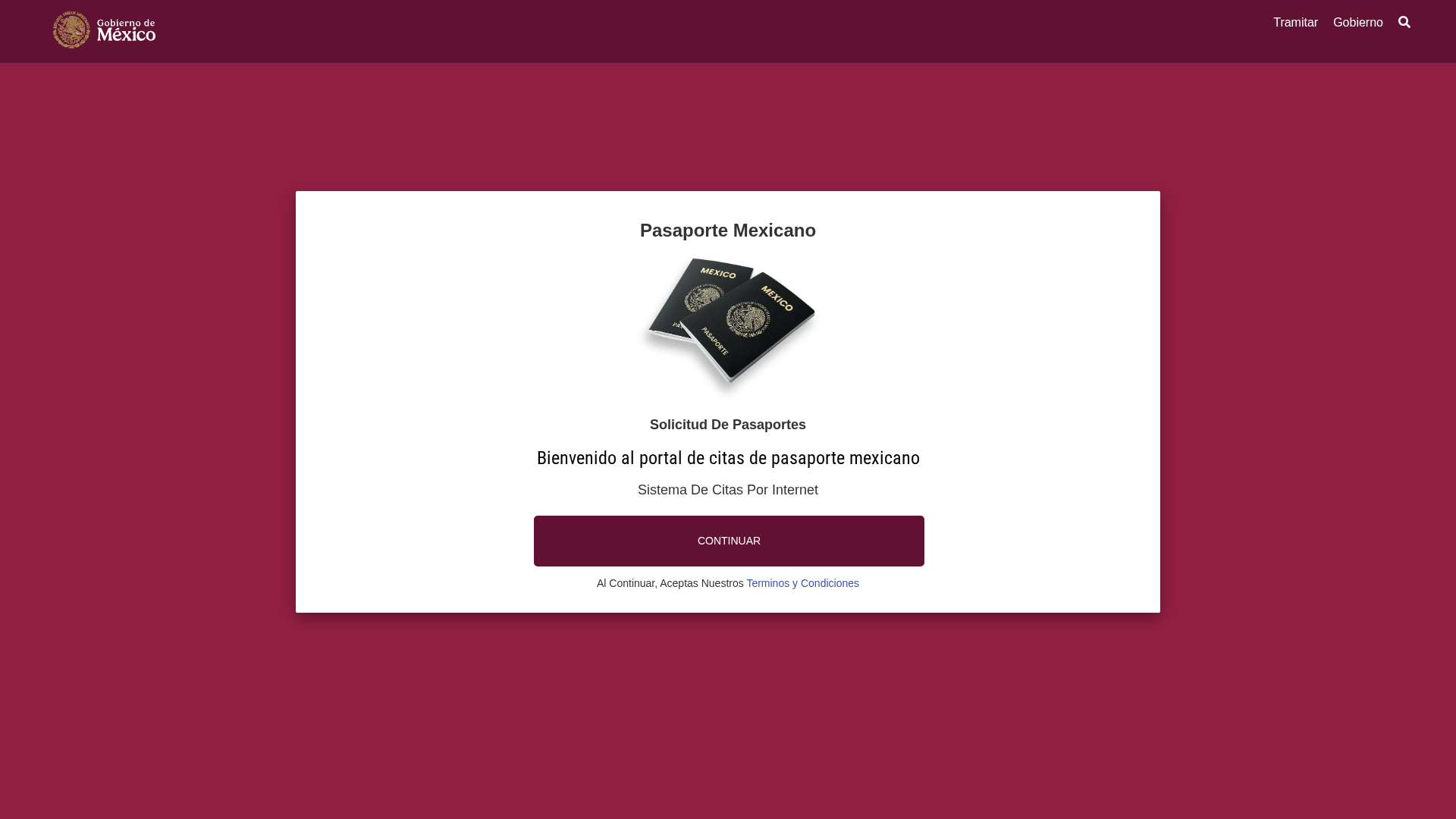
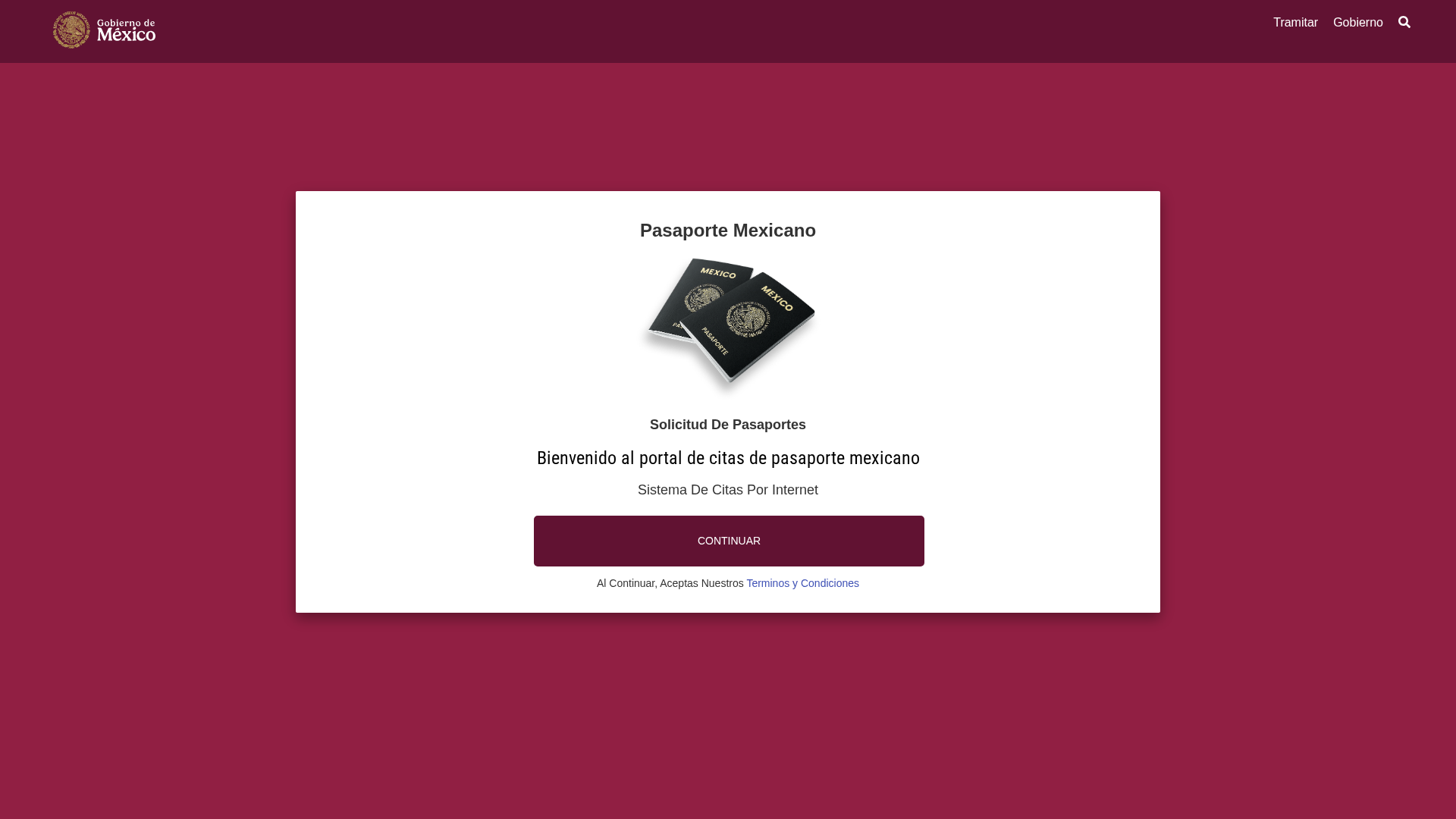
Visual Capture
Detection Info
https://sre-segob.mx/citas-gobmx/
Detected Brand
Gobierno de México
Country
Mexico
Confidence
100%
HTTP Status
200
Report ID
a3c9e1a5-856…
Analyzed
2026-01-11 06:39
Final URL (after redirects)
https://sre-segob.mx/citas-gobmx/#/SRE
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T1D4B11F35460424BA0BA3BDE8DA937E1561CFC01AD6DF0718A5E84BAD1BC2FF4D482F61 |
|
CONTENT
ssdeep
|
96:dH3OuQRq8UpkMIf5xvL6fSWrI9c5chHPxKOC87D:xmqnpkMIf5ASWAFCkD |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
c6ce3971486ec699 |
|
VISUAL
aHash
|
00007e7e7e7e0000 |
|
VISUAL
dHash
|
2bf0ccecccccf007 |
|
VISUAL
wHash
|
007e7e7e7e7e0000 |
|
VISUAL
colorHash
|
02000000007 |
|
VISUAL
cropResistant
|
8c8c8c8c8e8e9696,2bf0ccecccccf007,2e274d189903060d,00100cb2b20c1000 |
Code Analysis
Risk Score
85/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Banking
🎣 Personal Info
🔬 Threat Analysis Report
• Threat: Credential harvesting phishing kit
• Target: Mexican passport applicants
• Method: Fake passport application form stealing personal data
• Exfil: Data likely sent to unknown server
• Indicators: Non-official domain, recent domain registration, obfuscated JavaScript
• Risk: HIGH - Immediate personal data theft
🔒 Obfuscation Detected
- unescape
- hex_escape
- unicode_escape
- js_packer
- base64_strings
Similar Websites
Pages with identical visual appearance (based on perceptual hash)