
Phishing Analysis
Detailed analysis of captured phishing page
73
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: Tonkeeper
- • Threat: Credential harvesting phishing kit
- • Target: Tonkeeper cryptocurrency wallet users
- • Method: Fake login form stealing user credentials
- • Exfil: Potential data exfiltration via obfuscated JavaScript
- • Indicators: Domain mismatch, forms present, obfuscation detected
- • Risk: HIGH - Immediate credential theft
⚠ Risk Factors
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
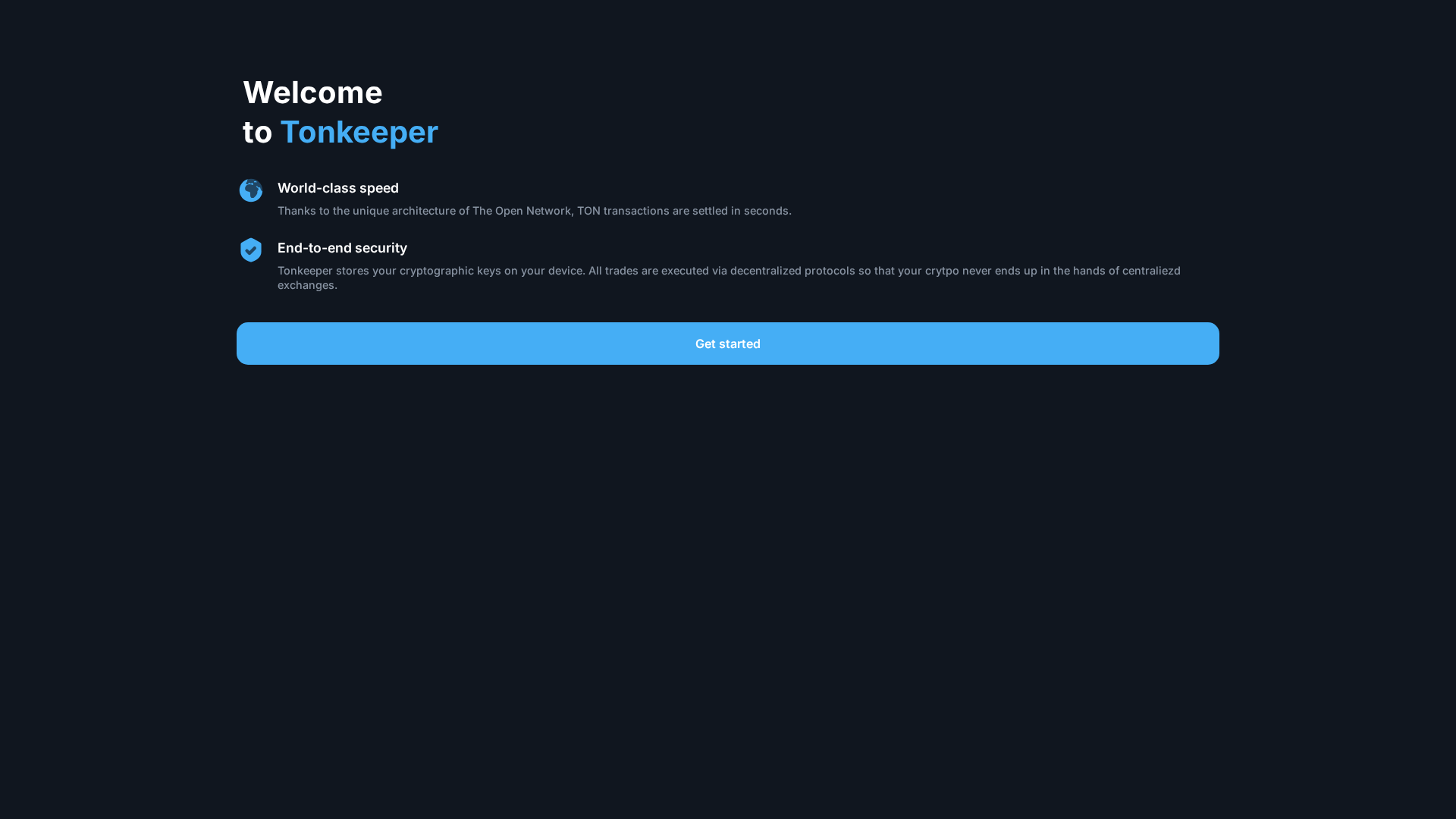
Detection Info
https://tonkeeperpro.com
Detected Brand
Tonkeeper
Country
International
Confidence
100%
HTTP Status
200
Report ID
aad7c1d2-382…
Analyzed
2026-01-11 08:31
Final URL (after redirects)
https://tonkeeperpro.com/
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T14DD1EFB1A208DCBB419386E583B5AB5F3A80D753CB27124953FC939D9BC3CC1CD698A4 |
|
CONTENT
ssdeep
|
48:nXSA83pS6USRjuwuSRpme6A9VAv4fQEIn29UIwcPH9hEoQ4NU1MTO6:nu3pPUcjZWe3jAvQQEx9UPg9LQt14 |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
c1c1693e96961e3e |
|
VISUAL
aHash
|
40607e7e00000000 |
|
VISUAL
dHash
|
9093d4d423800000 |
|
VISUAL
wHash
|
efefffff00000000 |
|
VISUAL
colorHash
|
380000001c0 |
|
VISUAL
cropResistant
|
0000003030100800,9093d4d423800000 |
Code Analysis
Risk Score
73/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Banking
🎣 Personal Info
🔬 Threat Analysis Report
• Threat: Credential harvesting phishing kit
• Target: Tonkeeper cryptocurrency wallet users
• Method: Fake login form stealing user credentials
• Exfil: Potential data exfiltration via obfuscated JavaScript
• Indicators: Domain mismatch, forms present, obfuscation detected
• Risk: HIGH - Immediate credential theft
🔒 Obfuscation Detected
- fromCharCode