
Phishing Analysis
Detailed analysis of captured phishing page
50
Risk Score
Medium Risk
Threat Level: ALTO
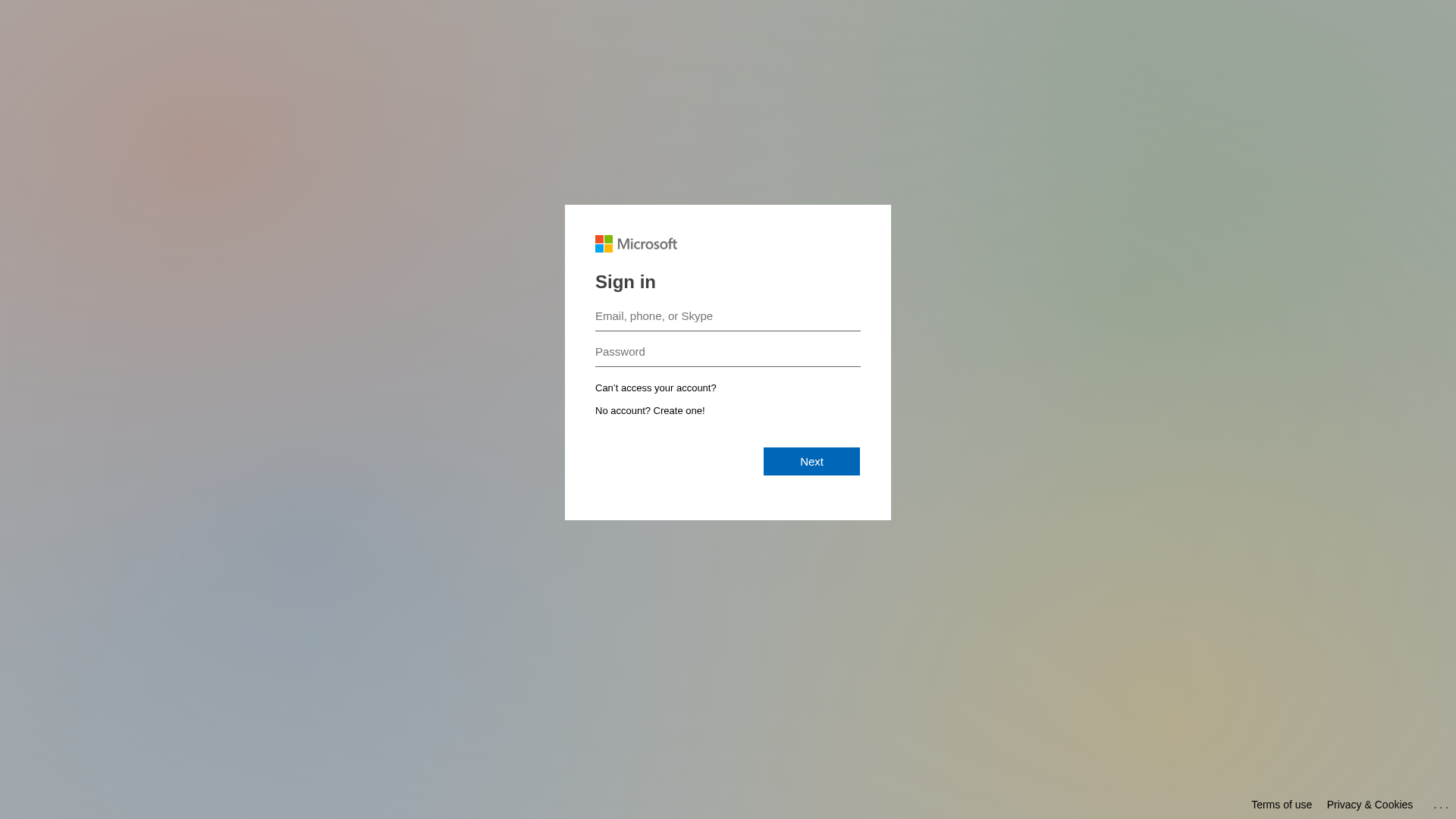
• Impersonating: Microsoft
- • Threat: Credential harvesting phishing kit
- • Target: Microsoft users globally
- • Method: Fake login form stealing email/phone/Skype and password
- • Exfil: Unknown, likely sent to attacker's server
- • Indicators: Domain mismatch, mimicked login form, no official URL
- • Risk: HIGH - Immediate credential theft
⚠ Risk Factors
- Brand impersonation of Microsoft on non-official domain
- Contains 1 credential harvesting form(s)
- Credential harvesting indicators detected
Visual Capture
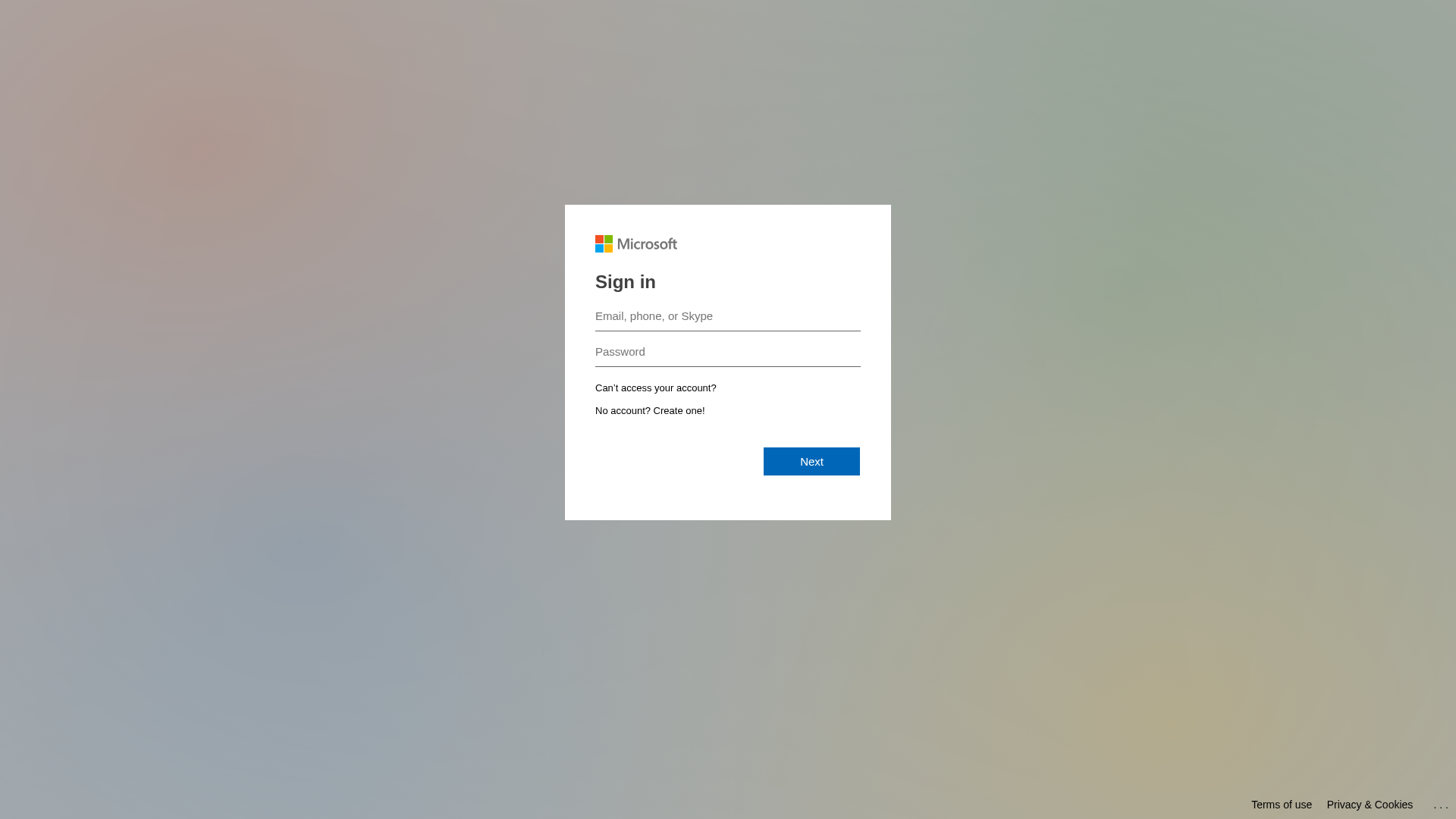
Detection Info
https://securityawareness.cc/landing/form/90273d17-767e-41c3-b80c-6ac125add670
Detected Brand
Microsoft
Country
International
Confidence
95%
HTTP Status
200
Report ID
ae38efa7-025…
Analyzed
2026-01-10 01:51
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T17641A81CD2010346E357EE90F962FBD666140BC0C7134A7C6AB9927AB1CE17553723CD |
|
CONTENT
ssdeep
|
48:n0i0Hls5hwhjO7c2ZgV0jxJF0jIPcU85D4c5hkj0:nfjhh7xg6jxJqjJTt4g5 |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
9cc97326cc99d98c |
|
VISUAL
aHash
|
0000181818180000 |
|
VISUAL
dHash
|
6171333232327c78 |
|
VISUAL
wHash
|
1818181c1f1f1fff |
|
VISUAL
colorHash
|
070000001c0 |
|
VISUAL
cropResistant
|
6171333232327c78 |
Code Analysis
Risk Score
50/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🔬 Threat Analysis Report
• Threat: Credential harvesting phishing kit
• Target: Microsoft users globally
• Method: Fake login form stealing email/phone/Skype and password
• Exfil: Unknown, likely sent to attacker's server
• Indicators: Domain mismatch, mimicked login form, no official URL
• Risk: HIGH - Immediate credential theft
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
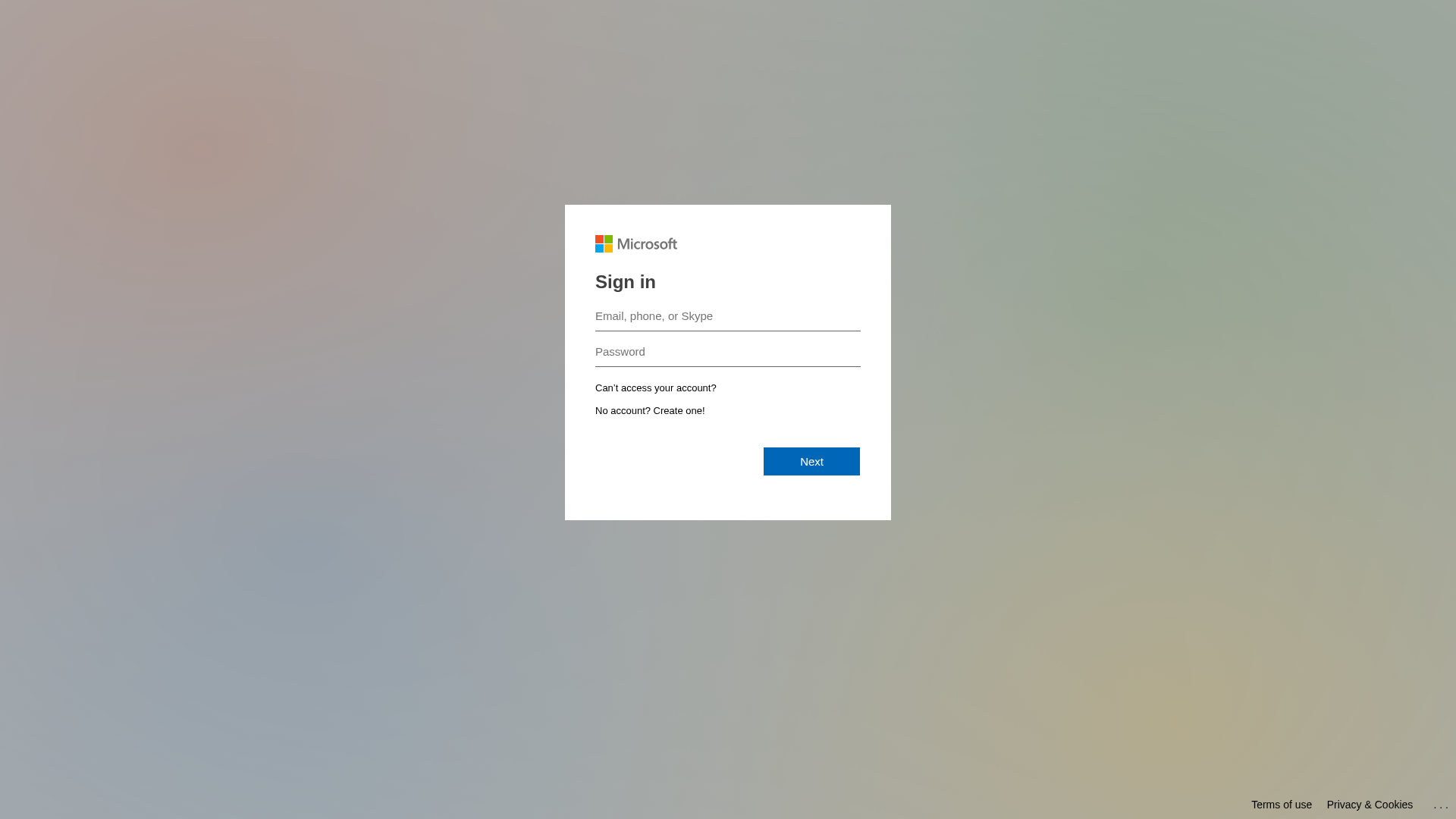
Microsoft
https://securityawareness.cc/landing/form/90273d17-767e-41c3...
Jan 10, 2026
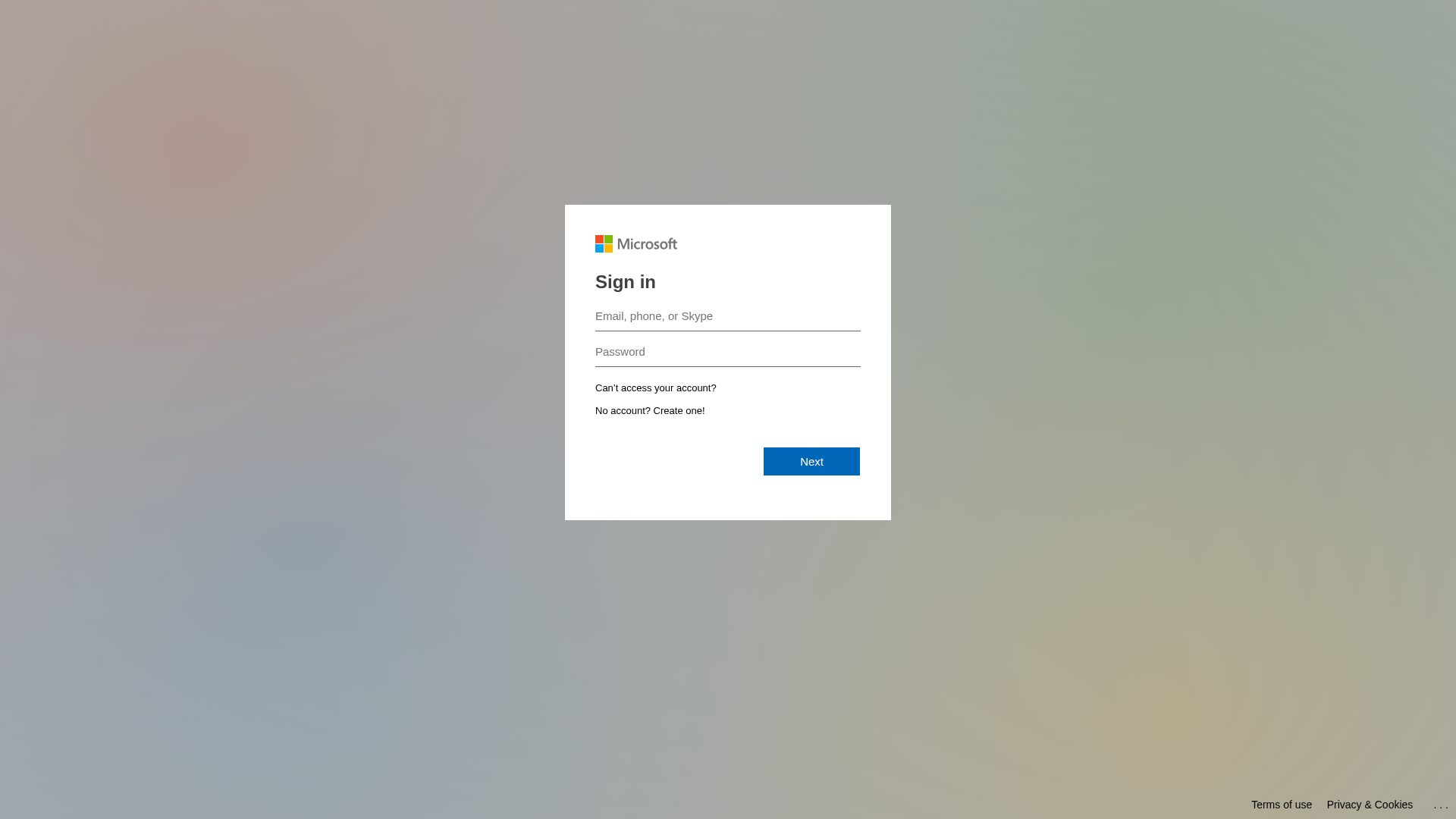
Microsoft
https://securityawareness.cc/landing/form/857b14f2-c167-4dbb...
Jan 01, 2026
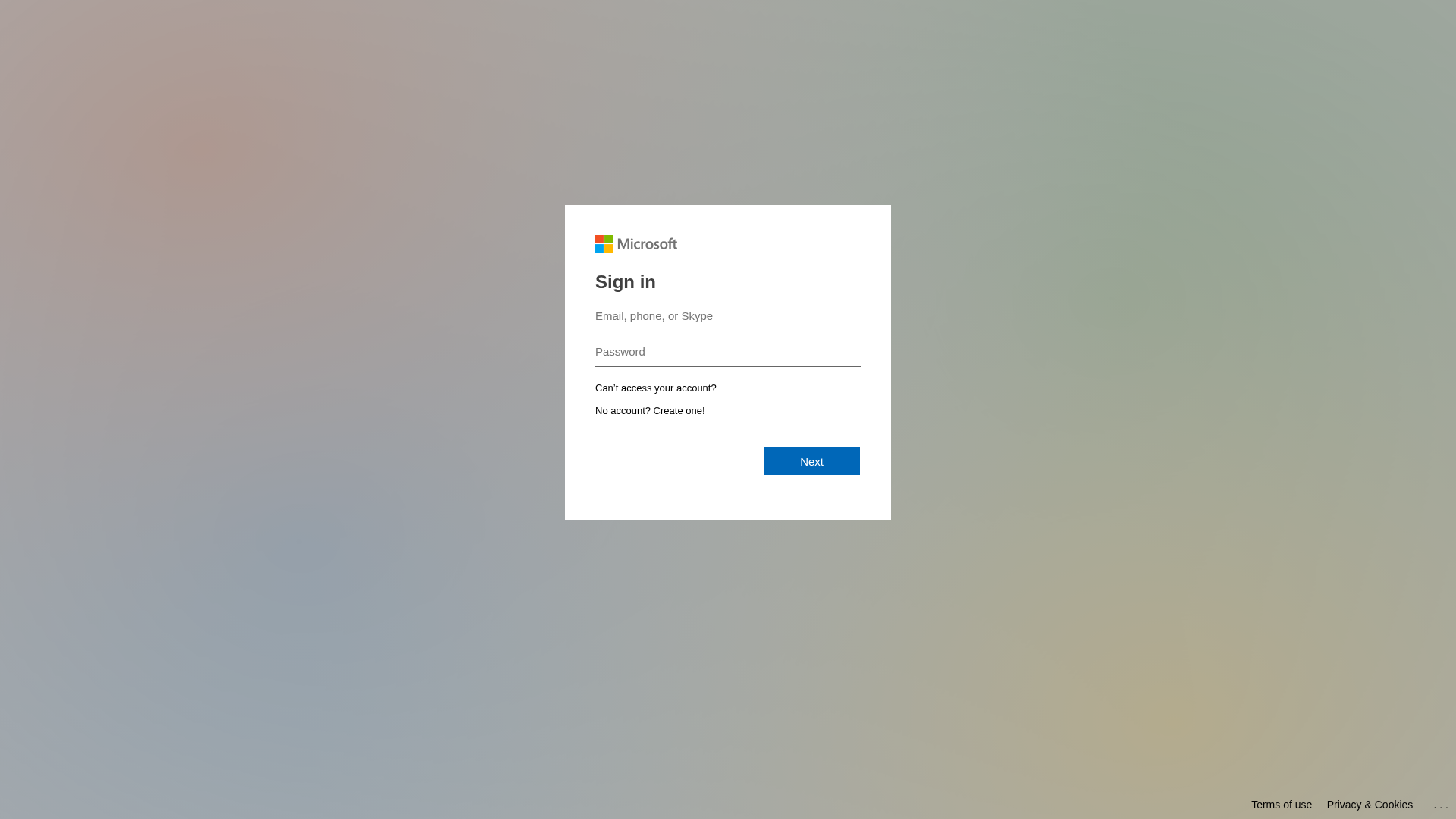
Microsoft
http://mgamt.com/landing/form/3261b7e4-cda3-4263-b1f5-8e5d4d...
Dec 28, 2025
Microsoft
https://mgamt.com/landing/form/2304cdba-1a5e-4680-902b-892d5...
Dec 25, 2025
No screenshot
Microsoft
https://securityawareness.cc/landing/form/10d2324c-1548-44bc...
Dec 11, 2025
Scan History for securityawareness.cc
Found 3 other scans for this domain