Phishing Analysis
Detailed analysis of captured phishing page
24
Risk Score
Low Risk
Threat Level: ALTO
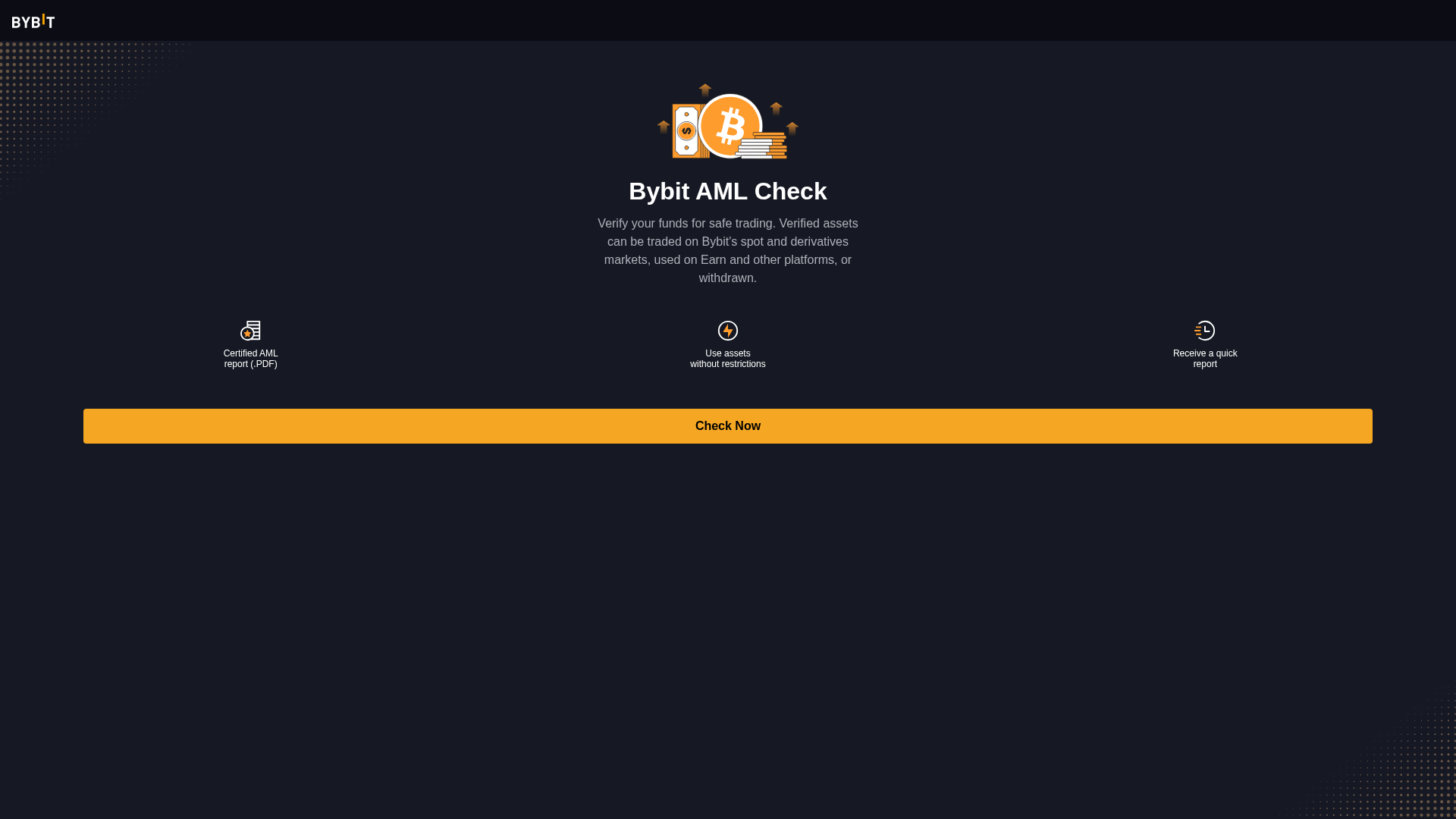
• Impersonating: Bybit
- • Threat: Bybit AML Check Phishing
- • Target: Bybit users worldwide
- • Method: Lures users with a fake AML check to steal credentials or personal information.
- • Exfil: The site likely exfiltrates data via JavaScript form submission to an unknown destination.
- • Indicators: New domain, domain doesn't match official site, generic TLD, form submission detected.
- • Risk: HIGH - Potential credential or personal information theft.
Visual Capture
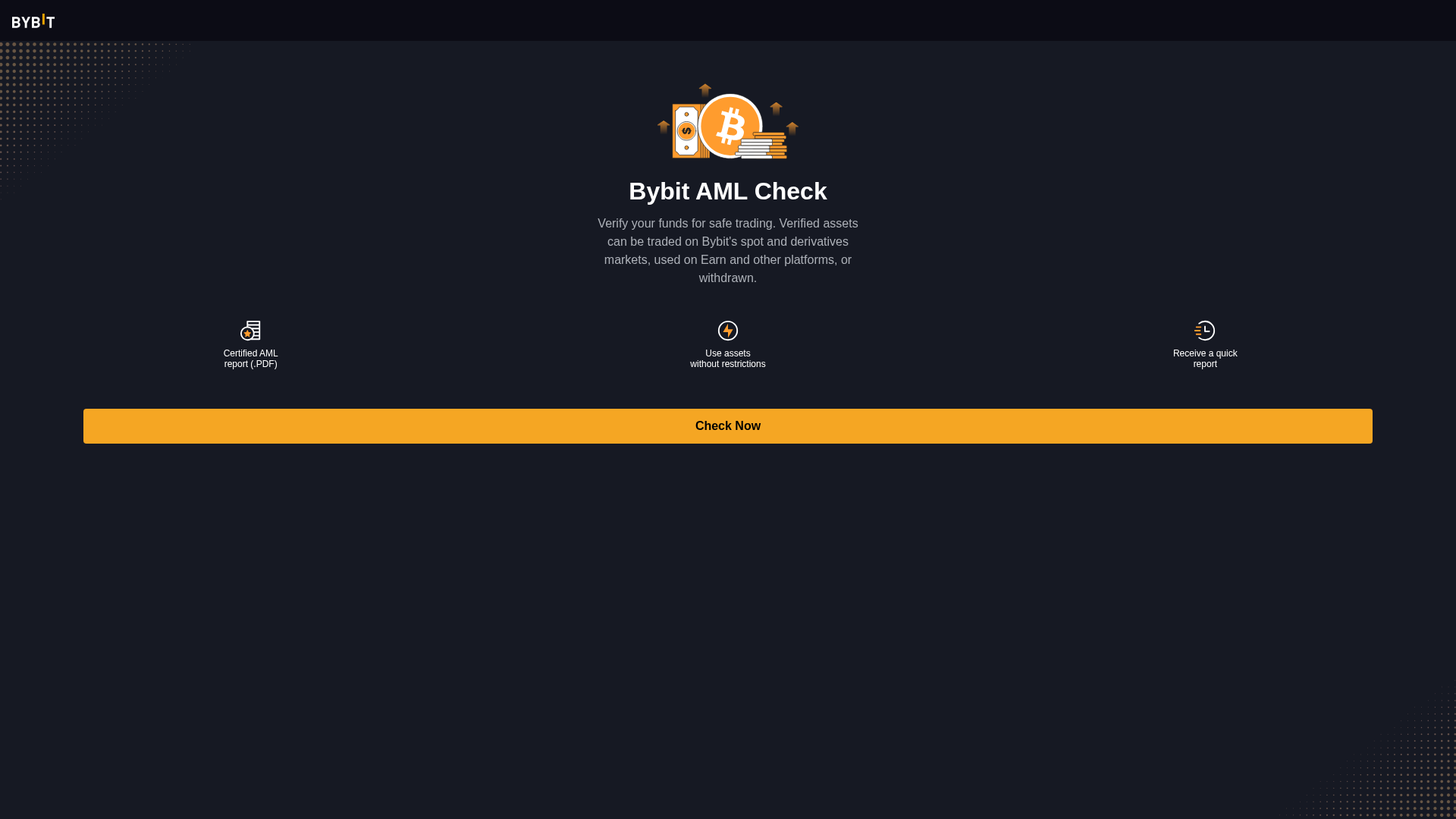
Detection Info
http://trust-bybit.click/
Detected Brand
Bybit
Country
International
Confidence
95%
HTTP Status
200
Report ID
b6430878-725…
Analyzed
2026-01-11 01:05
Final URL (after redirects)
https://trust-bybit.click/
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T10071AC709199EA3381A391E5AB724B2E32D08285DB5327140BF8D3DD5FEBEA8CE16044 |
|
CONTENT
ssdeep
|
48:nMyR/IDfkUGP8AvjLIusPY5cx5PDbW/ISpg/NNqqCU+LHV5pSWDVnNPCw32veV:nWzT3A7MusAexhDbWASpg14UQVlPFaeV |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
ccdc2e77a07322a3 |
|
VISUAL
aHash
|
001800ffff000000 |
|
VISUAL
dHash
|
54303396aa018201 |
|
VISUAL
wHash
|
809c1cffff420101 |
|
VISUAL
colorHash
|
38000038000 |
|
VISUAL
cropResistant
|
0010080c0c081000,54303396aa018201 |
Code Analysis
Risk Score
24/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🔬 Threat Analysis Report
• Threat: Bybit AML Check Phishing
• Target: Bybit users worldwide
• Method: Lures users with a fake AML check to steal credentials or personal information.
• Exfil: The site likely exfiltrates data via JavaScript form submission to an unknown destination.
• Indicators: New domain, domain doesn't match official site, generic TLD, form submission detected.
• Risk: HIGH - Potential credential or personal information theft.
Similar Websites
Pages with identical visual appearance (based on perceptual hash)