
Phishing Analysis
Detailed analysis of captured phishing page
100
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: Rolls-Royce
⚠ Fatores de Risco
- Contém 1 token(s) de bot Telegram para exfiltração de credenciais
- Contém 7 formulário(s) com submissão JavaScript
- Ofuscação JavaScript detectada (5 padrões)
- Indicadores de roubo de credenciais detectados
- Indicadores de roubo de otp/2fa detectados
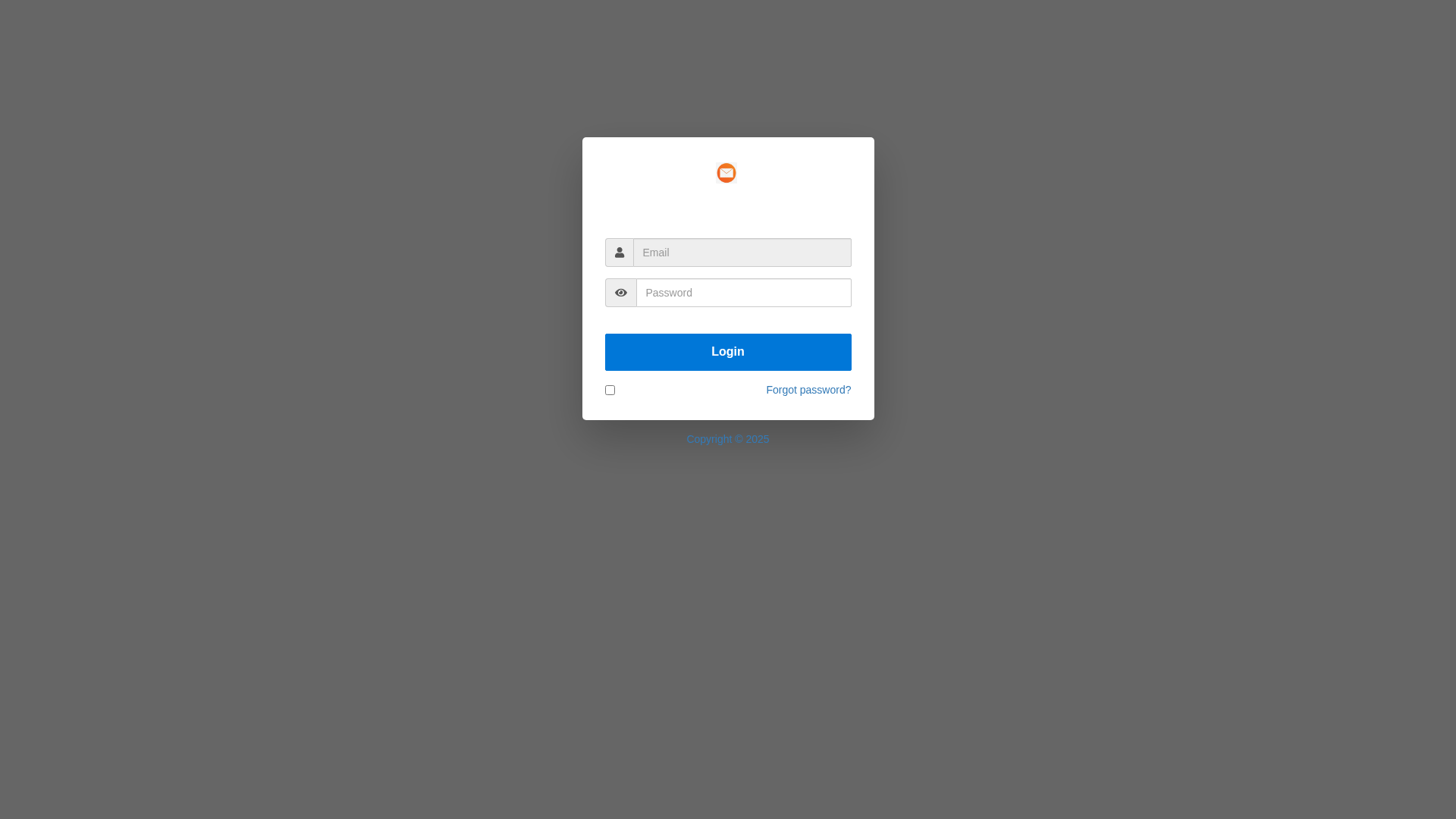
Visual Capture
Detection Info
http://rollsroyce.temp.domains/~anayansiprestamo/Kawa.html#
Detected Brand
Rolls-Royce
Country
International
Confidence
100%
HTTP Status
200
Report ID
bcf3ddb8-9fe…
Analyzed
2026-01-07 16:29
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T17561307180158D335A97C6E8AAE1EB1F6182824CCB571F045AF853AF7BDFD508B92298 |
|
CONTENT
ssdeep
|
48:Y1YQpaJ5OKNeBIBJw3xzPPBhl3jwifaqNTCSt6pFFkM+byz3rifSDQkz8DBm:YhIjpwtPP3lDf/5CRNb+63rtVzf |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
9999666666339999 |
|
VISUAL
aHash
|
0018181818000000 |
|
VISUAL
dHash
|
4cb2b2b2320c1000 |
|
VISUAL
wHash
|
f8f8fcfc38303030 |
|
VISUAL
colorHash
|
070000001c0 |
|
VISUAL
cropResistant
|
8a88b2a280333382,4cb2b2b2320c1000 |
Code Analysis
Risk Score
100/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Banking
🎣 Personal Info
Telegram Exfiltration
🔐 Credential Harvesting Forms
🔒 Obfuscation Detected
- atob
- fromCharCode
- unescape
- unicode_escape
- js_packer
🔑 Telegram Bot Tokens (1)
- 7567013646:AAGV...EqRerohs
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
No screenshot
Unknown
https://wasiu.standard.us-east-1.oortstorages.com/verificati...
Jan 07, 2026
No screenshot
Unknown
https://online-secured-access-webmail-confi.vercel.app/
Jan 07, 2026
MetaMask
https://bafybeictihwjrxpmvmzzsfyss67ifszryfbhvluo3m7ksk25ffj...
Jan 07, 2026
Unknown
https://aditivosforte.com/all.html
Jan 07, 2026
No screenshot
Unknown
https://kjhkjh-o4ul.vercel.app/hgcfgvgh.html
Jan 07, 2026