
Phishing Analysis
Detailed analysis of captured phishing page
95
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: VK
⚠ Risk Factors
- JavaScript obfuscation detected (6 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
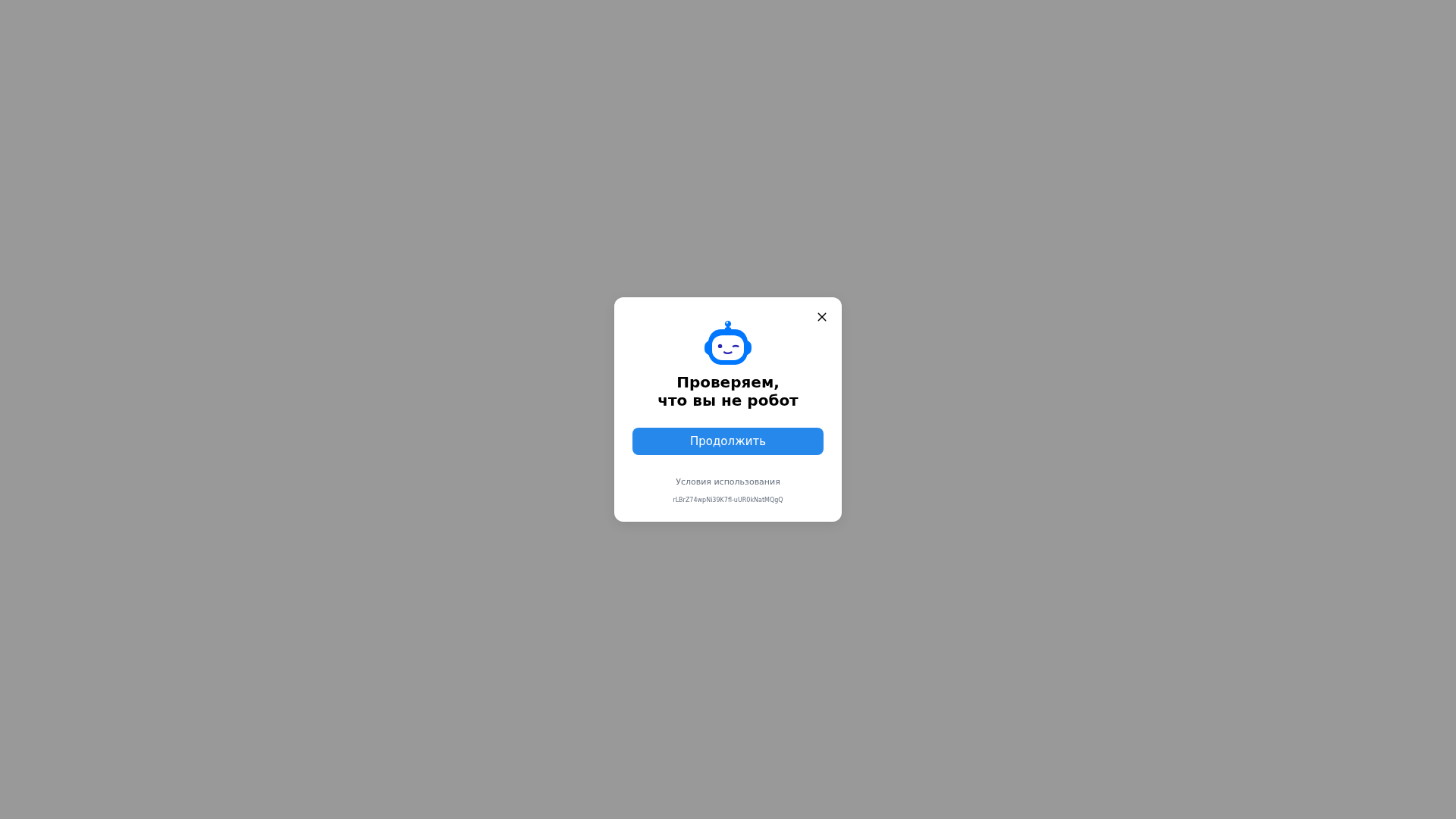
Detection Info
https://away.vk.com/away.php?rh=ed5bc5bb-a7ba-499f-9689-ef26703d6392
Detected Brand
VK
Country
Unknown
Confidence
100%
HTTP Status
200
Report ID
c61e86f6-3b3…
Analyzed
2026-01-06 03:06
Final URL (after redirects)
https://away.vk.com/challenge.html?tid=rLBrZ74wpNi39K7fl-uUR0kNatMQgQ&hash429=fNJbXE1uO6KvLB7fPCATq1pEJPyYblmruxxOF8PEiqAYa5lbNIwwCLT9V2fY86U079RxgV6qaLB_BNX1a05BOyH_ZZ5ZI-2FpDRHXCOnALdTgW7aSJEaxkY5LSczdYUDDjh7hGqDihLF6oj9&sign=ftGTcCbjJX_mPiYV4O9TxQ&back=https%3A%2F%2Faway.vk.com%2Faway.php%3Frh%3Ded5bc5bb-a7ba-499f-9689-ef26703d6392&origin=&lang_id=
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T16CD172E4AA3CA63D140F87ACCBAEB681235FA0EDF3170554638E96B10587E6CE946C54 |
|
CONTENT
ssdeep
|
96:e35KFSe0BlTSc/Q04JvN/Un4jFSe0BlTSc/Q04JWatPTOYuFA9ed/WqtuxE:ZAN3J4JvBAN3J4J/iVW9eJW4uu |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
cccc3333cccc6633 |
|
VISUAL
aHash
|
0000181818180000 |
|
VISUAL
dHash
|
100c32b2b2320c10 |
|
VISUAL
wHash
|
3c3c3c3c1c1c0000 |
|
VISUAL
colorHash
|
070000001c0 |
|
VISUAL
cropResistant
|
100c32b2b2320c10 |
Code Analysis
Risk Score
95/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Card Stealer
🎣 Banking
🎣 Personal Info
🔒 Obfuscation Detected
- atob
- eval
- fromCharCode
- unescape
- document.write
- base64_strings
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
VK
https://away.vk.com/away.php?rh=cfd366b6-171c-4507-8de7-2c09...
Jan 06, 2026
VK
https://976tep2sg8.vk.com/challenge.html?tid=l:KaVaYQfOJDTUt...
Jan 06, 2026
No screenshot
Unknown
https://976tep2sg8.vk.com/challenge.html?tid=l:6uMgaKKwwETt6...
Jan 06, 2026
VK
https://away.vk.com/away.php?rh=54635185-f7f2-4aa4-84f1-46c5...
Jan 06, 2026
No screenshot
Unknown
https://away.vk.com/away.php?rh=5c50e51d-3c82-4079-9532-d08e...
Jan 06, 2026
Scan History for away.vk.com
Found 10 other scans for this domain
-
https://away.vk.com/away.php?rh=cfd366b6-171c-4507...
https://away.vk.com/away.php?rh=54635185-f7f2-4aa4...
https://away.vk.com/away.php?rh=5c50e51d-3c82-4079...
https://away.vk.com/away.php?rh=6d55571d-68fc-481c...
https://away.vk.com/away.php?rh=475c33a9-524d-48f1...
https://away.vk.com/away.php?rh=ad73d2d3-158f-4f26...
https://away.vk.com/away.php?rh=31d2d1ce-ece4-4199...
https://away.vk.com/away.php?rh=e1e2fa49-4236-450e...
https://away.vk.com/away.php?rh=fccbf99d-2a9a-4108...
https://away.vk.com/away.php?rh=a8fc4265-e6cc-4389...