
Phishing Analysis
Detailed analysis of captured phishing page
100
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: SafePal
- • Threat: Credential harvesting phishing kit
- • Target: SafePal users
- • Method: Fake login form stealing user credentials
- • Exfil: Data sent via JavaScript form submission
- • Indicators: Domain mismatch, forms detected, obfuscated JavaScript
- • Risk: HIGH - Immediate credential theft
⚠ Risk Factors
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
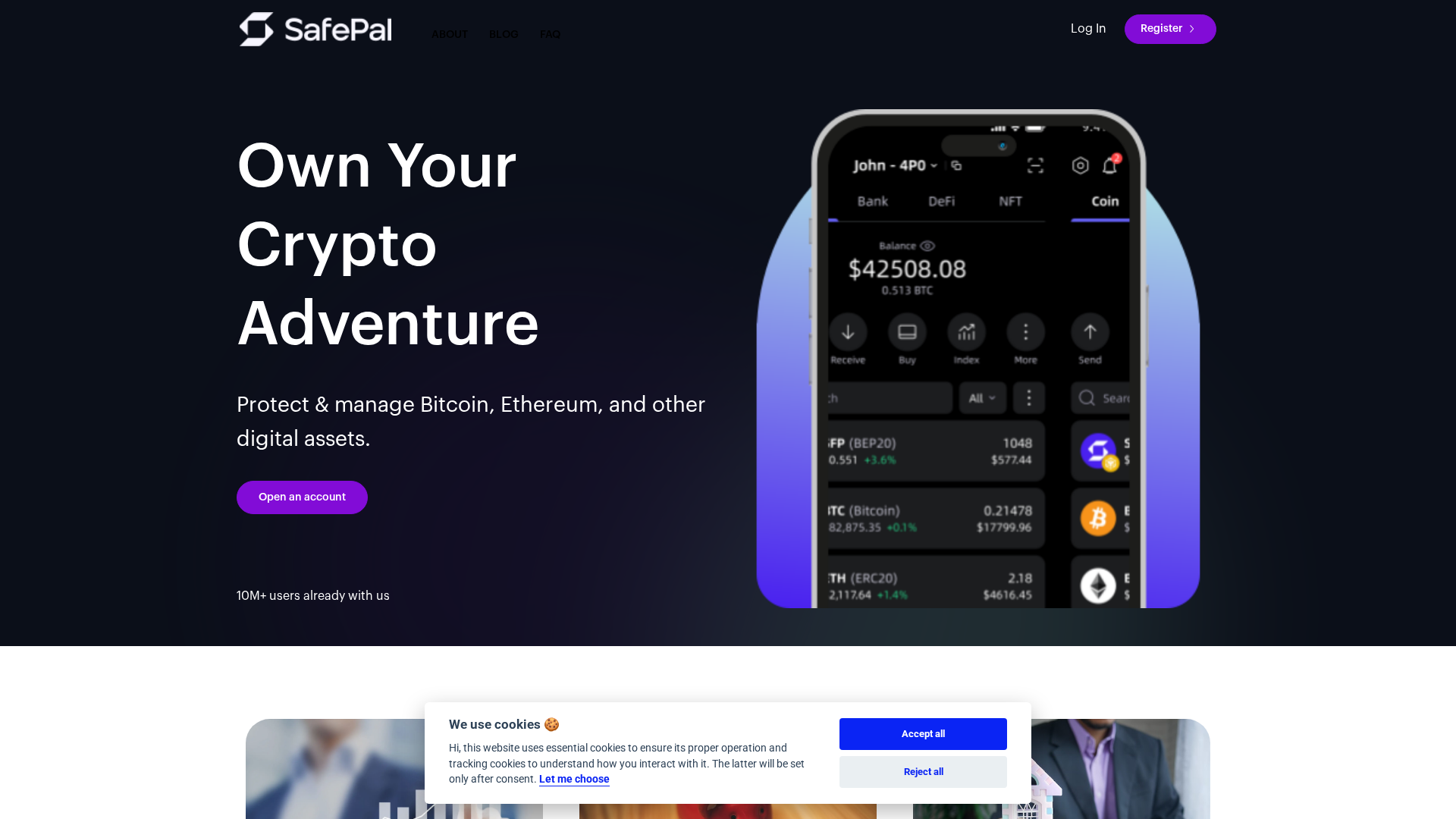
Detection Info
https://safepalportfolio.com
Detected Brand
SafePal
Country
International
Confidence
100%
HTTP Status
200
Report ID
cc9e0ee3-4ab…
Analyzed
2026-01-11 06:33
Final URL (after redirects)
https://safepalportfolio.com/
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T16103E731B0702D7F024B83D4B2306B9EF193934FC6635296D3F587593BEADA1E8165A8 |
|
CONTENT
ssdeep
|
768:tZhuuyEEMVh8S4iZVXxTVjFPeRcpVhe9WK:HhNyEEMVh8GZVXVeRcpm4K |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
8951ea16edc539e1 |
|
VISUAL
aHash
|
000000000000ffff |
|
VISUAL
dHash
|
9cc8d2d292d43323 |
|
VISUAL
wHash
|
40604a6a4a0effff |
|
VISUAL
colorHash
|
39006200008 |
|
VISUAL
cropResistant
|
7df18d6589110921,8170ce2148445048,28020833333b332b,96ccd2d2d29296dc,5d63e76727213131 |
Code Analysis
Risk Score
100/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Card Stealer
🎣 Banking
🎣 Personal Info
🔬 Threat Analysis Report
• Threat: Credential harvesting phishing kit
• Target: SafePal users
• Method: Fake login form stealing user credentials
• Exfil: Data sent via JavaScript form submission
• Indicators: Domain mismatch, forms detected, obfuscated JavaScript
• Risk: HIGH - Immediate credential theft
🔒 Obfuscation Detected
- eval
- fromCharCode
- base64_strings