
Phishing Analysis
Detailed analysis of captured phishing page
79
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: Trust Wallet
- • Threat: Credential harvesting phishing kit
- • Target: Trust Wallet users
- • Method: Fake website impersonating Trust Wallet
- • Exfil: Data sent via JavaScript form submission
- • Indicators: Domain mismatch, obfuscated JavaScript, forms detected
- • Risk: HIGH - Immediate credential theft
⚠ Risk Factors
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
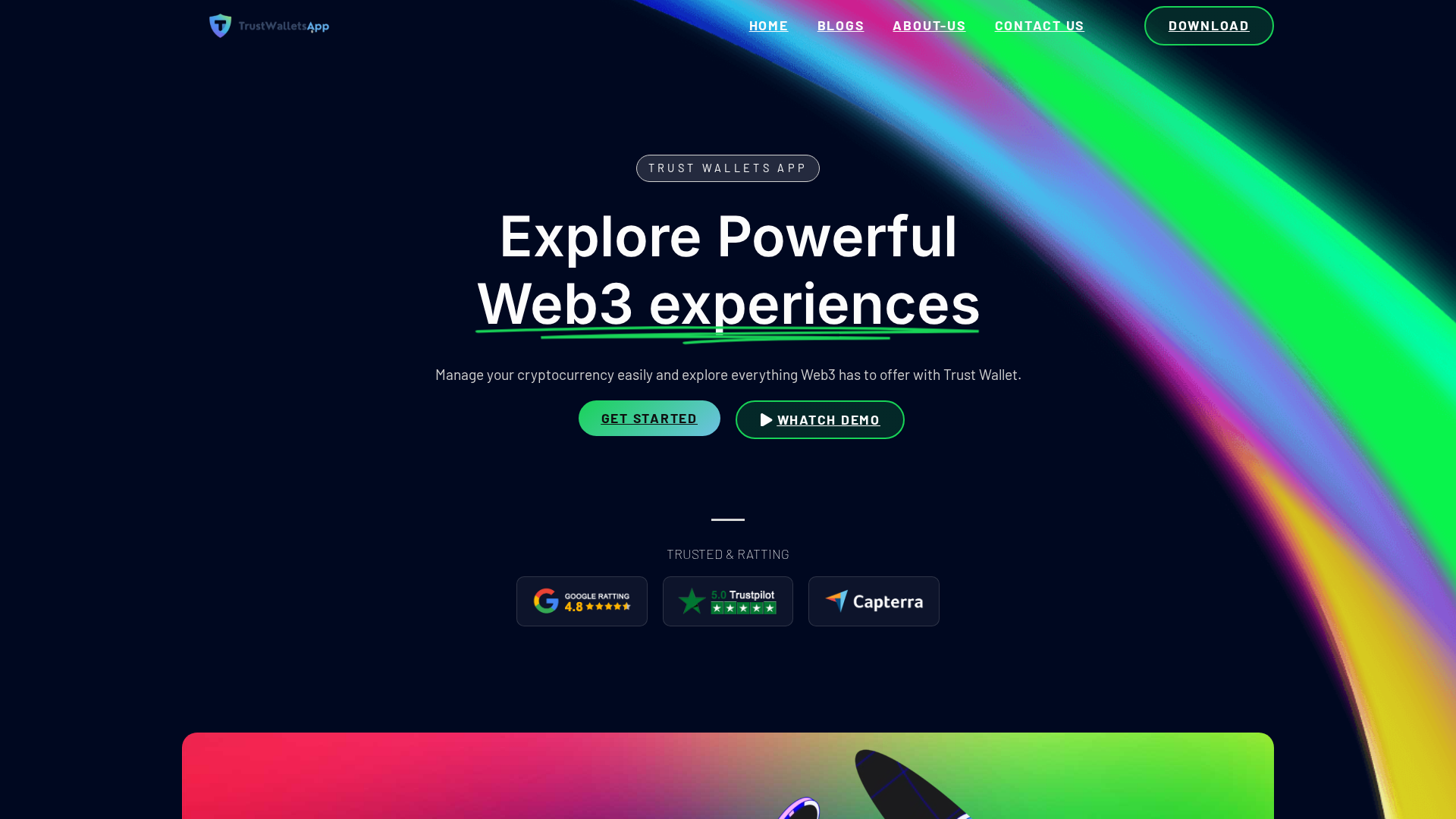
Detection Info
https://trustwalletsapp.com
Detected Brand
Trust Wallet
Country
International
Confidence
100%
HTTP Status
200
Report ID
d6f6a00d-ae2…
Analyzed
2026-01-11 06:39
Final URL (after redirects)
https://trustwalletsapp.com/
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T1CDE353713A06651631AF43CFD227254C90C1D6CDEAD1ABE4D6F08338E6F5DA4BBE2681 |
|
CONTENT
ssdeep
|
3072:gbxH7vIkgpSzHCVrfo5kETunfAXa5Ez+YF8W:gbxH7vIkgpSzHCVrfo5kETunfAXgW |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
a815d27adb4b8969 |
|
VISUAL
aHash
|
0e061f1b0101017f |
|
VISUAL
dHash
|
9c3c7673b333b9d4 |
|
VISUAL
wHash
|
0e0f3f1f1b09017f |
|
VISUAL
colorHash
|
38001000401 |
|
VISUAL
cropResistant
|
a0f1789c5f8f9756,bec7e170b8582c2c,f9b9b1b191999959,9c3c7673b333b9d4,3c9d8e87c3e3f1f8,220084e27138dcde |
Code Analysis
Risk Score
79/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Banking
🎣 Personal Info
🔬 Threat Analysis Report
• Threat: Credential harvesting phishing kit
• Target: Trust Wallet users
• Method: Fake website impersonating Trust Wallet
• Exfil: Data sent via JavaScript form submission
• Indicators: Domain mismatch, obfuscated JavaScript, forms detected
• Risk: HIGH - Immediate credential theft
🔒 Obfuscation Detected
- atob
- fromCharCode
- unicode_escape