Phishing Analysis
Detailed analysis of captured phishing page
100
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: Steam
⚠ Risk Factors
- Brand impersonation of Steam on non-official domain
- Discord webhook detected for data exfiltration
- Contains 11 form(s) with JavaScript submission
- JavaScript obfuscation detected (6 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
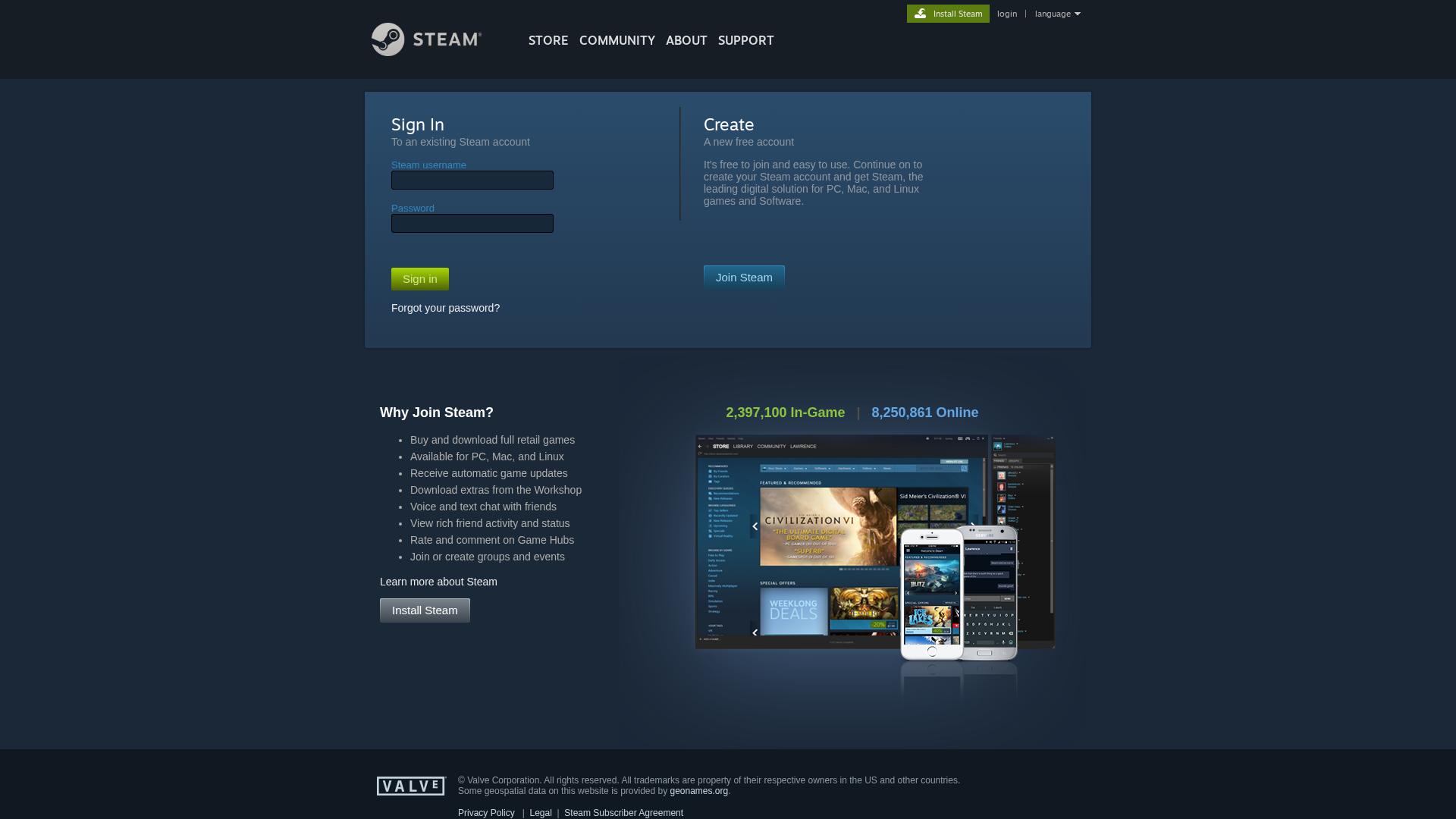
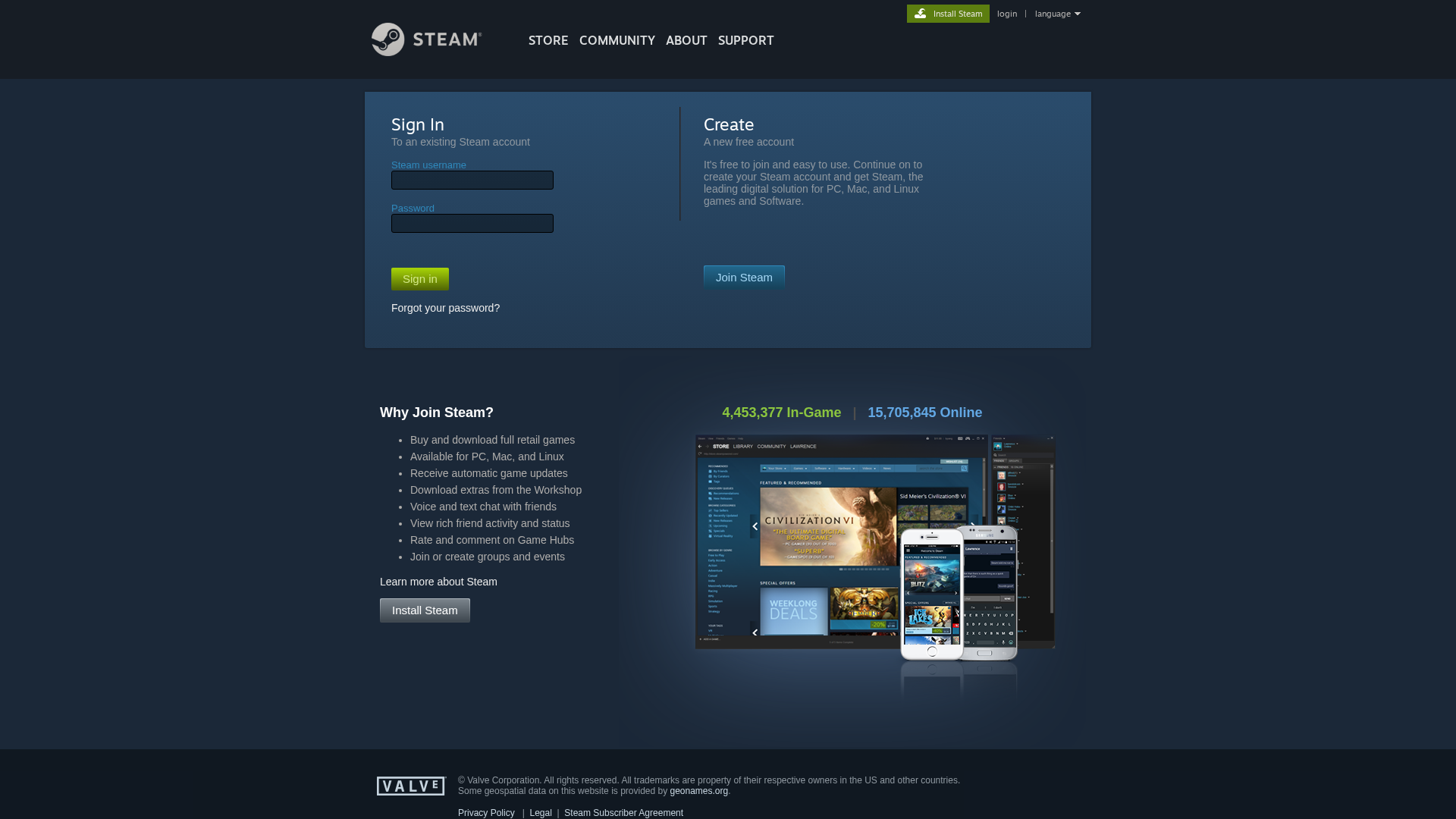
Visual Capture
Detection Info
https://tr.ee/steamlogin
Detected Brand
Steam
Country
Unknown
Confidence
100%
HTTP Status
200
Report ID
dffac9e1-854…
Analyzed
2026-01-10 01:50
Final URL (after redirects)
https://pannkook77rizz.github.io/FakeSteam/
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T1F773557A51394637DB83D3847C76A71B768B8A49BB165F064AF813B40F8EC84CE39D48 |
|
CONTENT
ssdeep
|
1536:VPg1c74TvHkI404Xd1civg+pqxqpGVfYfewBl4U:iWUWGkBl4U |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
9bc6669b64365934 |
|
VISUAL
aHash
|
203c3c203c3c0c00 |
|
VISUAL
dHash
|
4971714858595960 |
|
VISUAL
wHash
|
343d3c3c3c3c3f00 |
|
VISUAL
colorHash
|
08007000000 |
|
VISUAL
cropResistant
|
f0f8fc7efeee4e4c,4971714858595960 |
Code Analysis
Risk Score
100/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Banking
🎣 Personal Info
Discord Webhook
🔒 Obfuscation Detected
- eval
- fromCharCode
- unescape
- document.write
- unicode_escape
- base64_strings
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
Scan History for tr.ee
Found 10 other scans for this domain
-
https://linktr.ee/currently.att
https://linktr.ee/attnews11
https://linktr.ee/digitalpontinhos
https://linktr.ee/readdid
http://linktr.ee/PayBiz
https://linktr.ee/mlohome
https://linktr.ee/m1i2e3n4
https://linktr.ee/youssefgdr007?lt_utm_source=lt_a...
https://linktr.ee/unlockitnow
https://tr.ee/1t1QTDtpFK