
Phishing Analysis
Detailed analysis of captured phishing page
100
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: Mail.com
⚠ Factores de Riesgo
- Suplantación de marca Mail.com en dominio no oficial
- Contiene 5 formulario(s) con envío JavaScript
- Ofuscación JavaScript detectada (7 patrones)
- Indicadores de robo de credenciales detectados
- Indicadores de robo de otp/2fa detectados
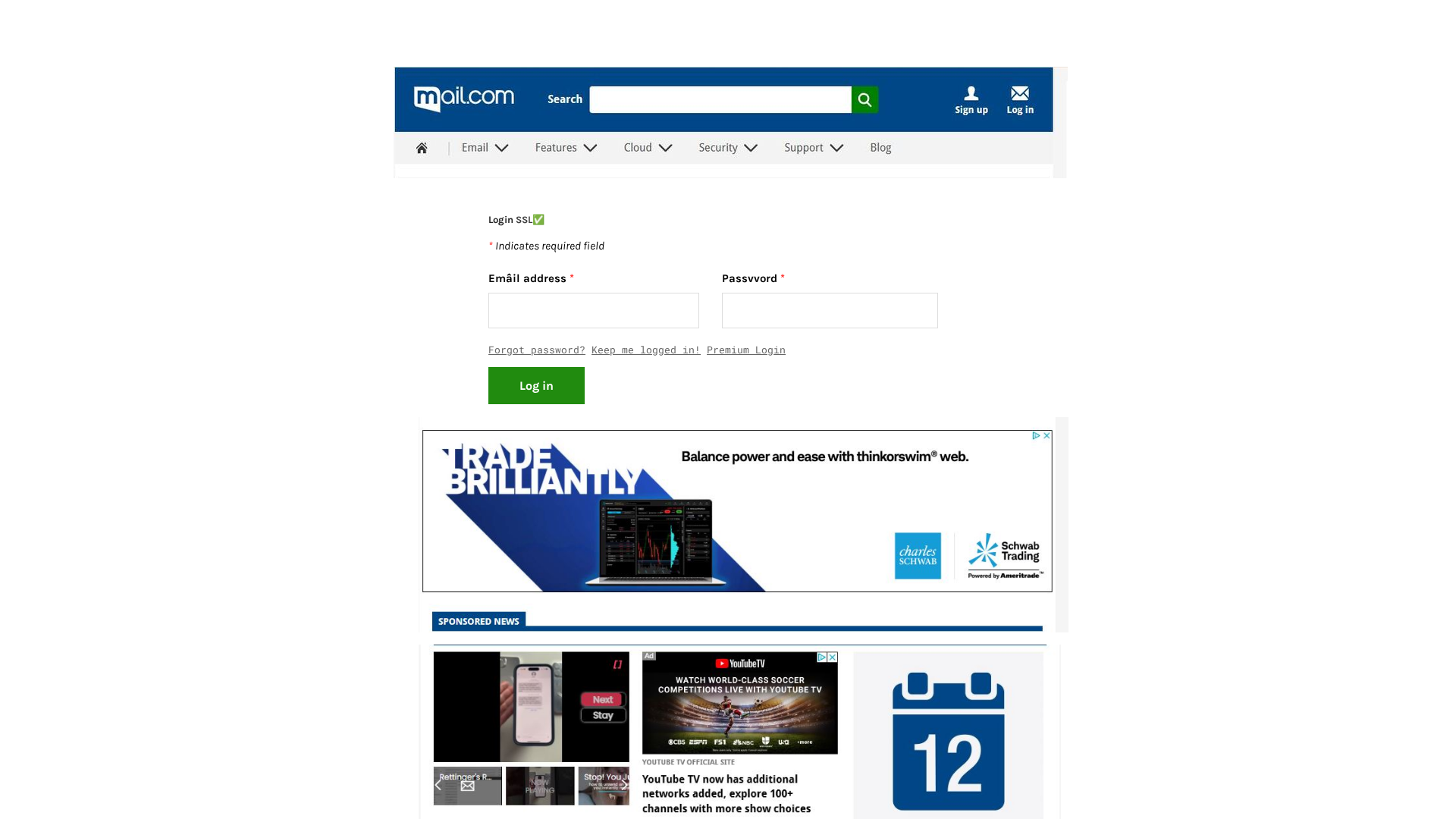
Visual Capture
Detection Info
https://mmwmail.weebly.com/
Detected Brand
Mail.com
Country
International
Confidence
100%
HTTP Status
200
Report ID
e52d5c21-082…
Analyzed
2026-01-08 07:39
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T18A32DCE1C501FA3B476691C4E7726F0B3791C389DF530941E3B887ABABCAC60CA1659D |
|
CONTENT
ssdeep
|
192:kvEb6x0Vn/zH715lUGoxbyvBLVH7IE0cd2QaIOkyIMIBjkyIZBjkyIyBTkyIrBf:kvEb6x01bmzxb4BLVHUEDd2N1k/MIBjN |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
b1ce6433ccc6d392 |
|
VISUAL
aHash
|
c3c3ffffcfcfc3c3 |
|
VISUAL
dHash
|
969600169e9a9e96 |
|
VISUAL
wHash
|
c3c3c3c3c3c3c3c3 |
|
VISUAL
colorHash
|
07000000180 |
|
VISUAL
cropResistant
|
969600169e9a9e96,a280a2a2a2a280a2,6186696161699661,c6e7636327250596,5757575757570757,95949694d4d63f3b |
Code Analysis
Risk Score
100/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Card Stealer
🎣 Banking
🎣 Personal Info
🔐 Credential Harvesting Forms
🔒 Obfuscation Detected
- atob
- eval
- fromCharCode
- unescape
- hex_escape
- unicode_escape
- base64_strings