
Phishing Analysis
Detailed analysis of captured phishing page
70
Risk Score
High Risk
Threat Level: CRITICAL
• Impersonating: Copart
- • Threat: Credential harvesting phishing targeting Copart users.
- • Target: Copart account holders.
- • Method: Fake sign-in page to steal user credentials (email and password).
- • Exfil: Likely to a remote server controlled by the attacker, but details are unavailable without further code analysis.
- • Indicators: Mismatched domain 'sso-security.com', which is different from the official Copart domain (copart.com).
- • Risk: HIGH - The site attempts to steal login credentials, potentially leading to account compromise.
⚠ Risk Factors
- Brand impersonation of Copart on non-official domain
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
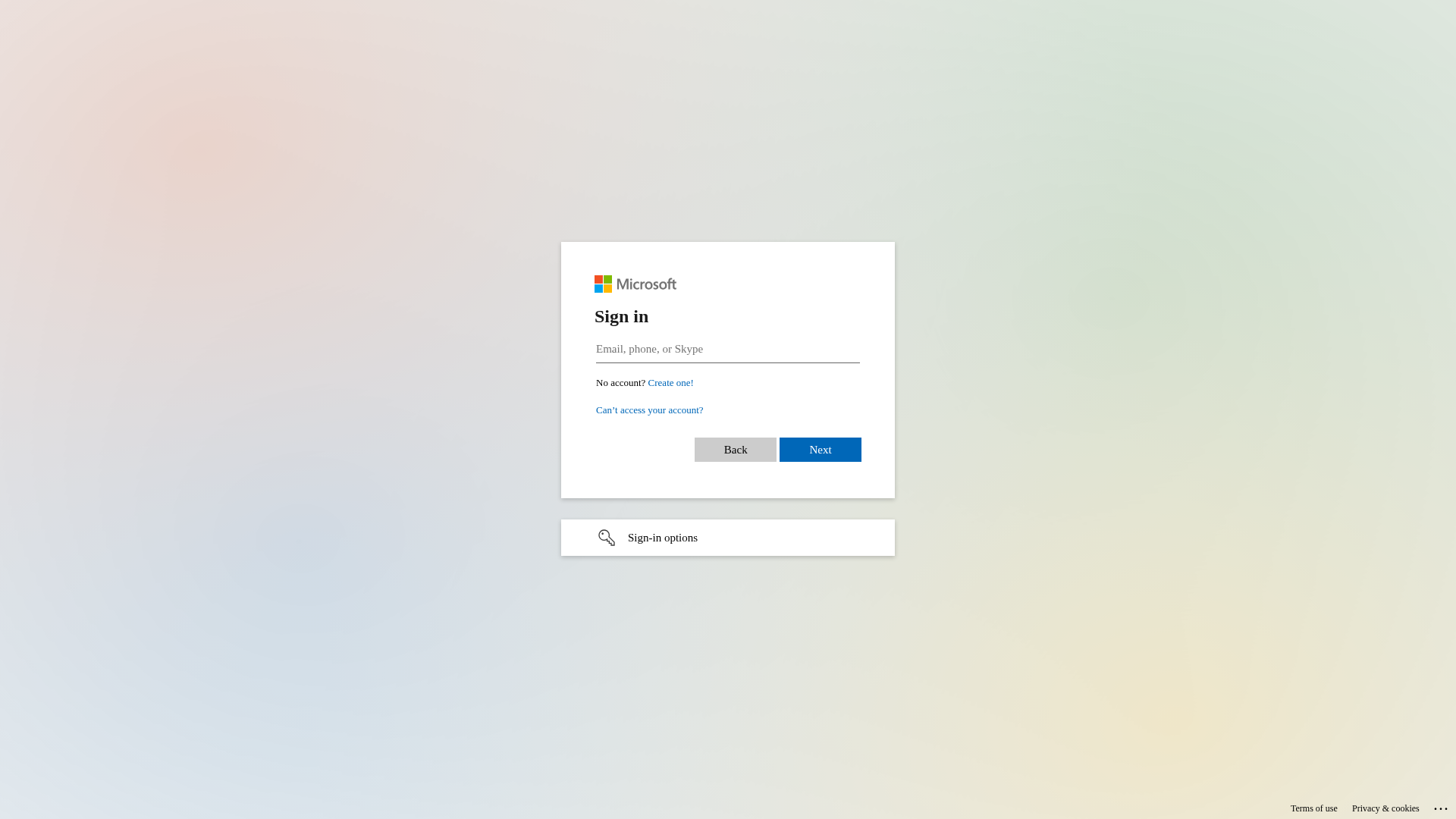
Visual Capture
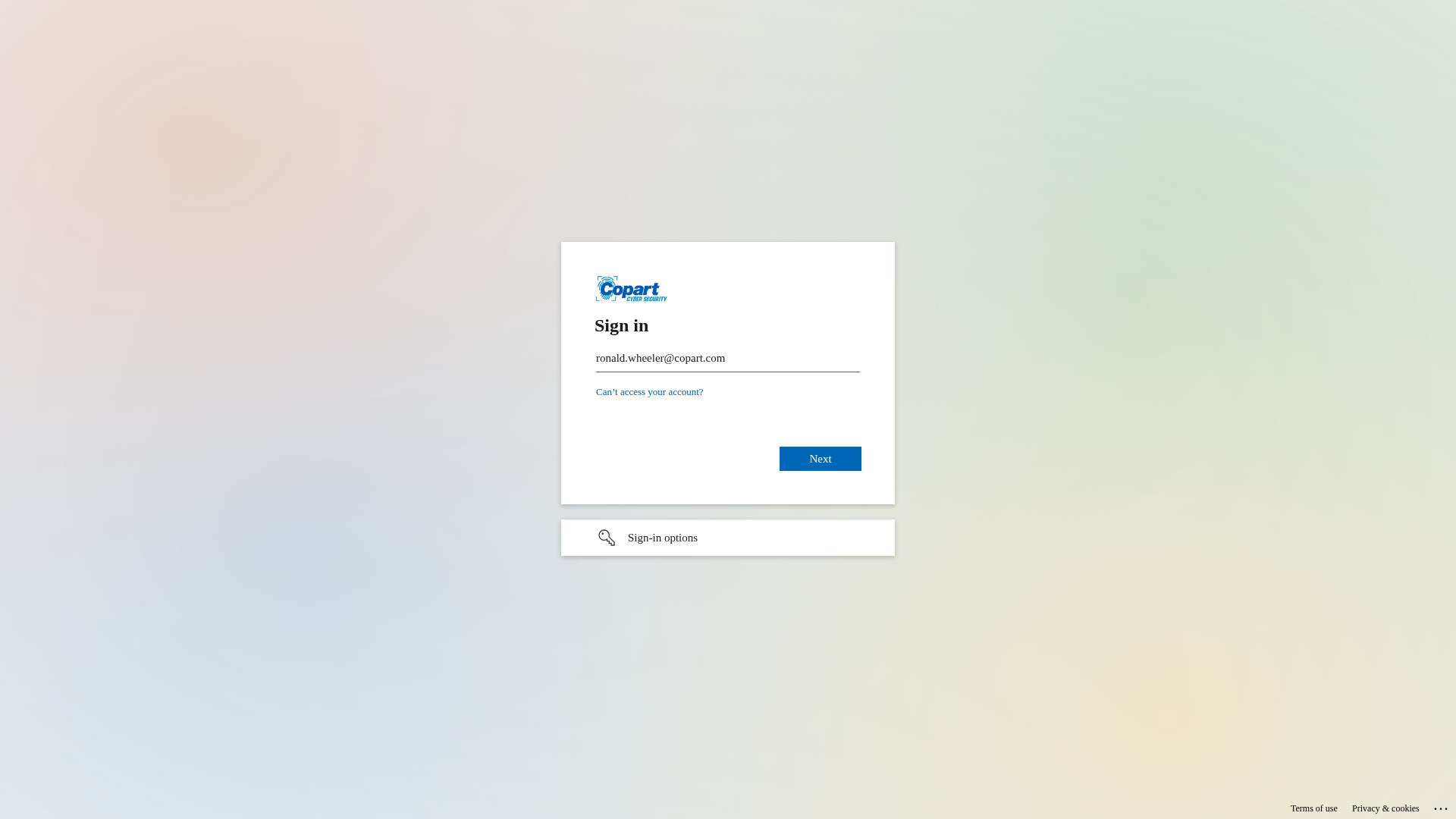
Detection Info
https://sso-security.com/8mdoRKygydY_ntWLug?/aG94aHVudA
Detected Brand
Copart
Country
International
Confidence
100%
HTTP Status
200
Report ID
e9a197d9-be1…
Analyzed
2025-12-29 13:15
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T170D1FE7060509D3B4283C6D4B3B9AB9F7394C346EA87565A63F4C39C0FE3E56CC1A226 |
|
CONTENT
ssdeep
|
96:nIpkCGTHRPyISakrwkMns39TbJG9KjsWsjOVo0U2gs0sjOVZOVJQ6Q6ynQjNsjOg:9BSak8C9TbJG9ah61ZOVJQyyQjhu |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
9c497326cc99d966 |
|
VISUAL
aHash
|
18001818191f0f9f |
|
VISUAL
dHash
|
7161713331727d38 |
|
VISUAL
wHash
|
191818181f1f1fff |
Code Analysis
Risk Score
70/100
Threat Level
CRITICAL
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Personal Info
🔬 Threat Analysis Report
• Threat: Credential harvesting phishing targeting Copart users.
• Target: Copart account holders.
• Method: Fake sign-in page to steal user credentials (email and password).
• Exfil: Likely to a remote server controlled by the attacker, but details are unavailable without further code analysis.
• Indicators: Mismatched domain 'sso-security.com', which is different from the official Copart domain (copart.com).
• Risk: HIGH - The site attempts to steal login credentials, potentially leading to account compromise.
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
Microsoft
http://inner.website/pcdde712fh20d94f742bc3a42131444b38b5.ht...
Jan 09, 2026
Microsoft
https://inner.website/yba964a42c4b7d4e62la770d4a1827d382b7.h...
Jan 09, 2026
Microsoft
https://inner.website/y023e62ecc47bd45efl8a100d2888677a163.h...
Jan 09, 2026
Microsoft
https://inner.website/yd0dd9503c13e84494l82ec464e8fa52549d.h...
Jan 09, 2026
No screenshot
Microsoft
https://inner.website/p8f95d256hfeeb436d2a4b540cc1ae756976.h...
Jan 09, 2026
Scan History for sso-security.com
Found 10 other scans for this domain
-
https://sso-security.com/pSWUhYWFe0hRfvxBhg?=useri...
https://sso-security.com/tuJwHdkl4Xc6v60N?=userid&...
https://sso-security.com/mwNw9yK7zSMRZa4?=userid&m...
https://sso-security.com/V6ocws3yf6a162k?=userid&m...
https://sso-security.com/yDggbRnMeqV36P0?=userid&m...
https://sso-security.com/oZ9LZteAbpu9?=userid&mess...
https://sso-security.com/g28Wrc83vcT5d48?/aG94aHVu...
https://sso-security.com/W0Sy9LNGpj7PPSk?=userid&m...
https://sso-security.com/sdtaSCjL3SMXheo?=userid&m...
https://sso-security.com/wPkmh20MmRTxVEwAhQ?=useri...