Phishing Analysis
Detailed analysis of captured phishing page
Visual Capture
No screenshot available
Detection Info
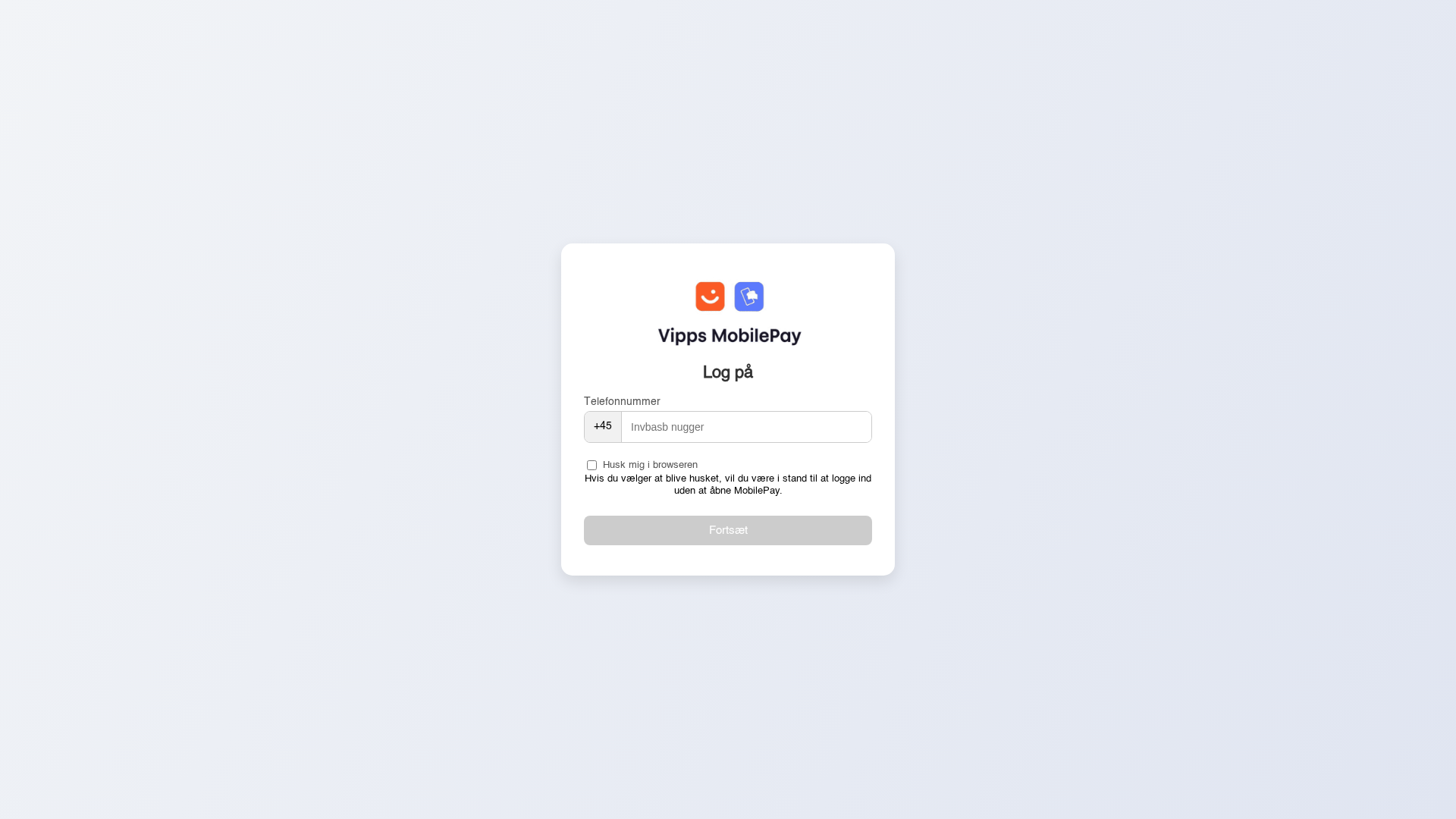
https://faramahd.ir/mobilepay/numero.htm
Detected Brand
Vipps MobilePay
Country
International
Confidence
70%
HTTP Status
200
Report ID
ec88ff61-23c…
Analyzed
2026-01-10 19:04
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T16721773058159C2AD935C3B15FD1E94517BA8F41CE493C40D5D4775F0BDAC98D86F744 |
|
CONTENT
ssdeep
|
24:bs6sCIyBKTRtxosGH7szaD1imqGDplYSZqupPVMSV:46ooKnq/qGDLVXV |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
db8c643199ce6699 |
|
VISUAL
aHash
|
f0f0f8f8f8e0c0c0 |
|
VISUAL
dHash
|
0000282810080000 |
|
VISUAL
wHash
|
f8f0f8f8f8e0e0c0 |
|
VISUAL
colorHash
|
07003018000 |
|
VISUAL
cropResistant
|
0000282810080000 |
Code Analysis
Threat Level
MEDIO
🔬 Threat Analysis Report
• Threat: Potential phishing targeting Vipps MobilePay users.
• Target: Vipps MobilePay users, potentially in Denmark
• Method: Fake login form is used to collect phone numbers.
• Exfil: Data exfiltration target is unknown, form action to ./post/index.php
• Indicators: Unofficial domain, Danish language, requests phone number.
• Risk: MEDIUM - Potential credential harvesting.
🔐 Credential Harvesting Forms
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
Scan History for faramahd.ir
Found 1 other scan for this domain