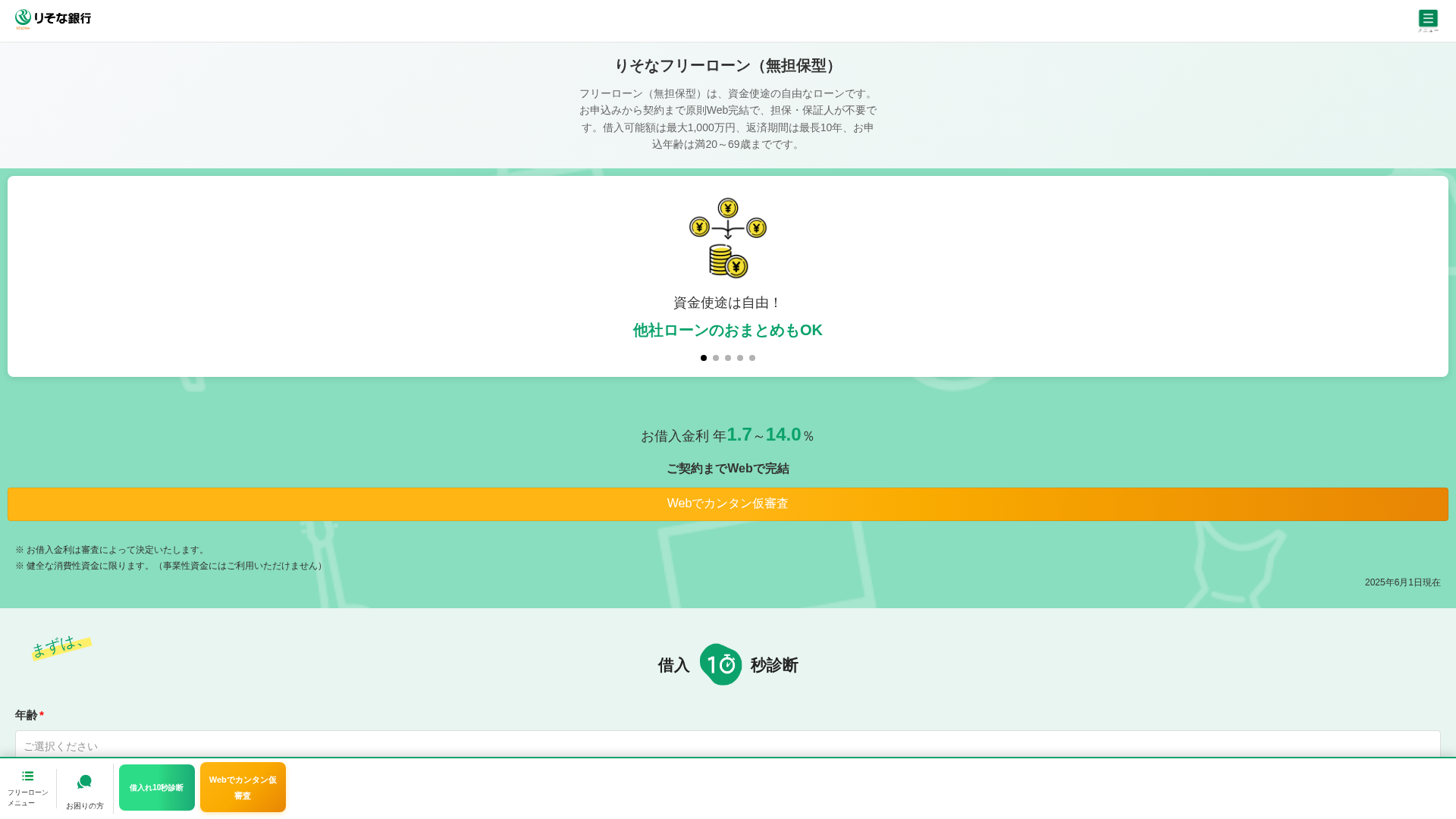
Phishing Analysis
Detailed analysis of captured phishing page
70
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: りそな銀行 (Resona Bank)
- • Threat: Phishing targeting bank customers
- • Target: Resona Bank customers
- • Method: Fake website with a login form is used to steal user credentials
- • Exfil: Credentials likely sent to a malicious server
- • Indicators: Domain registered 1 day ago, mismatched domain from legitimate bank, form requesting information
- • Risk: HIGH - immediate risk of credential theft
⚠ Risk Factors
- Brand impersonation of りそな銀行 (Resona Bank) on non-official domain
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
No screenshot available
Detection Info
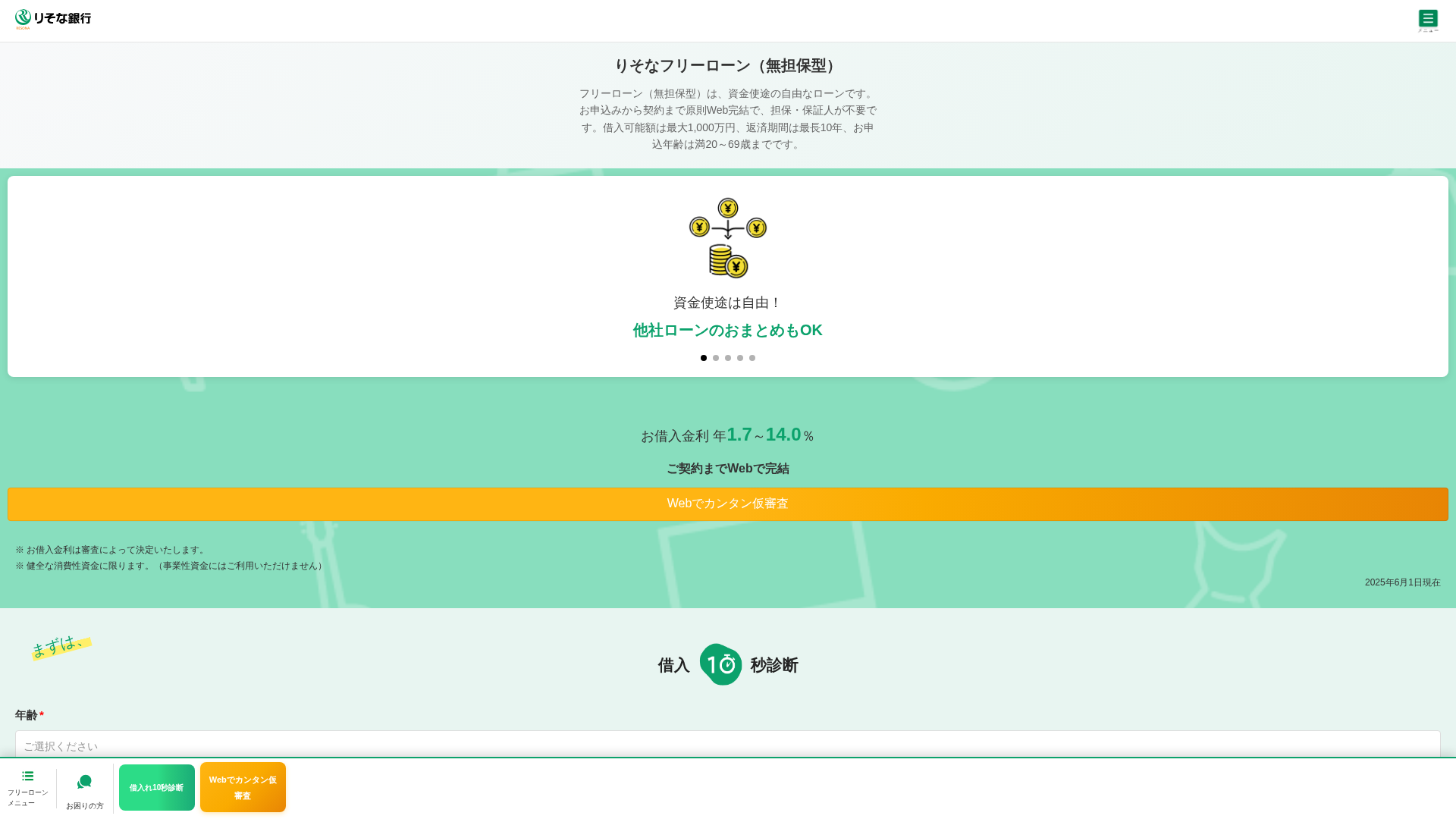
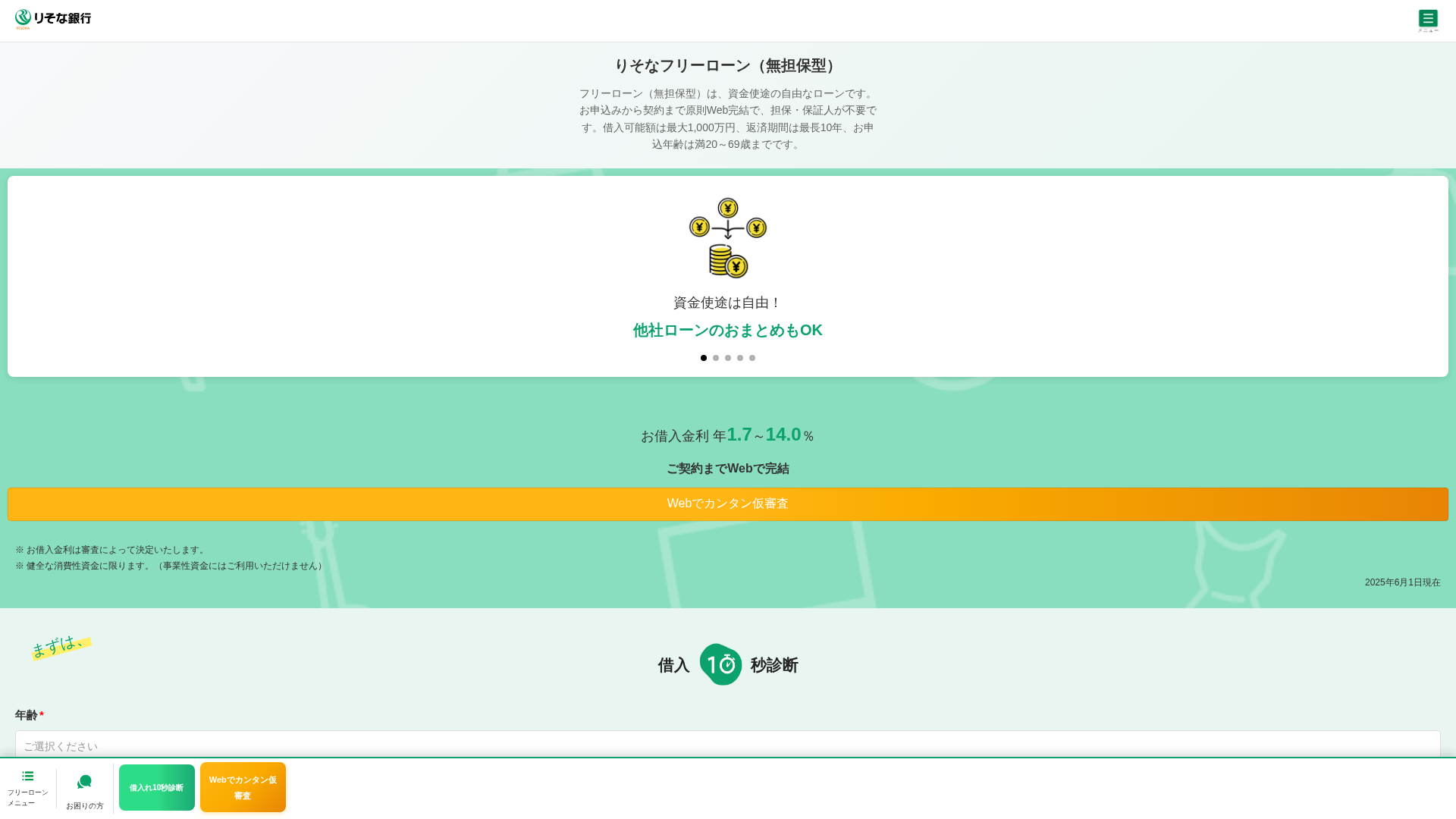
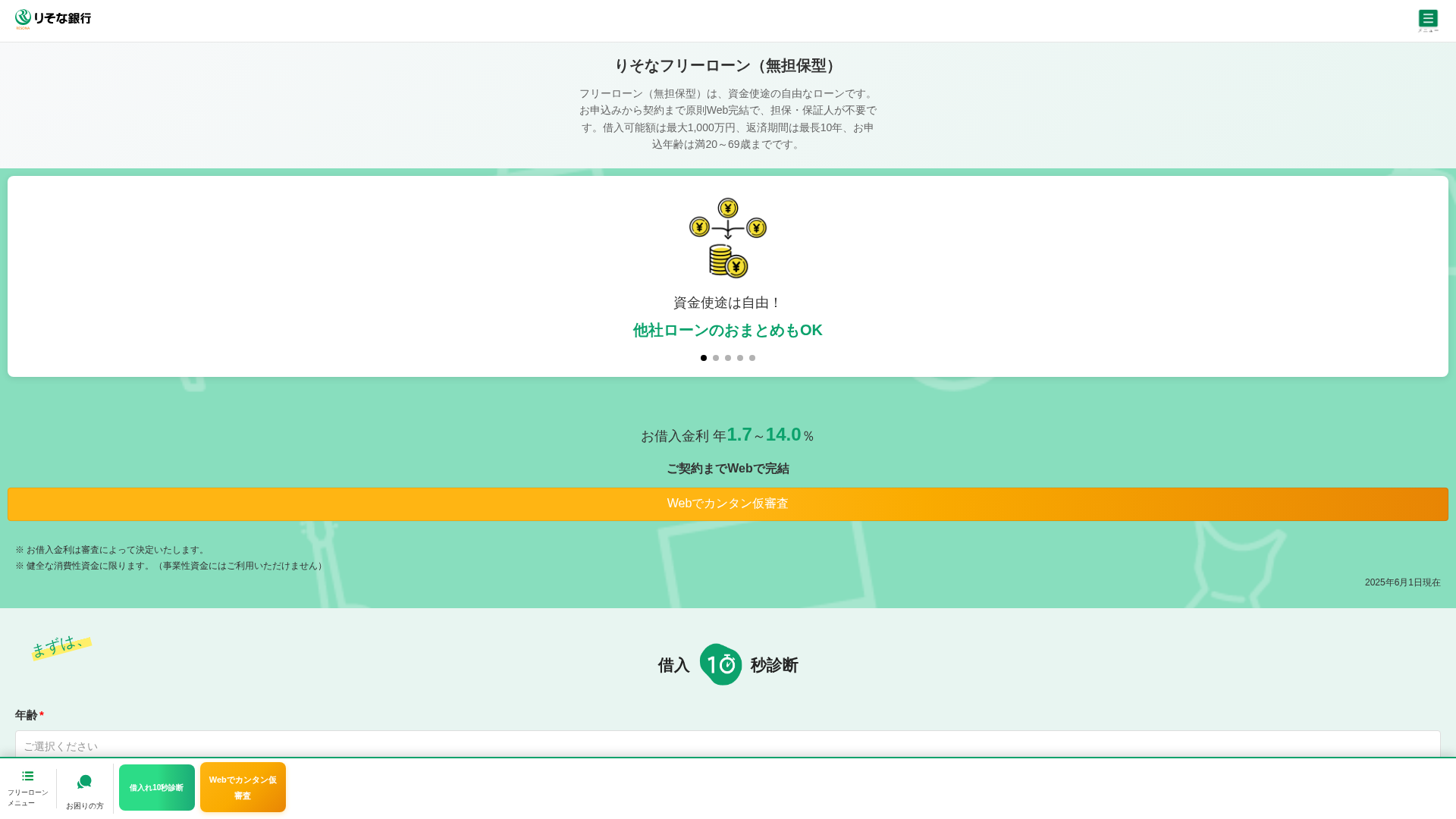
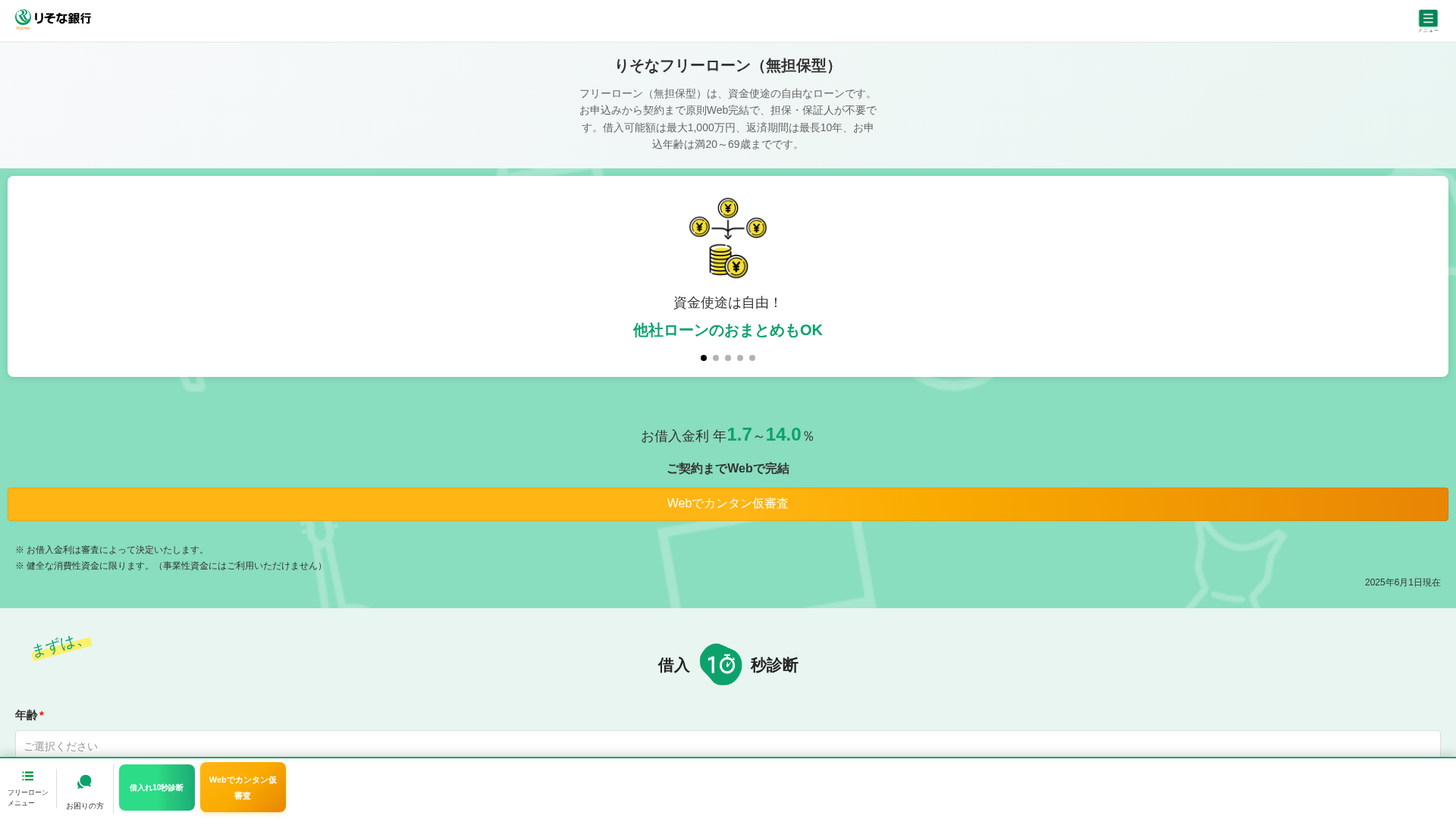
https://bankdgop.top/
Detected Brand
りそな銀行 (Resona Bank)
Country
Japan
Confidence
99%
HTTP Status
200
Report ID
f0d81a9e-eff…
Analyzed
2025-12-23 11:04
Final URL (after redirects)
https://bankdgop.top/#/
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T15F925D6871073D5B543386D0F4D96F0E709BE335E2054518A3AEA2AE7FCECF19826369 |
|
CONTENT
ssdeep
|
192:HeEKsUbDgSwrDQ2PNkCJb/NxTA6mA6aA62q6ydJVvEN2YNqyTzhBeC3D:dDQ4NnLx1UQzdJVCtTzhBeC3D |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
a7f087780ff08d70 |
|
VISUAL
aHash
|
ffffffff0000ff3f |
|
VISUAL
dHash
|
8c0c088c08d28e40 |
|
VISUAL
wHash
|
f7e7ff000000673f |
|
VISUAL
colorHash
|
07030008000 |
|
VISUAL
cropResistant
|
8c0c088c08d28e40 |
Code Analysis
Risk Score
70/100
Threat Level
ALTO
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Banking
🎣 Personal Info
🔬 Threat Analysis Report
• Threat: Phishing targeting bank customers
• Target: Resona Bank customers
• Method: Fake website with a login form is used to steal user credentials
• Exfil: Credentials likely sent to a malicious server
• Indicators: Domain registered 1 day ago, mismatched domain from legitimate bank, form requesting information
• Risk: HIGH - immediate risk of credential theft
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
Scan History for bankdgop.top
Found 2 other scans for this domain