
Phishing Analysis
Detailed analysis of captured phishing page
70
Risk Score
High Risk
Threat Level: CRITICAL
• Impersonating: BELECTRIC
- • Threat: Credential harvesting phishing
- • Target: BELECTRIC users
- • Method: Fake login page attempting to steal credentials
- • Exfil: Unknown - likely to a server controlled by the attacker
- • Indicators: Domain does not match the official brand, login form present
- • Risk: HIGH - Risk of stolen credentials being used for malicious purposes
⚠ Risk Factors
- Brand impersonation of BELECTRIC on non-official domain
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
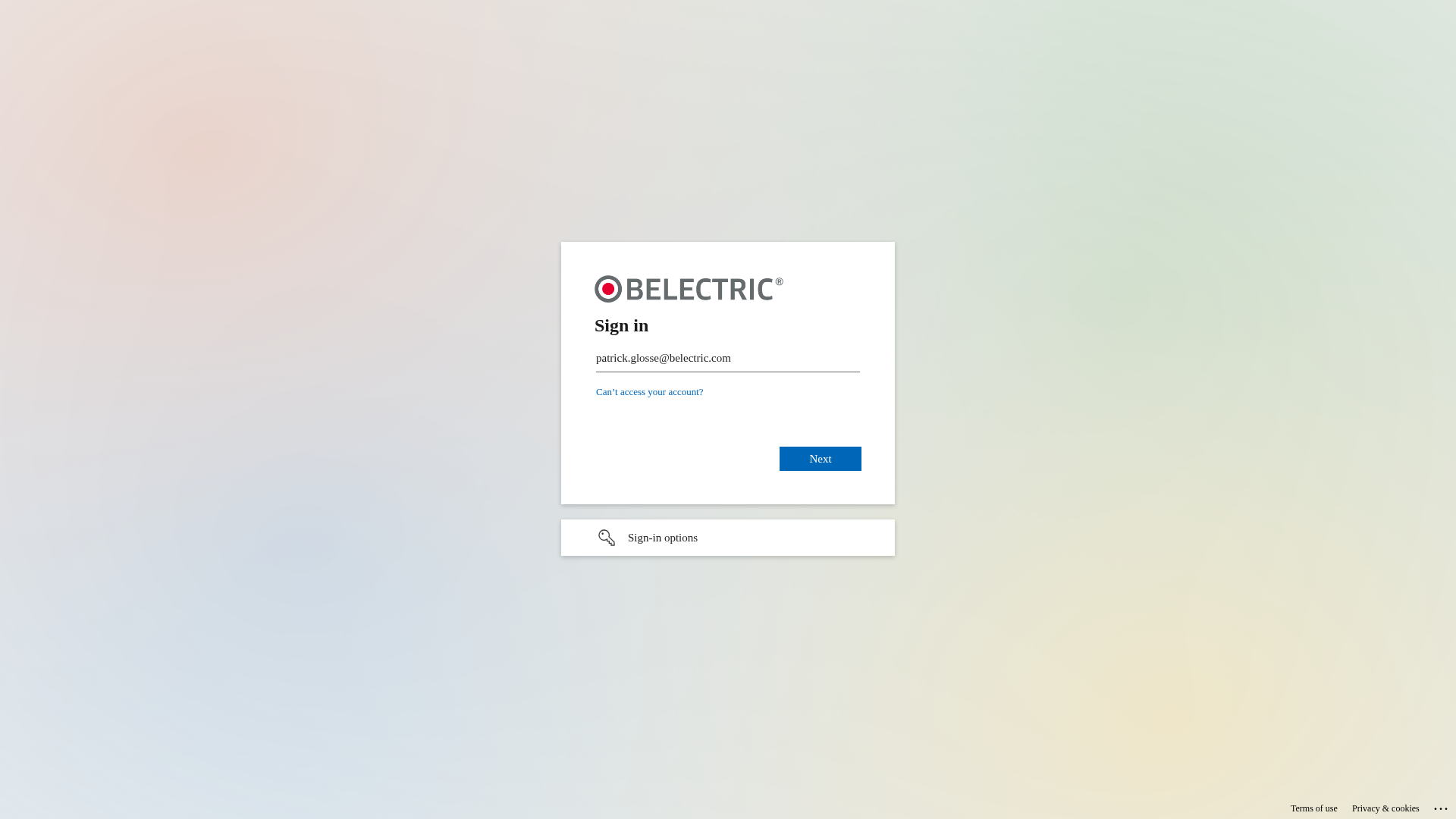
Detection Info
https://sso-auth.com/wqdQnTL9BHQ8Zg?/g/personal/patrick_glosse_belectric_com/ETvMuE2HPLpPgskR0RfHG0sBk3kf43GwtcnE26u0vW301g?e=rF2mfd
Detected Brand
BELECTRIC
Country
International
Confidence
100%
HTTP Status
200
Report ID
f23af94b-dae…
Analyzed
2025-12-24 19:28
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T1DBD1E07050509D3B5283C7D4B3B96B9F3794C346EA97565A63F8C39C0EE3E26CC1A226 |
|
CONTENT
ssdeep
|
96:nIpkCGTHRPy3krwkMAs39TbJG9KjsWsjORaX0U2gs0sjORaiOVJQ6Q6ynQjNsjOE:9kk859TbJG9a8FQiOVJQyyQj8D |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
9c4b7326cc99d964 |
|
VISUAL
aHash
|
18001818191f0f9f |
|
VISUAL
dHash
|
7161713331727d38 |
|
VISUAL
wHash
|
191818181f1f1fff |
Code Analysis
Risk Score
70/100
Threat Level
CRITICAL
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Personal Info
🔬 Threat Analysis Report
• Threat: Credential harvesting phishing
• Target: BELECTRIC users
• Method: Fake login page attempting to steal credentials
• Exfil: Unknown - likely to a server controlled by the attacker
• Indicators: Domain does not match the official brand, login form present
• Risk: HIGH - Risk of stolen credentials being used for malicious purposes
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
No screenshot
Belectric
https://sso-security.com/mwNw9yK7zSMRZa4?=userid&messageid=Y...
Jan 07, 2026
Lufthansa Group
https://auth-secure.me/uevS-wCLOtUaMg
Jan 05, 2026

Lufthansa Group
https://auth-secure.me/uevS-wCLOtUaMg
Jan 05, 2026
BELECTRIC
https://sso-security.com/yDggbRnMeqV36P0?=userid&messageid=Y...
Jan 02, 2026
Belectric
https://sso-security.com/1NUTBtgmCwX39x8?=userid&messageid=Y...
Dec 24, 2025
Scan History for sso-auth.com
Found 10 other scans for this domain
-
https://sso-auth.com/aZOdHyJ6ngsBheSA?/facebook_se...
https://sso-auth.com/28jOsuzCXkrq?/facebook_secure...
https://sso-auth.com/cbJQq-8SxdE?/edwalina-bueno/s...
https://sso-auth.com/IoVTp4ZEW3oOJw?/facebook_secu...
https://sso-auth.com/_E1vv_uLKtMe?/facebook_secure...
https://sso-auth.com/C21pjma05edvW2SPsw?/facebook_...
https://sso-auth.com/WRkqw2X3HU4?/facebook_secure_...
https://sso-auth.com/5tsXksyXetV8W940?/g/personal/...
https://sso-auth.com/pjbejpaz-KfW-M8?/facebook_sec...
https://sso-auth.com/IjX5r9t7egV1YaU?/facebook_sec...