
Phishing Analysis
Detailed analysis of captured phishing page
79
Risk Score
High Risk
Threat Level: ALTO
• Impersonating: TronLink
- • Threat: Credential harvesting phishing kit
- • Target: TronLink users internationally
- • Method: Fake login form stealing user credentials
- • Exfil: Data sent to unknown server
- • Indicators: Domain mismatch, obfuscated JavaScript, forms present
- • Risk: HIGH - Immediate credential theft
⚠ Risk Factors
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
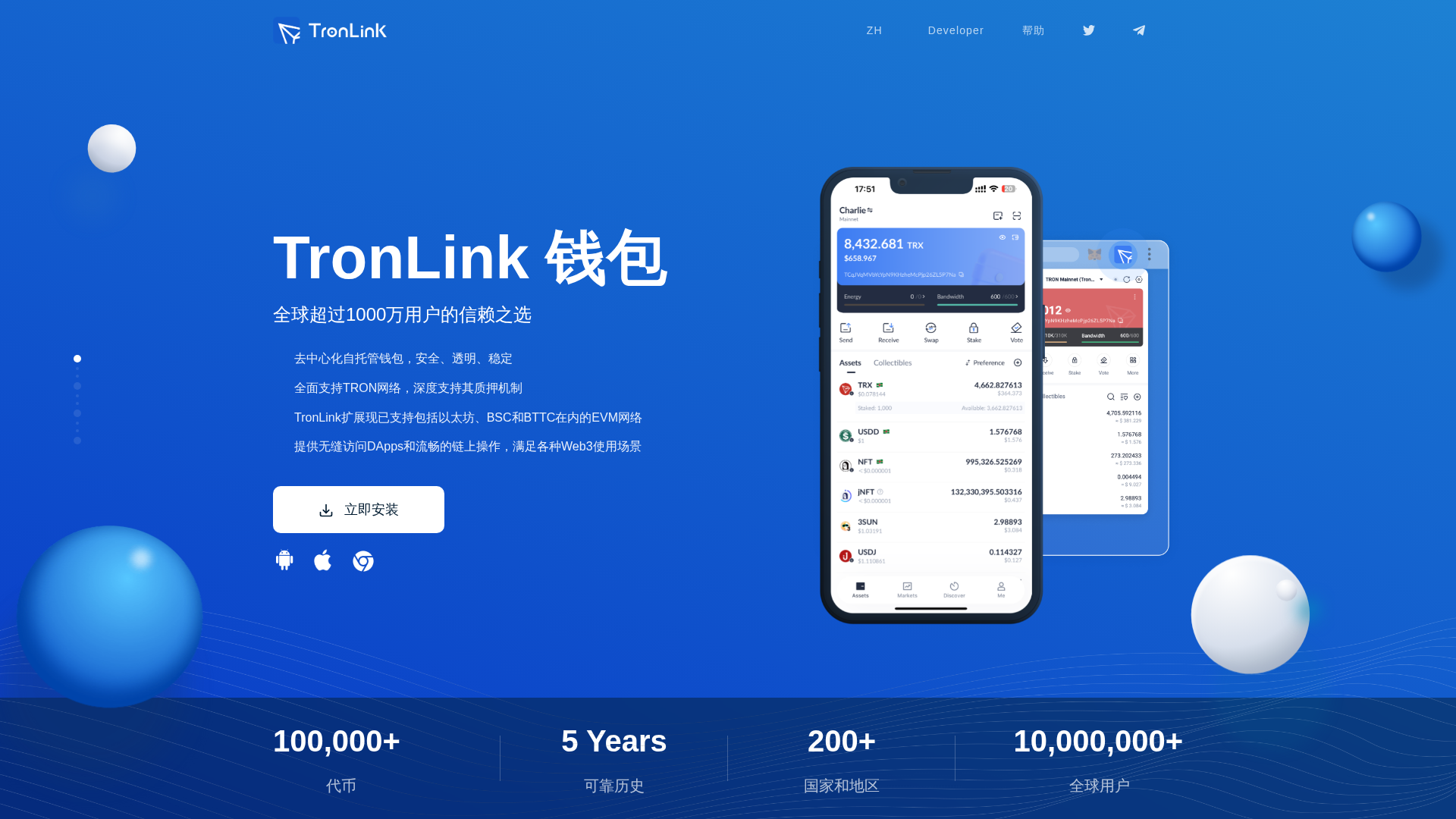
Detection Info
https://tronlink2026.com/
Detected Brand
TronLink
Country
International
Confidence
100%
HTTP Status
200
Report ID
f5a513b6-095…
Analyzed
2026-01-11 06:16
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T1F1C27172D251F863015383D1F339276EF792804ED8A34B4267F9838D9B89D96FD0286E |
|
CONTENT
ssdeep
|
384:jWKO166SY0jBi8RIFzgDxyngvIKFIZ3SDnZINPlax1CfR:JeIIF8DxwEeBQZINdI1CfR |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
92ce6db3122dc3c6 |
|
VISUAL
aHash
|
030d3e0e6eef0200 |
|
VISUAL
dHash
|
d739eccccc583ad4 |
|
VISUAL
wHash
|
0f8f7f2e6ecf0200 |
|
VISUAL
colorHash
|
000000001c0 |
|
VISUAL
cropResistant
|
337c7686c4c4c2b3,3913c6e6f7e75959,a280a286a6b280a2,f0f8f8f0f0f0f0f0,70e0c2a0a080c070,d739eccccc583ad4 |
Code Analysis
Risk Score
79/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Banking
🔬 Threat Analysis Report
• Threat: Credential harvesting phishing kit
• Target: TronLink users internationally
• Method: Fake login form stealing user credentials
• Exfil: Data sent to unknown server
• Indicators: Domain mismatch, obfuscated JavaScript, forms present
• Risk: HIGH - Immediate credential theft
🔒 Obfuscation Detected
- fromCharCode
- document.write
- base64_strings
Similar Websites
Pages with identical visual appearance (based on perceptual hash)