
Phishing Analysis
Detailed analysis of captured phishing page
16
Risk Score
Low Risk
Threat Level: MEDIO
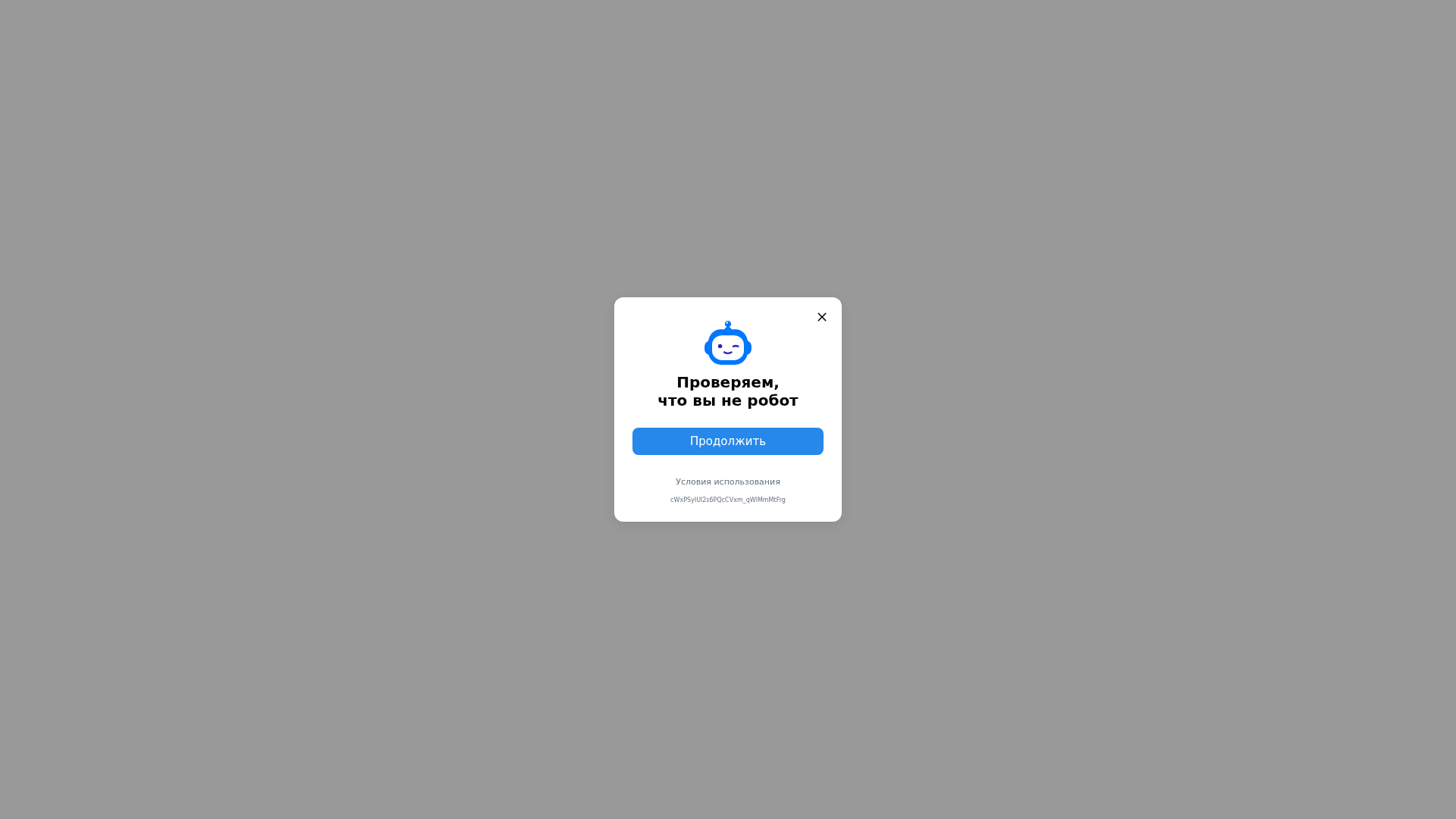
• Impersonating: VK
- • Threat: Captcha bypass attempt with potential data collection.
- • Target: VK (VKontakte) users.
- • Method: Displaying a fake 'are you a robot' check to potentially harvest data or bypass security measures.
- • Exfil: Unknown, but likely involves data exfiltration through obfuscated Javascript.
- • Indicators: Uncharacteristic subdomain, obfuscated Javascript using fromCharCode and unescape, the presence of an unusual hash at the bottom of the popup.
- • Risk: MEDIUM - Data collection or account compromise if bypassed.
Visual Capture
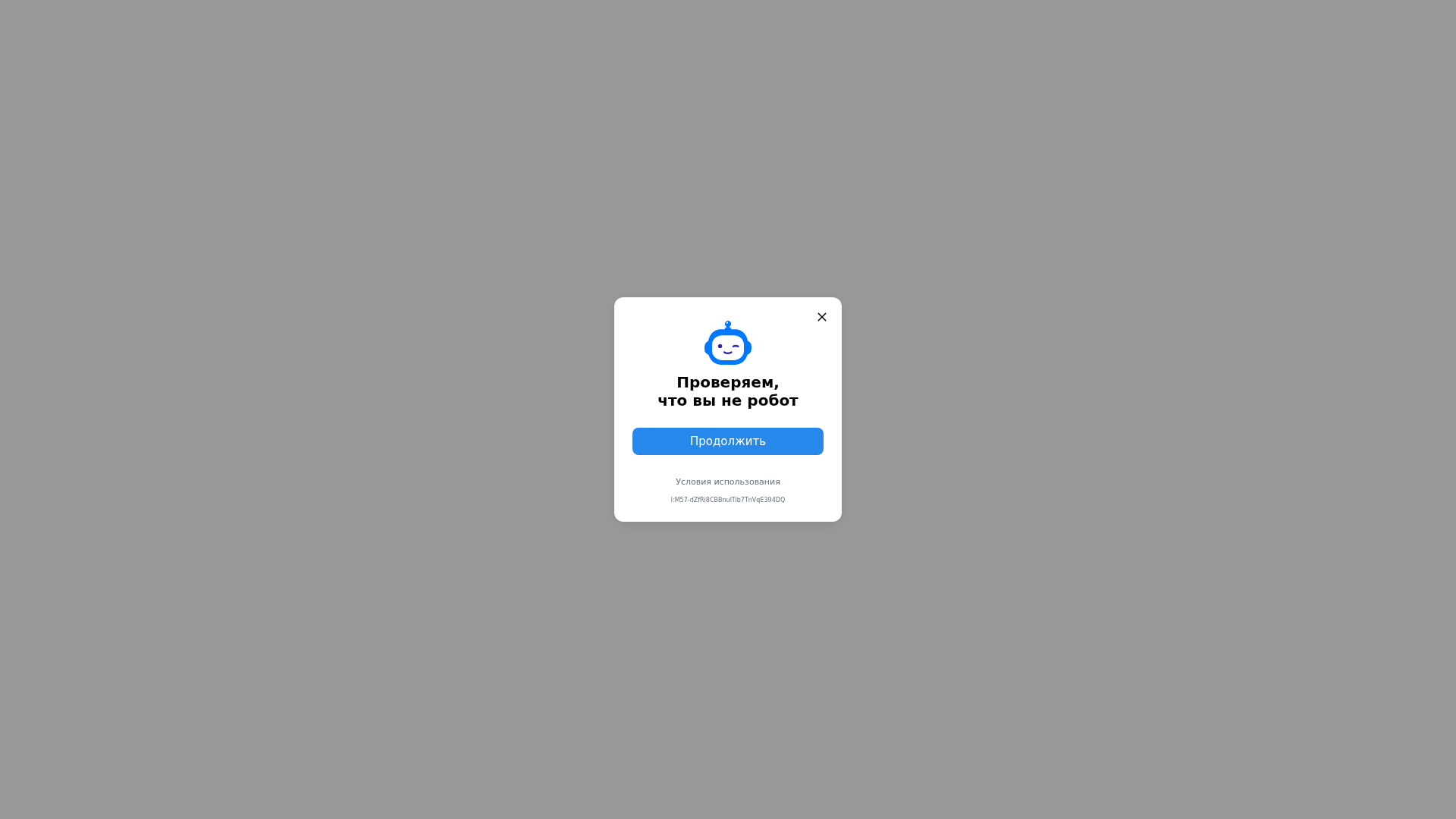
Detection Info
https://976tep2sg8.vk.com/challenge.html?tid=l:M57-dZfRi8CBBnulTib7TnVqE394DQ&hash429=9RR_4HWtQ3iViPjQYwfk88pNxdqHsooHdDP7hlT9pPa_1TCgdjkallgN7Qy2SMPlHltZE1B9m7Me1FfLApkh4-a9g8dL12Et1cOnedjNaC9LZTA6rxygLmrxSlOgKIu9KloF2ODLPZ5RH9FI&redirect=/away.php%3Fto=https%253A%252F%252Fviewmyprofile-activateinfo.es%252Fde&back=&sign=LfU7_g0qaMTAFJd3BguFlg&origin=&lang_id=
Detected Brand
VK
Country
International
Confidence
99%
HTTP Status
200
Report ID
f96dd279-990…
Analyzed
2026-01-05 23:08
Final URL (after redirects)
https://976tep2sg8.vk.com/challenge.html?tid=l:M57-dZfRi8CBBnulTib7TnVqE394DQ&hash429=SdCSixLxEiT3gk_yIJpeFsHhdDuYnfuLlCDntwVEWrZxzqfFAopLspDbfqHUjPeNhlB3UbftQqDx_gN8uXNkEUzEepOf8_KfdqKLK0j4heVUFeA2xSnqLYdXpVkw70RfsAZ3BmSiuTrCR_kv&redirect=/away.php%3Fto=https%253A%252F%252Fviewmyprofile-activateinfo.es%252Fde&back=&sign=fmoAI7H5WNgoJfOxXoBoxw&origin=&lang_id=
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T1DCD183E8AA3CB63D140F87ACCB6EF681235FA0EDF3170564638E56B10587E6CE946C54 |
|
CONTENT
ssdeep
|
96:e35KFSe0BlTSc/Q04JvN/Un4jFSe0BlTSc/Q04JWatPTOYuFA9ed/WqtuC:ZAN3J4JvBAN3J4J/iVW9eJW4uC |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
cccc3333cccc6633 |
|
VISUAL
aHash
|
0000181818180000 |
|
VISUAL
dHash
|
100c32b2b2320c10 |
|
VISUAL
wHash
|
3c3c3c3c1c1c3030 |
|
VISUAL
colorHash
|
070000001c0 |
|
VISUAL
cropResistant
|
100c32b2b2320c10 |
Code Analysis
Risk Score
16/100
Threat Level
MEDIO
⚠️ Phishing Confirmed
🔬 Threat Analysis Report
• Threat: Captcha bypass attempt with potential data collection.
• Target: VK (VKontakte) users.
• Method: Displaying a fake 'are you a robot' check to potentially harvest data or bypass security measures.
• Exfil: Unknown, but likely involves data exfiltration through obfuscated Javascript.
• Indicators: Uncharacteristic subdomain, obfuscated Javascript using fromCharCode and unescape, the presence of an unusual hash at the bottom of the popup.
• Risk: MEDIUM - Data collection or account compromise if bypassed.
🔒 Obfuscation Detected
- fromCharCode
- unescape
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
VK
https://away.vk.com/away.php?rh=cfd366b6-171c-4507-8de7-2c09...
Jan 06, 2026
VK
https://away.vk.com/away.php?rh=ed5bc5bb-a7ba-499f-9689-ef26...
Jan 06, 2026
VK
https://976tep2sg8.vk.com/challenge.html?tid=l:KaVaYQfOJDTUt...
Jan 06, 2026
No screenshot
Unknown
https://976tep2sg8.vk.com/challenge.html?tid=l:6uMgaKKwwETt6...
Jan 06, 2026
VK
https://away.vk.com/away.php?rh=54635185-f7f2-4aa4-84f1-46c5...
Jan 06, 2026
Scan History for 976tep2sg8.vk.com
Found 10 other scans for this domain
-
https://976tep2sg8.vk.com/challenge.html?tid=l:WY7...
https://976tep2sg8.vk.com/challenge.html?tid=l:ZkO...
https://976tep2sg8.vk.com/challenge.html?tid=l:Mii...
https://976tep2sg8.vk.com/challenge.html?tid=l:KaV...
https://976tep2sg8.vk.com/challenge.html?tid=l:6uM...
https://976tep2sg8.vk.com/challenge.html?tid=l:DAE...
https://976tep2sg8.vk.com/challenge.html?tid=l:kJj...
https://976tep2sg8.vk.com/challenge.html?tid=l:8PX...
https://976tep2sg8.vk.com/challenge.html?tid=l:R2S...
https://976tep2sg8.vk.com/challenge.html?tid=l:o9Z...