Phishing Analysis
Detailed analysis of captured phishing page
95
Risk Score
High Risk
Threat Level: ALTO
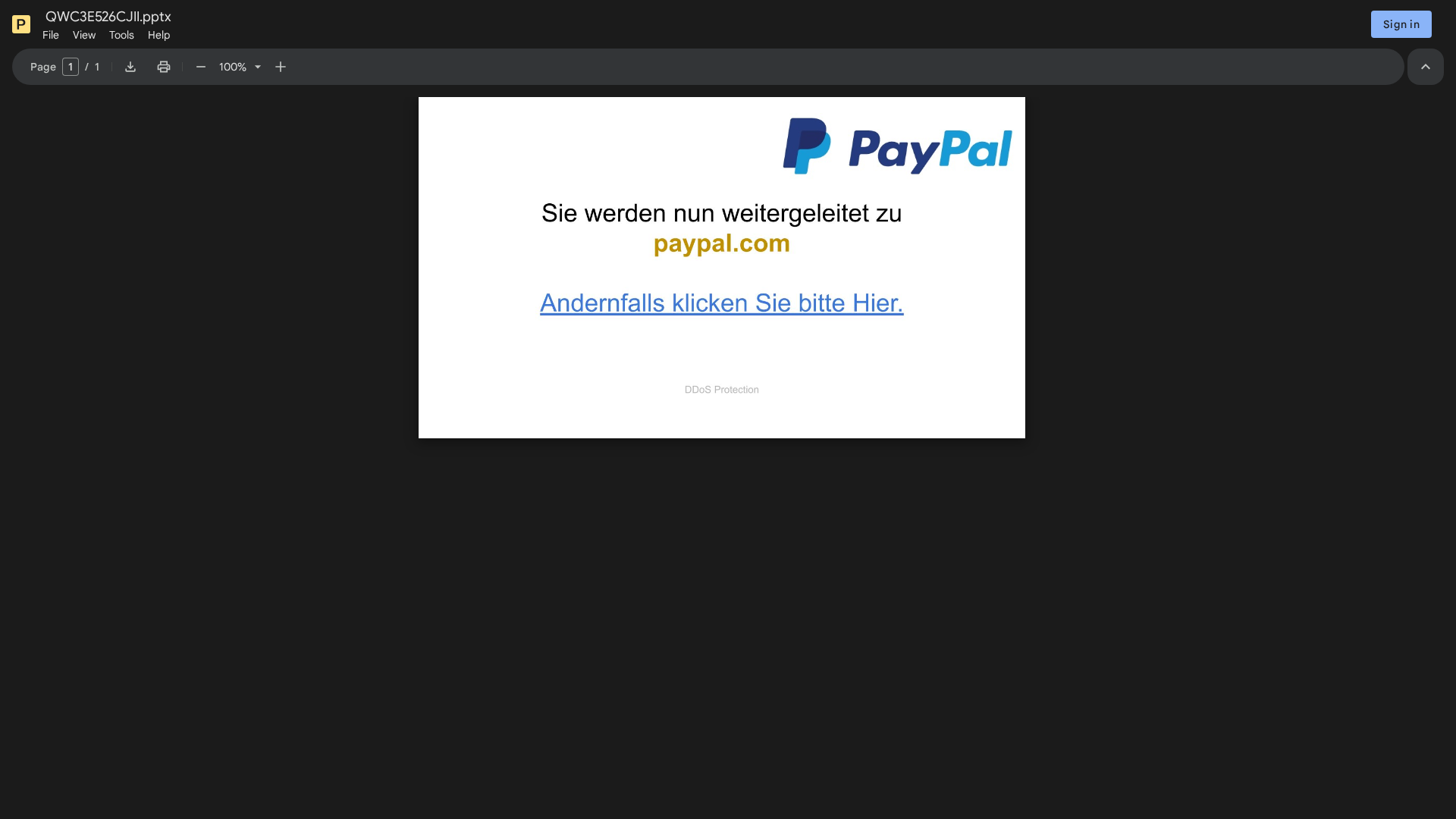
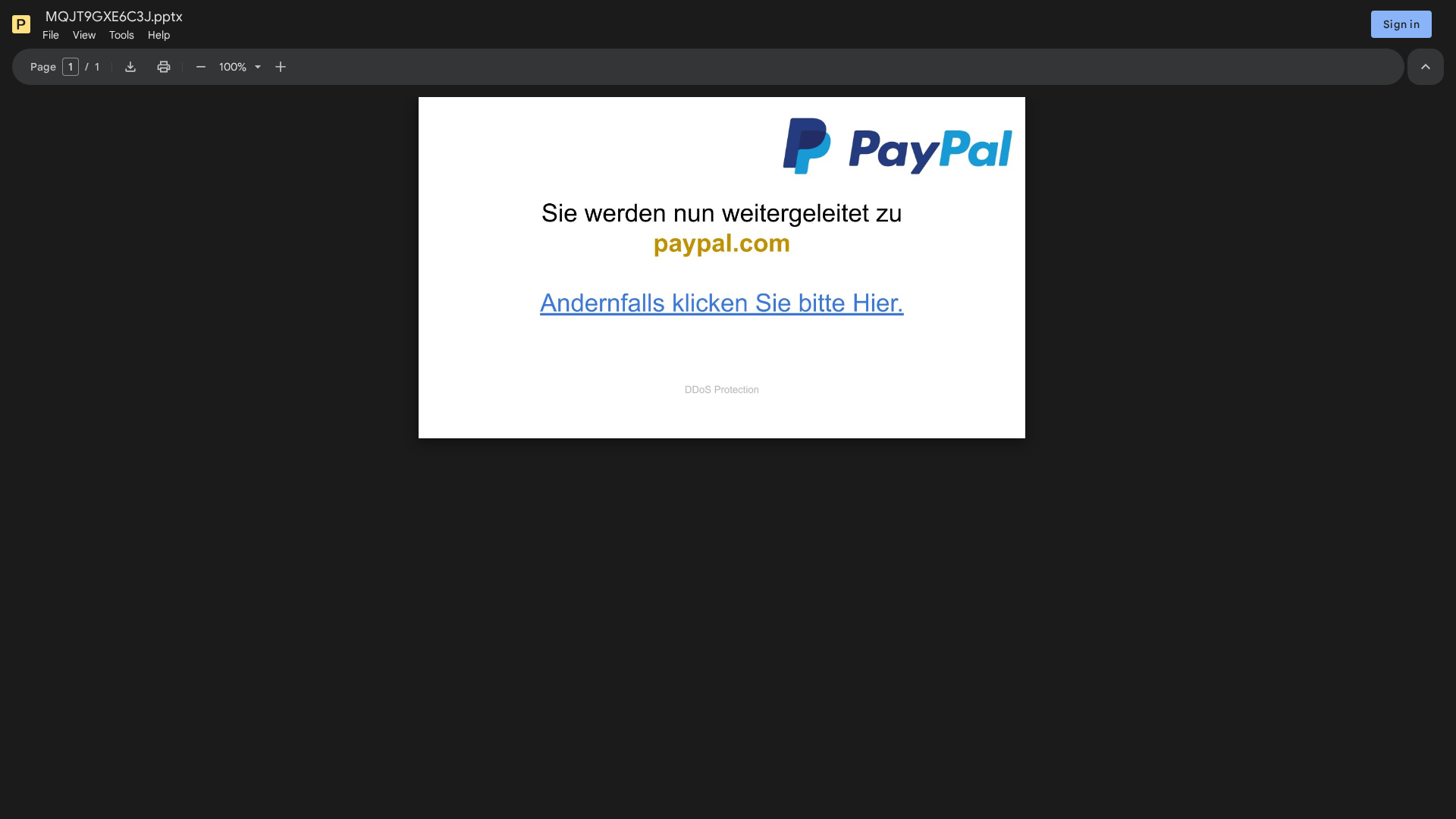
• Impersonating: PayPal
⚠ Risk Factors
- Brand impersonation of PayPal on non-official domain
- JavaScript obfuscation detected (8 patterns)
- Credential harvesting indicators detected
- OTP/2FA stealing indicators detected
Visual Capture
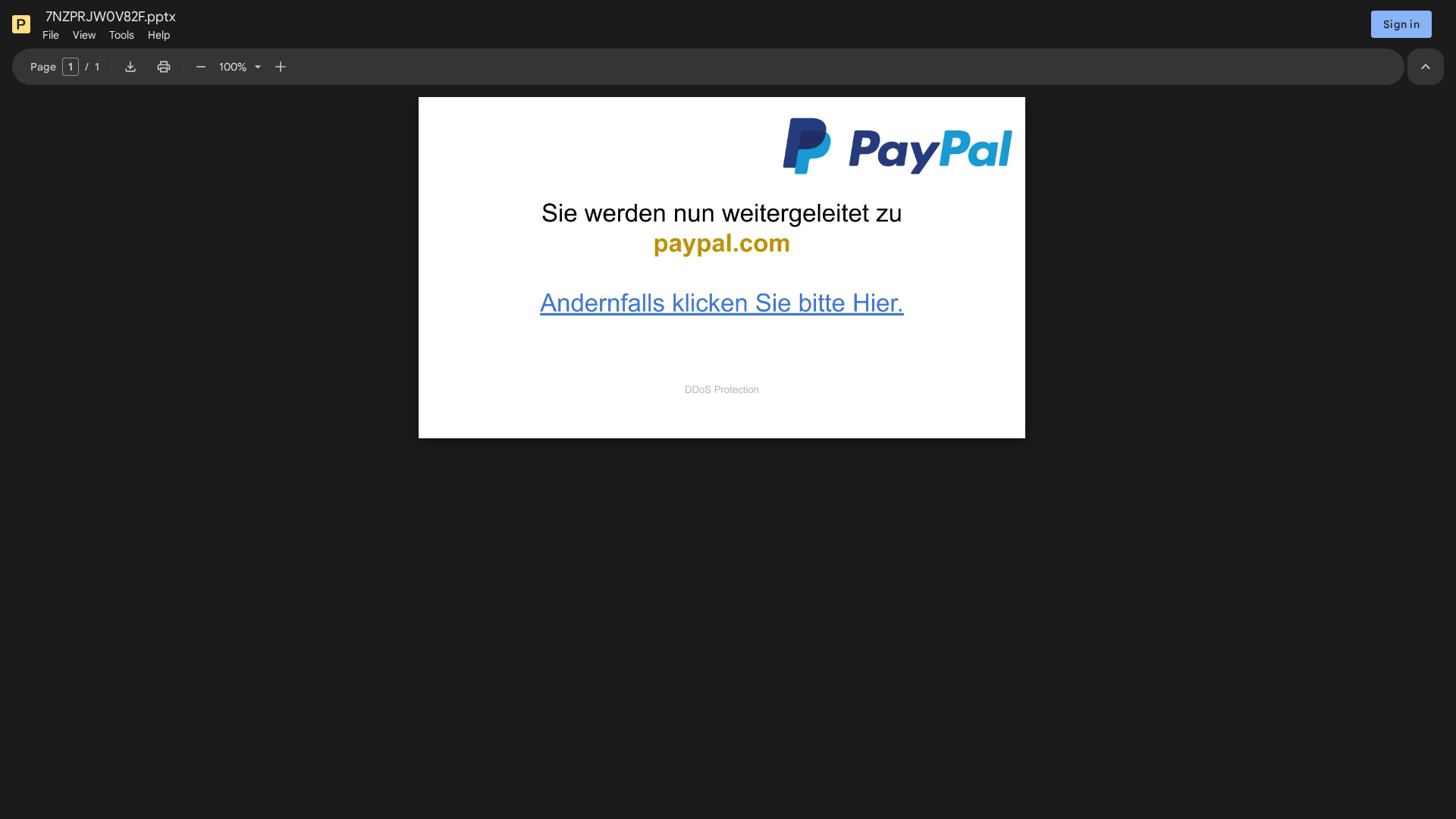
Detection Info
https://drive.google.com/file/d/19zPw90jGON3J5mERXi1pauVKjDMx8NFQ/edit
Detected Brand
PayPal
Country
Unknown
Confidence
100%
HTTP Status
200
Report ID
fbe57f4a-ebb…
Analyzed
2026-01-09 23:12
Content Hashes (HTML Similarity)
Used to detect similar phishing pages based on HTML content
| Algorithm | Hash Value |
|---|---|
|
CONTENT
TLSH
|
T1C3938662B0537937025775C6B96DB75E72E3C31DD40B00324BBCA3B81BDADA1BA0B646 |
|
CONTENT
ssdeep
|
1536:KJ7OWv3IqgytKfZ9xEkQQoI1PKeQ0erSeIDepueyqeyWee4U5g16EKGKHCkXKNMH:K1EB5WQURapzX |
Visual Hashes (Screenshot Similarity)
Used to detect visually similar phishing pages based on screenshots
| Algorithm | Hash Value |
|---|---|
|
VISUAL
pHash
|
cfcf343031bb3131 |
|
VISUAL
aHash
|
003c3c3c3c000000 |
|
VISUAL
dHash
|
6161696969866000 |
|
VISUAL
wHash
|
ff3c3c3c3c000000 |
|
VISUAL
colorHash
|
310030000c0 |
|
VISUAL
cropResistant
|
9681368f1b338088,6161696969866000 |
Code Analysis
Risk Score
95/100
Threat Level
ALTO
⚠️ Phishing Confirmed
🎣 Credential Harvester
🎣 OTP Stealer
🎣 Card Stealer
🎣 Banking
🎣 Personal Info
🔒 Obfuscation Detected
- atob
- eval
- fromCharCode
- unescape
- document.write
- hex_escape
- unicode_escape
- base64_strings
Similar Websites
Pages with identical visual appearance (based on perceptual hash)
Scan History for drive.google.com
Found 6 other scans for this domain
-
https://drive.google.com/file/d/1C5O9_Y8_OcTSEPwyO...
https://drive.google.com/file/d/1GINBNlpVt7kpfNog9...
https://drive.google.com/file/d/1robIOsANBh8Doqa7Y...
https://drive.google.com/file/d/1EK-X4KsZazaqsluaT...
https://drive.google.com/file/d/1kewJar93TWUKK9QEj...
https://drive.google.com/file/d/1229Fd7PsxEeWtt_ct...